System and method for performing digital rights management for terminal equipment
A technology of digital rights management and terminal equipment, which is applied in the transmission system, user identity/authority verification, electrical components, etc., can solve problems such as user troubles, and achieve the effect of more efficient and safe instructions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
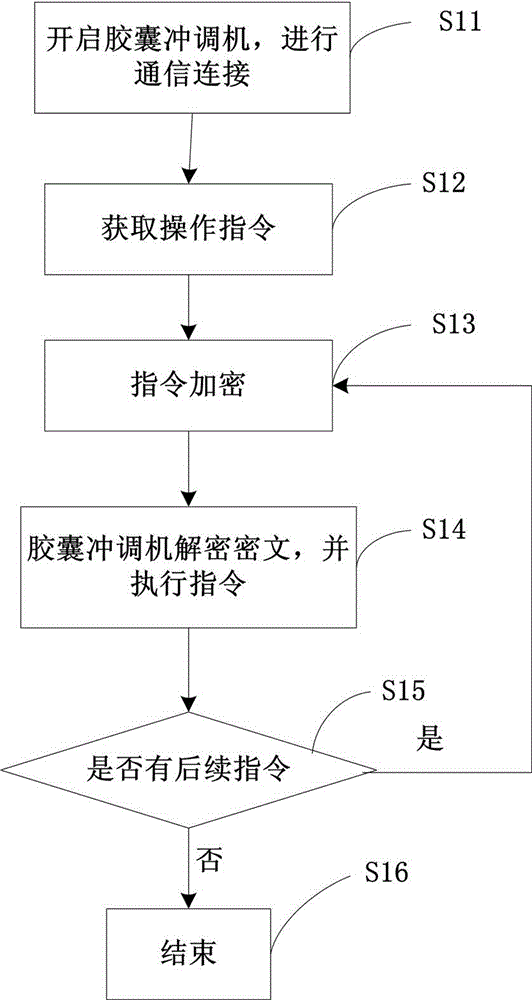
[0044] figure 1 It is a schematic structural diagram of a system for digital rights management of a capsule brewing machine involved in this embodiment. Such as figure 1 As shown, the system includes a capsule brewing machine 1 and an intelligent control terminal 2, which are interconnected through Bluetooth or WIFI communication protocols. The capsule brewing machine 1 includes a communication unit 11 , an information processing unit 12 , a work execution unit 13 , a control unit 14 and a storage unit 15 . The communication unit 11 is responsible for communicating with the intelligent control terminal 2 via Bluetooth or WIFI, receiving instructions sent by the intelligent control terminal 2 , or sending feedback information from the capsule brewing machine 1 to the intelligent control terminal 2 . The information processing unit 12 can analyze the corresponding execution instruction information from the ciphertext sent by the intelligent control terminal 2 according to the ...
Embodiment 2
[0051] The system in Embodiment 1 performs the encryption operation of the instruction information through the intelligent control terminal 2, and sends the encrypted instruction information to the capsule brewing machine, and the capsule brewing machine decrypts and executes the decrypted operation instruction, so that the encryption process Complete on the smart terminal. Malicious crackers who master smart terminals may obtain system core information such as encryption methods and encryption algorithms by monitoring the encryption process or other means, which system operators do not want to see.
[0052] In order to solve the above-mentioned technical problems, this embodiment puts the encryption process of the instruction in the background cloud module. The background cloud module and the intelligent control terminal can be interconnected through the network, and the account and the corresponding password need to be set to log in the background cloud module, so that you ca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com