Method for secure communication of wireless sensor network based on combined password
A wireless sensor and network security technology, applied in wireless communication, network topology, security devices, etc., can solve the problems of reducing computing cost, no data confidentiality protection, and no solution to the problem of message confidentiality in wireless sensor networks. Confidentiality, the effect of reducing the amount of storage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] In order to make the purpose, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the implementation methods and accompanying drawings.
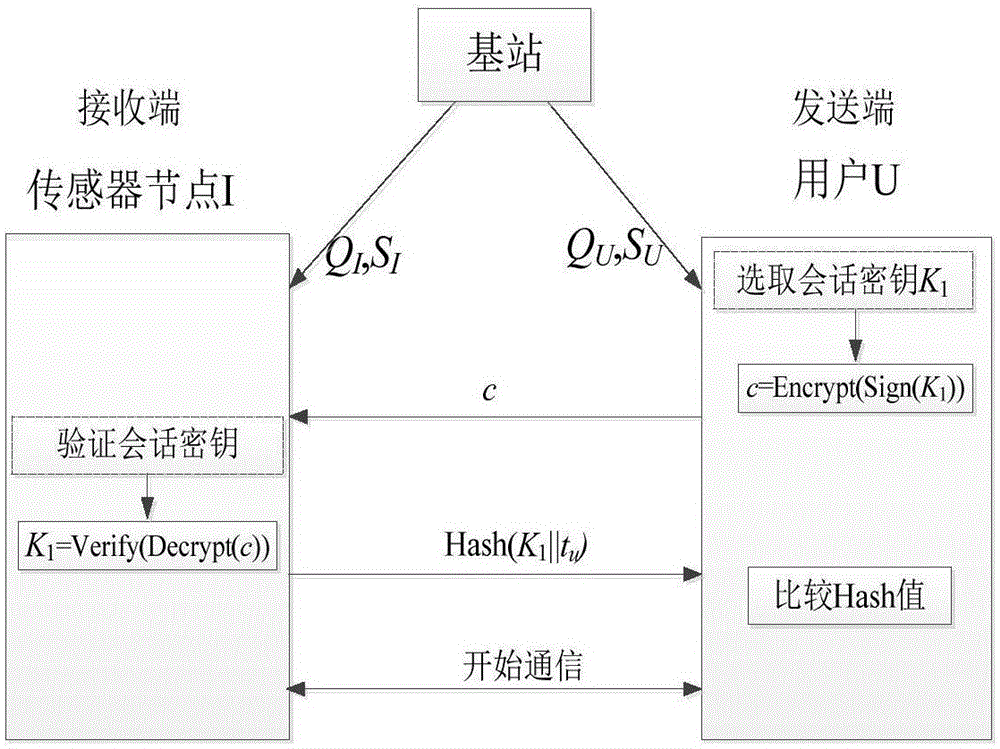
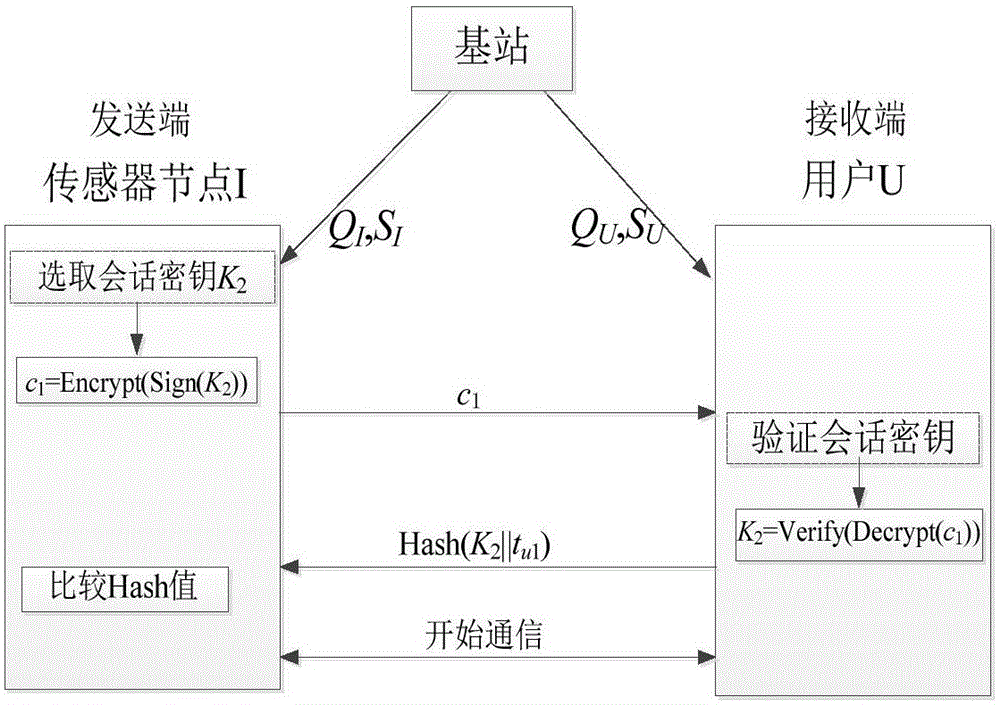
[0018] The specific realization of the present invention is as follows, this specific embodiment realizes the present invention based on the encryption scheme (BF encryption) of Boneh and Franklin and the signature scheme (CC signature) of Choon and Cheon, and its specific steps are as follows:
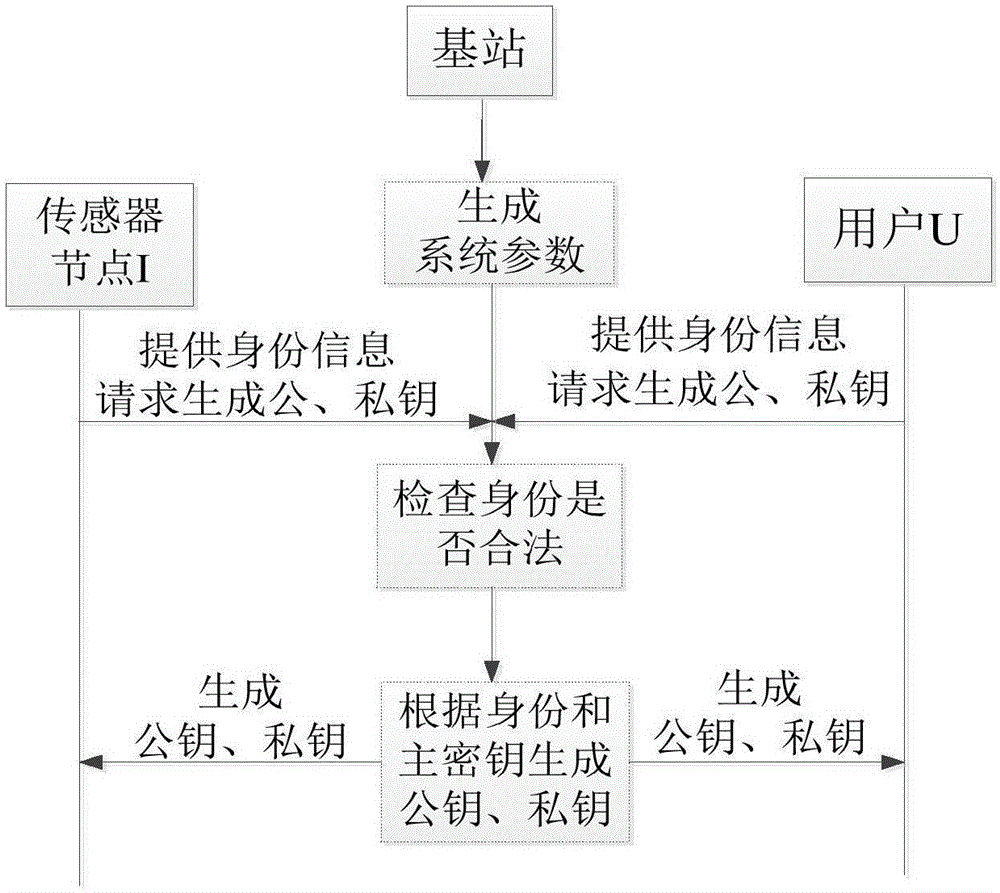
[0019] Step (1). System initialization, generate system parameters:
[0020] Step (1.1): see figure 1 , select a security parameter q (in order to ensure the security of the system, the security parameter q is preferably set to a large prime number not less than 160bit long), and based on the security parameter q, select the additive cyclic group G with prime number p as the order 1 and the multiplicative cyclic group G T , choose P as the gr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com