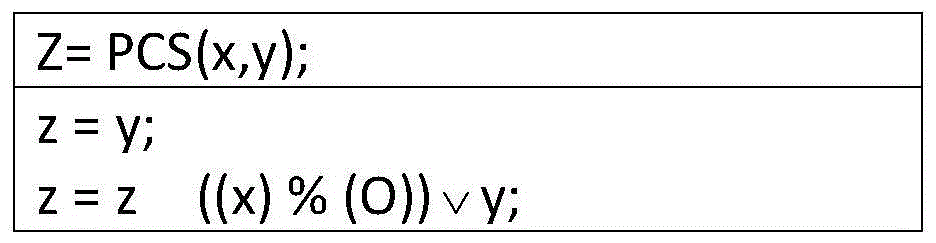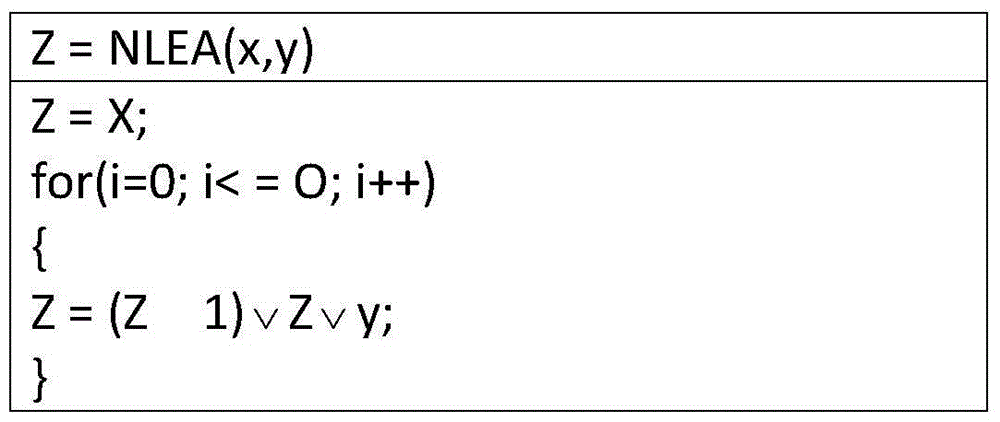Group RFID tag identity authentication method
An RFID tag and identity authentication technology, applied in user identity/authority verification, induction record carrier, transmission system, etc., can solve the problem of unsafe wireless channels between readers and tags, and RFID identity authentication protocols that are difficult to meet safety, efficiency, and low cost requirements , safety hazards and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] The following will clearly and completely describe the technical solutions in the embodiments of the present invention with reference to the accompanying drawings in the embodiments of the present invention. Obviously, the described embodiments are only some, not all, embodiments of the present invention. Based on the embodiments of the present invention, all other embodiments obtained by persons of ordinary skill in the art without creative efforts fall within the protection scope of the present invention.
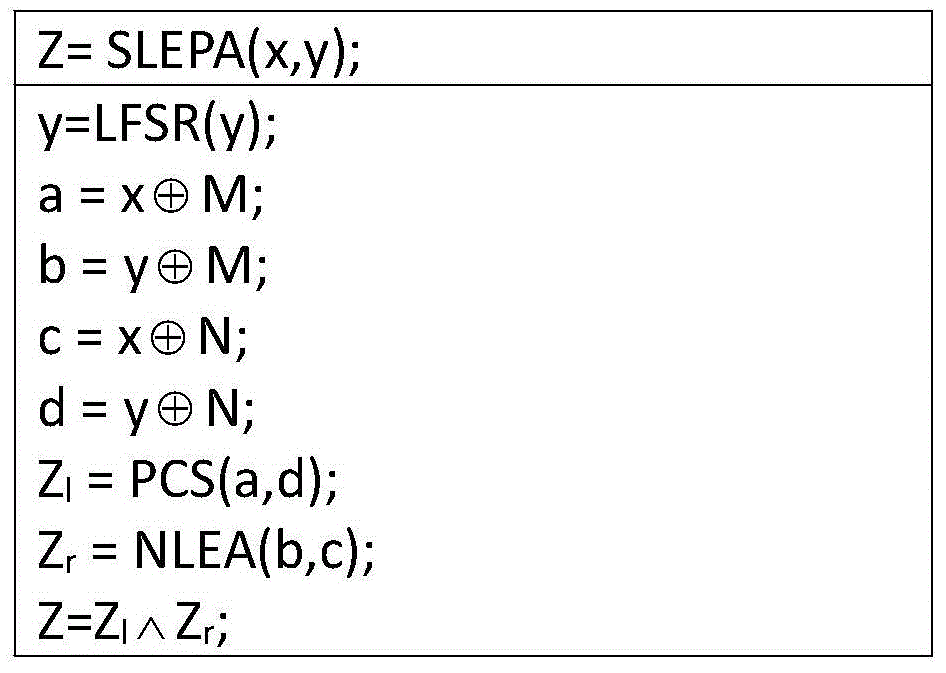
[0064] A group RFID identity authentication method is used to realize the function of passing system identity authentication in a group manner before RFID tags and RFID readers perform business communication in an RFID automatic identification system. Described RFID automatic identification system comprises RFID label group, RFID reader and background server, wherein the label in the RFID label group has no power supply, the internal EEPROM storage data in the label...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com