A call detection method, device and system
A technology for call detection and equipment, applied in the field of communications, to solve user privacy leakage, reduce processing load and service delay problems, and reduce waste.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
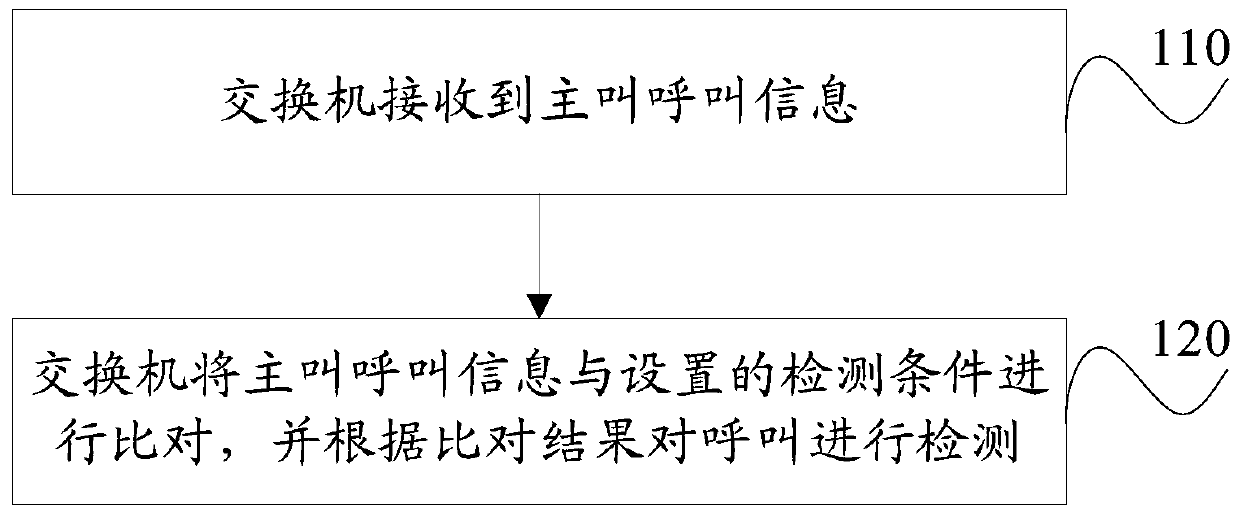
[0067] The detection condition includes the calling party, the incoming trunk, the calling number, the called office, the outgoing trunk, and / or the called number corresponding to the calling call information. Wherein, the calling party information is compared with all the parameters in the detection condition one by one, if it matches one of the parameters, then continue to compare whether other parameters matching the parameter match, if all the parameters match match, then detect that the call is a normal call, if not consistent with one of the parameters, then detect that the call is a suspicious call.
[0068] For example, the call comes from trunk number 5, the connected office of trunk number 5 is Guangzhou International Bureau, and the calling number is 0008620XXXXXXXX. However, the caller of the No. 5 trunk connected with the Guangzhou International Bureau in the existing network is generally 000190XXXX, so the call is determined to be a suspected call.
[0069] For ...
no. 2 example
[0071] The detection condition is a threshold value of the number of calling times within a specified time. Wherein, it is judged whether the calling call information is greater than or equal to the threshold value of the number of calling calls within a specified time, if yes, then detecting that the call is a suspected call; otherwise, detecting that the call is a normal call.
no. 3 example
[0073] The detection condition is the stored suspected call information. Wherein, it is judged whether the call information of the calling party is the same as the stored suspected call information, if yes, detect that the call is a suspected call, otherwise, detect that the call is a normal call. The suspected call information mentioned here includes the calling party, incoming trunk, calling number, called office, outgoing trunk, and / or called number corresponding to the calling call information.
[0074] In this embodiment, the suspected call information can be stored in the suspected call number table, and the stored suspected call information can be the information extracted after the suspected call has been confirmed in each of the above embodiments, such as the calling party number, Or, the suspected call that has been confirmed in the prior art is stored in the suspected call number table. At this time, once the subsequent call is matched, it can also be judged as a s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com