Safety access control method
A security door and gate technology, applied in electromagnetic radiation induction, instrument, character and pattern recognition, etc., can solve problems such as hidden safety hazards, high cost of fingerprint recognition systems, and the inability of fingerprint readers to distinguish user fingers.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The following examples are presented for illustrative purposes only and do not limit the scope of the invention.
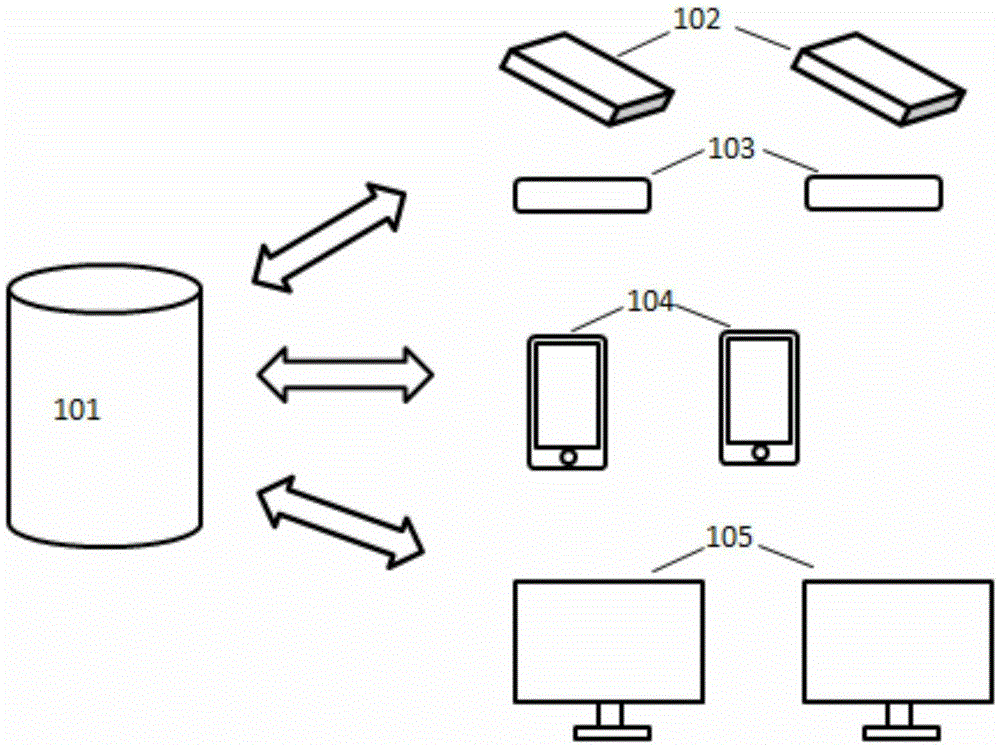
[0021] As described in the background technology, the access control system of the prior art has the problem that either the safety factor is not high, or the cost of the equipment is high, see at first figure 1 , introduces the device architecture adopted for realizing the method proposed by the present invention, it can be seen that the present invention uses a combination of various devices with low cost, which ensures that the realization cost of the present invention is low.
[0022] Such as figure 1 As shown, the access control system includes a background server 101, a plurality of cameras 102, a plurality of two-dimensional code readers 103, a plurality of mobile phones 104 communicating with the background server in a wired or wireless manner, and located in the monitoring room and capable of communicating with the background server. Multiple moni...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com