Method and system for protecting information security of smartphone
A smart phone and information security technology, which is applied in the field of cloud computing technology and mobile computing, can solve the problem of low data security and achieve the effect of improving reliability and protecting security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0123] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
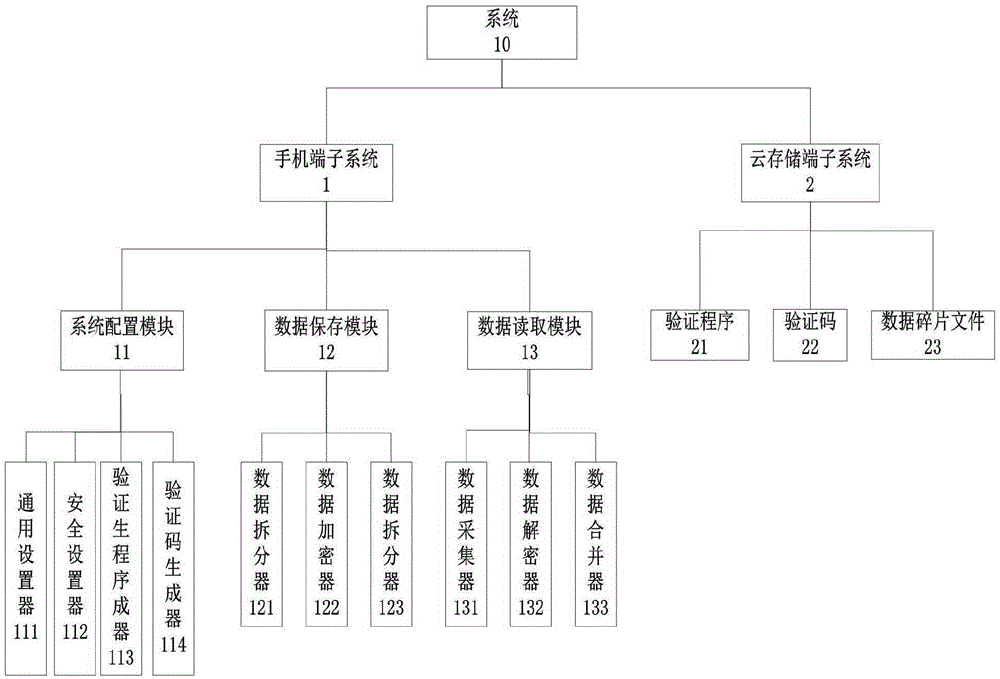
[0124] like Figure 1-3 As shown, the system module diagram is shown in image 3 shown.
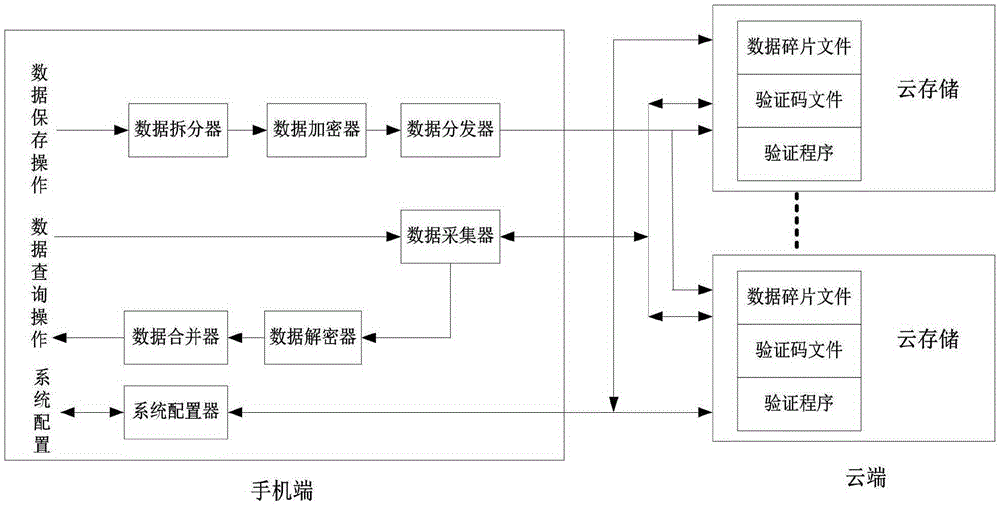
[0125] When the application in the mobile phone saves data, it does not directly call the file write operation of the operating system, but calls the program on the mobile phone. After splitting and encrypting, the data distributor calls the write operation to split the encrypted data. , according to the data slice storage settings, save in local and multiple cloud storage spaces.
[0126] When the application program calls the data, it is completed by providing the file name (including the storage path) of the data slice file to the program on the mobile phone.
[0127] A method and system for protecting the security of smartphone data. The core of the technical realization is that the storage of smartphone data is distributed in the mobile phone and multiple c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com