Identity-based authentication method and identity-based authentication system with secret key negotiation
A technology for key negotiation and authentication methods, applied in user identity/authority verification, transmission systems, key distribution, and can solve problems such as protocol man-in-the-middle attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
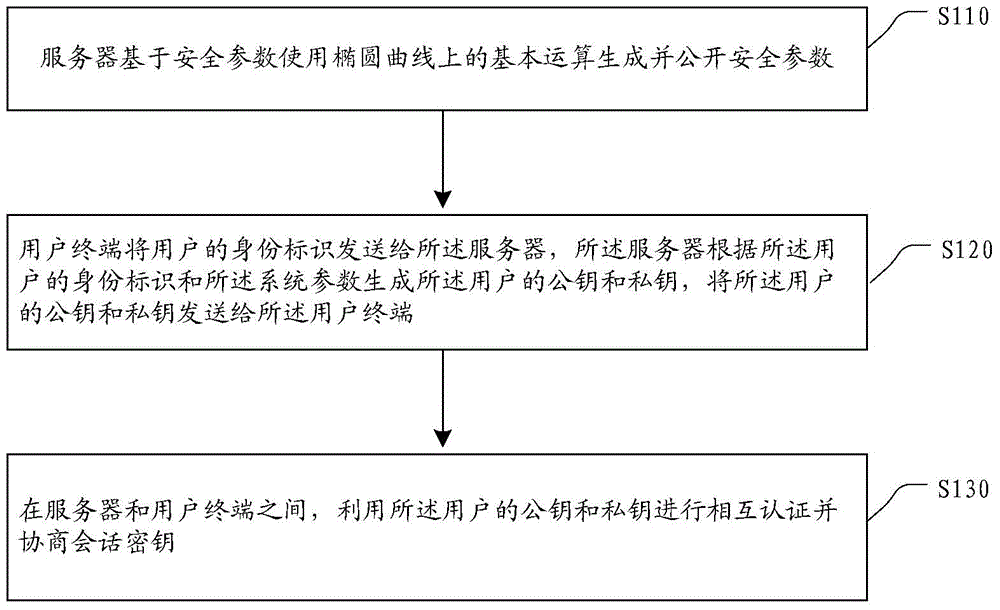
[0048] This embodiment provides a processing flow of an identity-based authentication method with key agreement as follows: figure 1 As shown, the following processing steps are included:
[0049] Step S110, based on the security parameters, the server generates and publishes the security parameters using basic operations on the elliptic curve.
[0050] Based on the security parameter k, the server S selects a cyclic group G of prime order p on the elliptic curve E on the finite field, and the generator of the cyclic group G is P. random selection of parameters in Calculate P s = d s p. Pick two secure hash functions and
[0051] Set the master key to d s , the public system parameters are (E, G, P, P s , H 1 , H 2 ).
[0052] Step S120, the user terminal sends the user's identity to the server, and the server generates the user's public key and private key according to the user's identity and the system parameters, and sends the user's public key and The...
Embodiment 2
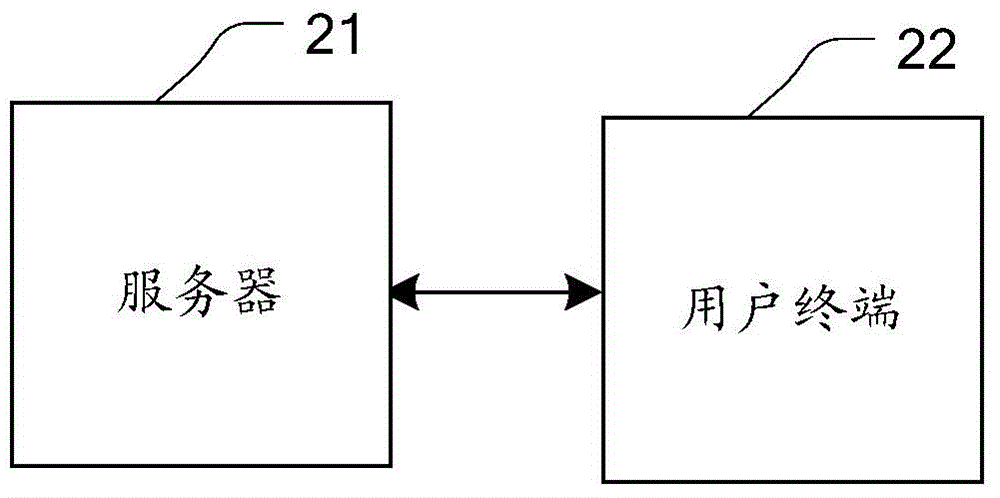
[0066] This embodiment provides an identity-based authentication device with key agreement, and its specific structure is as follows figure 2 As shown, the following modules are included: server 21, user terminal 22;
[0067] The server 21 is configured to use basic operations on elliptic curves to generate and disclose system parameters based on security parameters, generate the user's public key and private key according to the user's identity and the system parameters, and transfer the user's The public key and the private key are sent to the user terminal; and the user terminal uses the user's public key and private key to perform mutual authentication and negotiate a session key;
[0068] The user terminal 22 is configured to send the user's identity to the server, and use the user's public key and private key to perform mutual authentication and negotiate a session key with the server.
[0069] Further, the server 21 is specifically configured to select a cyclic group ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com