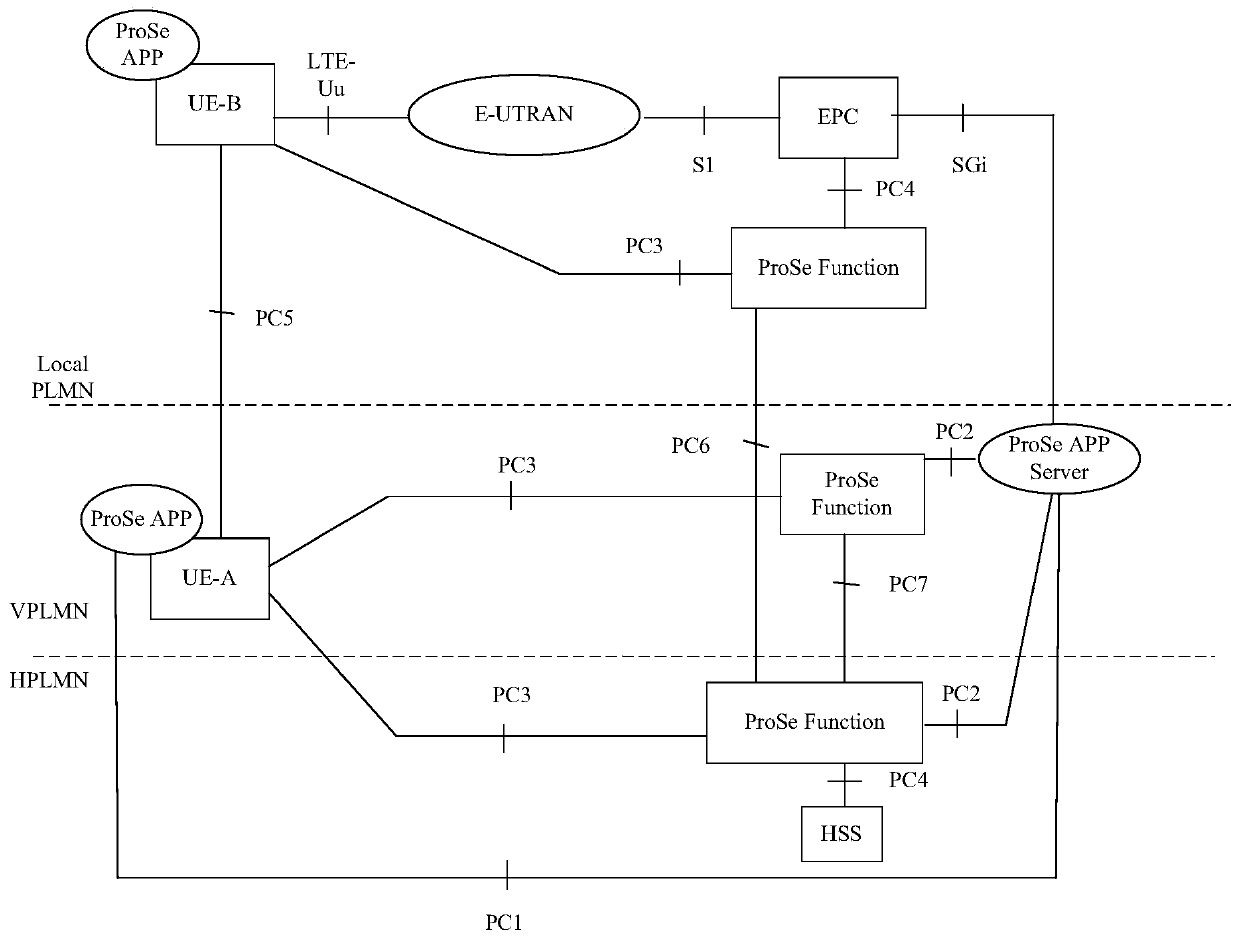
Short-range communication discovery method, device and system
A discovery method and short-distance technology, applied in the field of communication, can solve problems such as unfavorable restrictions on business development, waste of wireless resources, etc., and achieve the effect of avoiding waste of wireless resources and saving wireless resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0099] In this embodiment, PF-A assigns a discovery identifier to UE-B, and notifies UE-A and UE-B, and UE-A uses the discovery identifier to discover UE-B.
[0100] Figure 10 It is a signaling flow chart of the restricted discovery service method in Embodiment 1, such as Figure 10 As shown, the method mainly includes the following steps:
[0101] Step 1001: UE-A sends a discovery authentication message to its home PF-A, the message carries the UE-A identity, the message carries the discovery type, and to restrict discovery, the message also carries the UE-A discovery authentication message. The service identifier, the message also indicates that UE-A seeks to discover friends, and the message also includes the location information of UE-A.
[0102] Step 1002: PF-A finds that if there is no user context of UE-A, it sends a home register authentication request to obtain the user context of UE-A. If the user context of UE-A exists, PF-A sends a discovery authentication requ...
Embodiment 2
[0116] In this embodiment, PF-A assigns a discovery identifier to UE-B, and notifies UE-A and UE-B, and UE-A uses the discovery identifier to discover UE-B.
[0117] Figure 11 It is a signaling flow chart of the restricted discovery service method in Embodiment 1, such as Figure 11 As shown, the method mainly includes the following steps:
[0118] Step 1101: UE-B sends a discovery request message to its home PF-B, the message carries the UE-B identity, the message carries the discovery type, and to restrict discovery, the message also carries the UE-B discovery request message. Service identifier, the message also indicates that UE-B expects to be discovered by a friend, so the message may also carry a friend or a list of friends expected to be discovered, that is, a list of service identifiers of friends, and the list of friends or friend service identifiers includes at least The service identifier of UE-A, and the message also includes the location information of UE-B. ...
Embodiment 3
[0130] In this embodiment, the PF-B assigns a discovery identifier to UE-B, and notifies UE-A and UE-B, and UE-A uses the discovery identifier to discover UE-B.
[0131] Figure 12 It is a signaling flowchart of the discovery service method limited in this embodiment, such as Figure 12 As shown, the method includes the following steps:
[0132] Step 1201: UE-A sends a discovery authentication message to its PF-A, the message carries the UE-A identity, the message carries the discovery type, and to restrict discovery, the message also carries the UE-A service discovered this time The message also indicates that UE-A seeks a friend discovery, and the message also includes the location information of UE-A.
[0133] Step 1202: PF-A finds that if there is no user context of UE-A, it sends a home register authentication request to obtain the user context of UE-A. If the user context of UE-A exists, PF-A sends a discovery authentication request message to the application server, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com