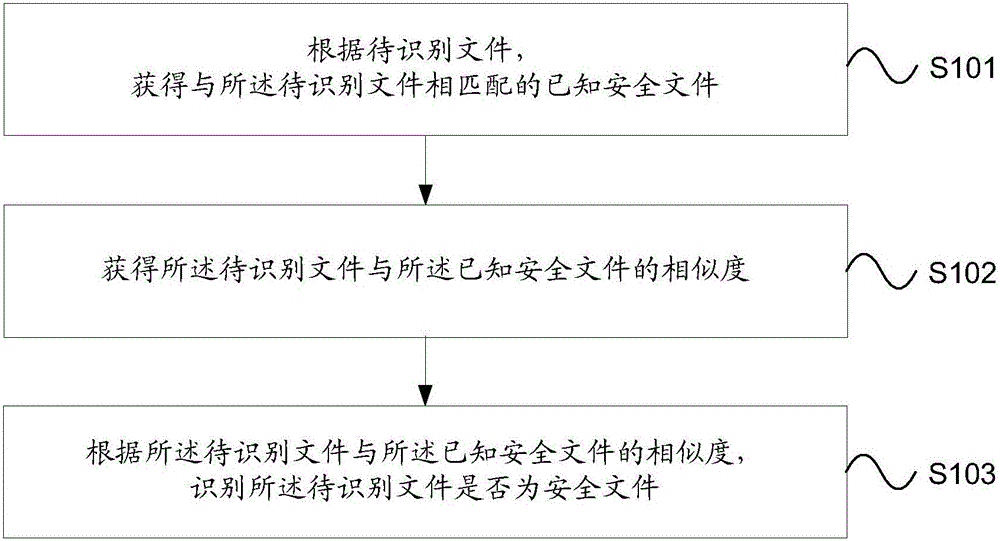
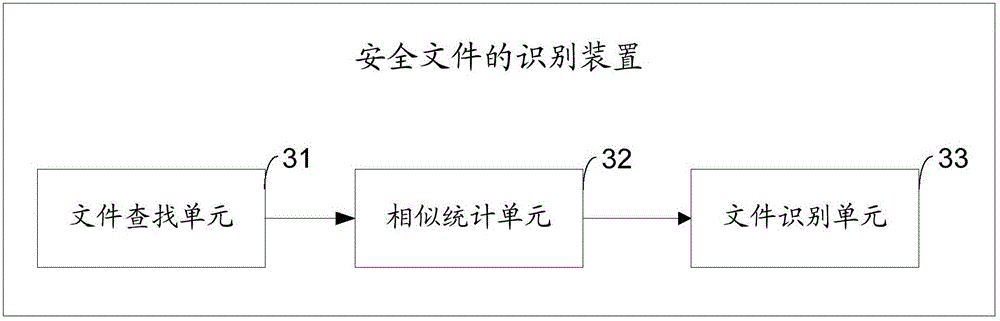
Recognition method and device for secure file
A security file and identification method technology, which is applied in the field of network security, can solve the problem of low identification rate of security documents, achieve the effect of solving the low identification rate, meeting identification requirements, and improving user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
[0075] Based on the security file identification method provided in the first embodiment above, the embodiment of the present invention specifically describes the method of obtaining a known security file that matches the file to be identified according to the file to be identified in S101. This step can specifically include:
[0076] To illustrate, in the embodiment of the present invention, according to the file to be identified, the method of obtaining a known safe file that matches the file to be identified may include but not limited to:
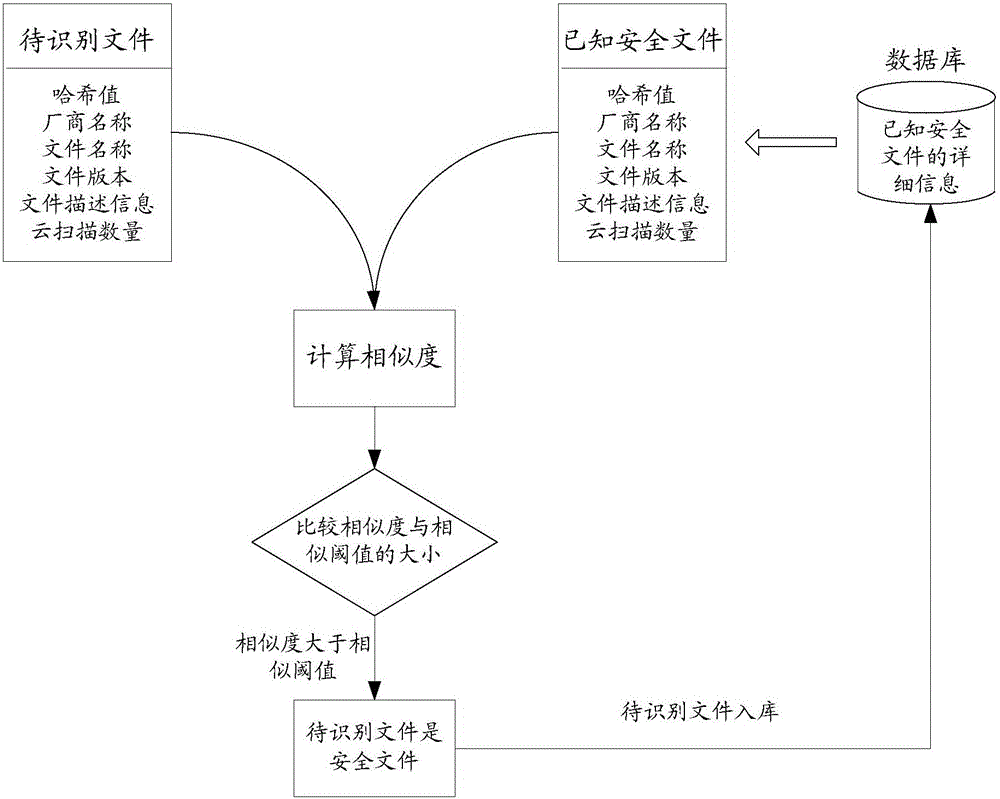
[0077] Please refer to figure 2 , which is an example diagram of using a known security file to identify a file to be identified provided by an embodiment of the present invention. As shown in the figure, according to the detailed information of the file to be identified, matching is performed in the database to obtain the A known safe file that matches the file to be identified; wherein, the database contains detailed information of ...
Embodiment 3
[0085] Based on the security file identification method provided in the first embodiment and the second embodiment, the embodiment of the present invention specifically describes the method for obtaining the similarity between the file to be identified and the known security file in S102. This step can specifically include:
[0086] In a specific implementation process, the method for obtaining the similarity between the file to be identified and the known safe file may include but not limited to: first, obtain the code block fingerprint of the file to be identified. Then, according to the code block fingerprint of the file to be identified and the code block fingerprint of the known safe file, the similarity between the file to be identified and the known safe file is obtained.
[0087] To illustrate, in the embodiment of the present invention, the method for obtaining the code block fingerprint of the file to be identified may include but not limited to:
[0088] Decompilin...
Embodiment 4
[0112] Based on the security file identification method provided in the first embodiment above, the second embodiment and the third embodiment, the embodiment of the present invention identifies the security file to be identified according to the similarity between the file to be identified and the known security file in S103. The method for identifying whether a file is a safe file is described in detail. This step can specifically include:
[0113] For example, in the embodiment of the present invention, according to the similarity between the file to be identified and the known safe file, the method for identifying whether the file to be identified is a safe file may include:
[0114] Such as figure 2 As shown, the similarity between the file to be identified and the known safe file is compared with a preset similarity threshold. If the comparison result is that the similarity between the file to be identified and the known safe file is greater than the similarity thresh...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com