Key protection module
A key protection and key technology, applied in key distribution, can solve the problems of undecryptable communication information, no hardware storage location, loss of private key, etc., to achieve the effect of protecting keys, simple modules, and improving utilization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
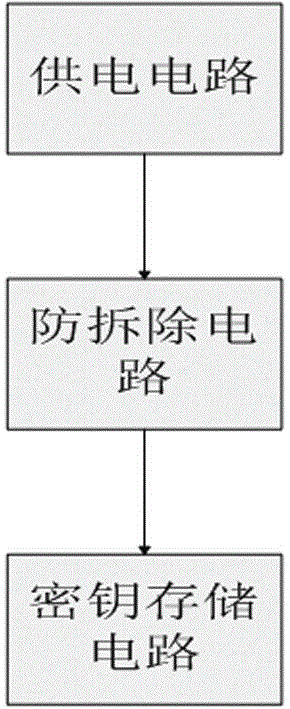
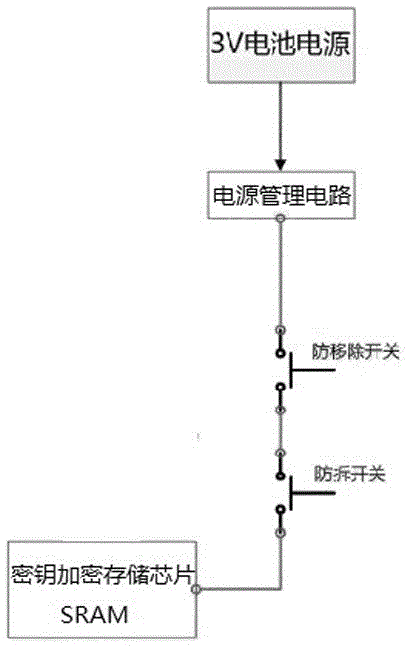
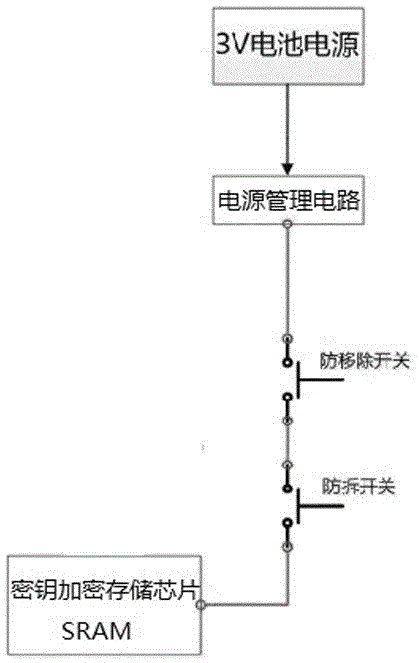
[0013] Such as figure 1 and figure 2 As shown, a key protection module includes: a key storage circuit, which stores the key information sent by the front-end circuit; an anti-demolition circuit, which detects that the key storage circuit moves and automatically erases the key information in the key storage circuit ; An external power supply to supply power to the key storage circuit. The invention utilizes an external power supply to directly supply power to the key storage circuit, and the key information is stored in the key protection circuit, so that the key information will not be lost even if the system is accidentally powered off. However, since the external power supply is used to directly supply power to the module, the external power supply needs to match the operating voltage of the circuit. When the external power supply voltage does not match the operating voltage of the circuit, the key protection module cannot work, and the module has a narrow application ran...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com