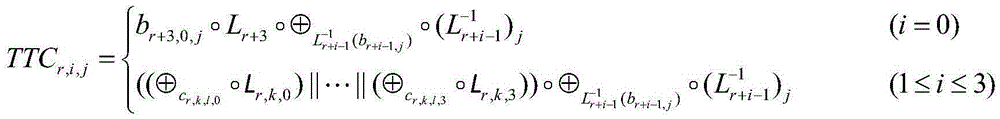Security white box realizing method and device for national cipher standard algorithm SM4
A technology of cryptographic algorithm and implementation method, applied in the field of protection of cryptographic components in digital property rights system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The specific embodiments and features of the present invention will be described in detail below, but the scope of the present invention is not limited in any way.
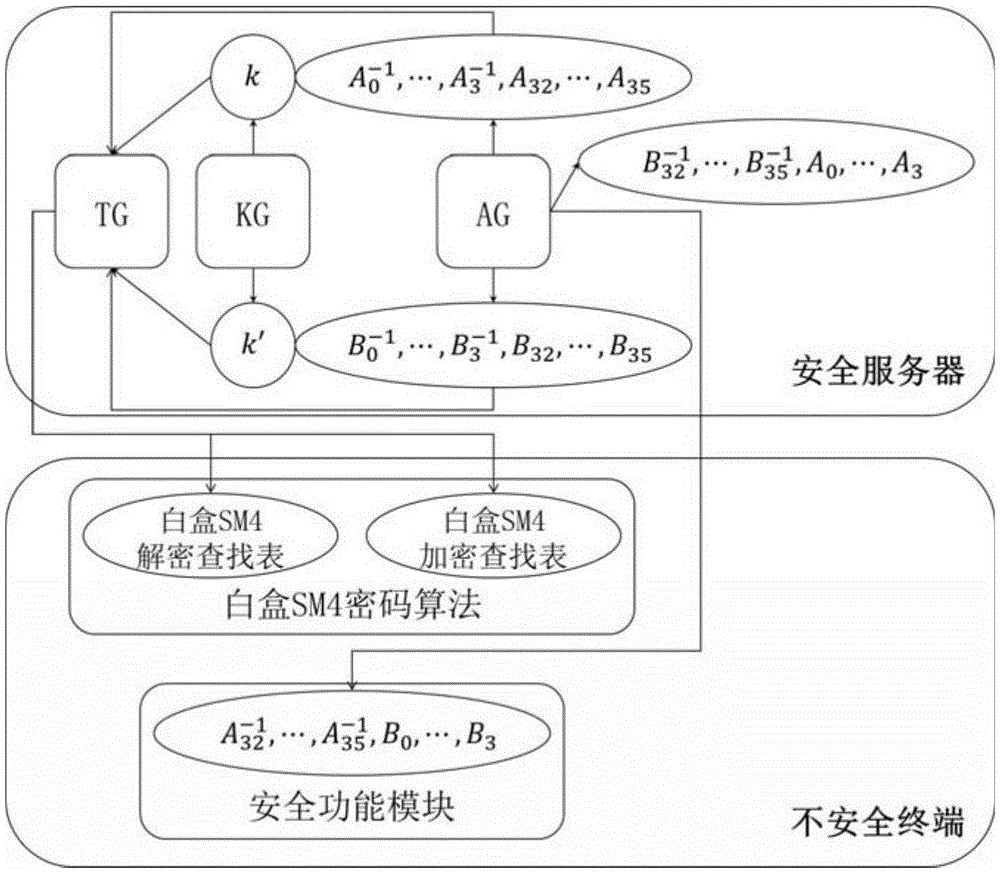
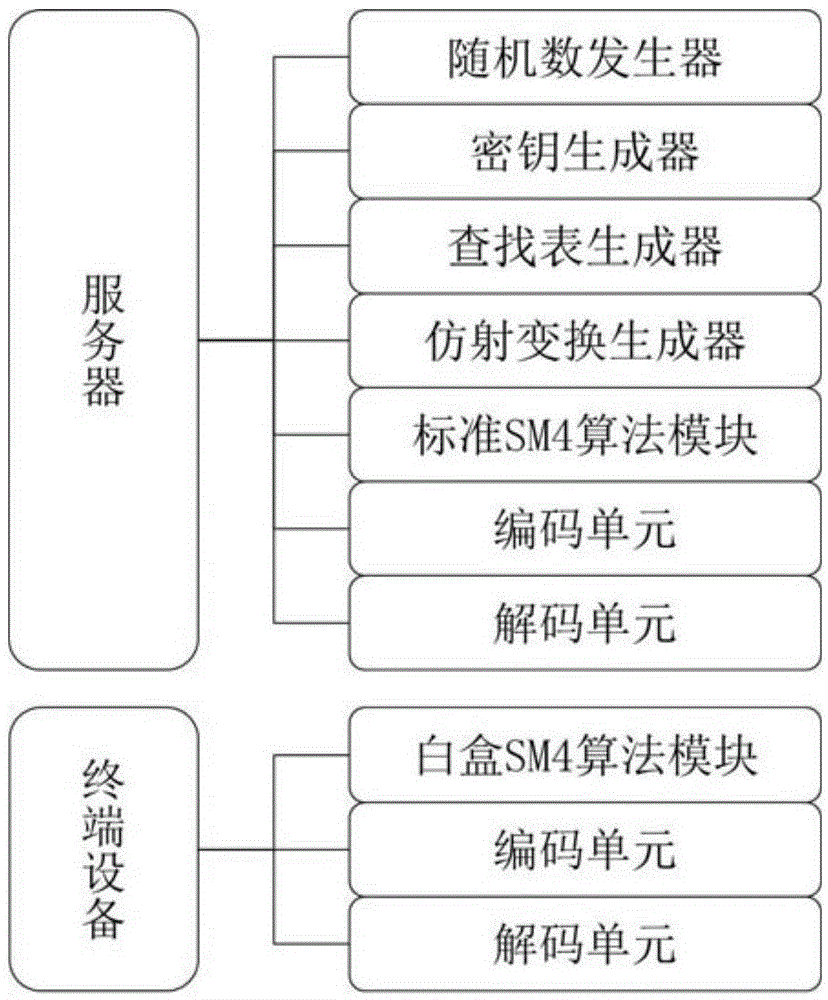
[0039] Such as figure 1 As shown, on the secure server side, there are three components: Lookup Table Generator (TG), Key Generator (KG), and Affine Transformation Generator (AG).
[0040] For each device (unsafe terminal), the AG of the server randomly generates 8 pairs of 32-bit reversible affine transformation A 32 , A 33 , A 34 , A 35 , B 0 , B 1 , B 2 , B 3 , and will B 0 ,B1 ,B 2 ,B 3 Bundled with the device's security feature modules (such as video player, music player, e-book reader, etc.). The device should also install the white box SM4 cryptographic algorithm module. The device is then ready for use by the user. Here, the 32-bit random reversible affine transformation can be generated according to device-related unique identifiers such as device MAC address and user...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com