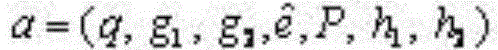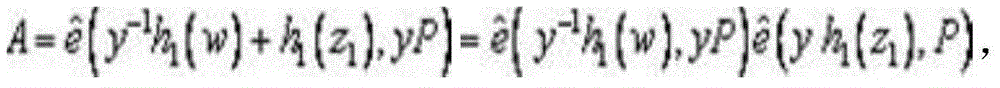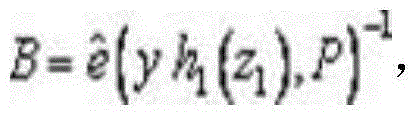Fuzzy keyword public key searchable encryption scheme achieving unrecognizable trap door
An unidentifiable and encryption scheme technology, applied in the field of cloud computing and cryptography, which can solve the problems of unidentifiable trapdoors and unidentifiable trapdoors.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0009] The embodiment of the present invention includes the following algorithms altogether.
[0010] Algorithm 1: Generate prime order q≥2 k a group g of 1 , a g 1 A random generator P for constructing a bilinear map :g 1 × g 1 → g 2 .Specify the hash function h 1 : {0, 1}*→g 1 , h 2 :g2 → {0, 1} k ,return a = ( q , g 1 , g 2 , e ^ , P , h 1 , h 2 ) as a public parameter.
[0011] Algorithm 2: :random selection Then calculate X=xP, choose randomly Return public key PS=(cp, Q, X) and private key SS=(cp, x) as the public-private key pair of the server.
[0012] Algorithm 3: :random se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com