Cloud configuration safety assessment method
A security assessment and security technology, applied in the field of cloud computing security, can solve the problem of no cloud architecture security assessment mechanism, no hierarchical analysis of cloud platform security, etc., to improve development quality, facilitate mathematical analysis, and simplify calculations.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] Specific embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings. If there are exemplary contents in these embodiments, they should not be construed as limiting the present invention.
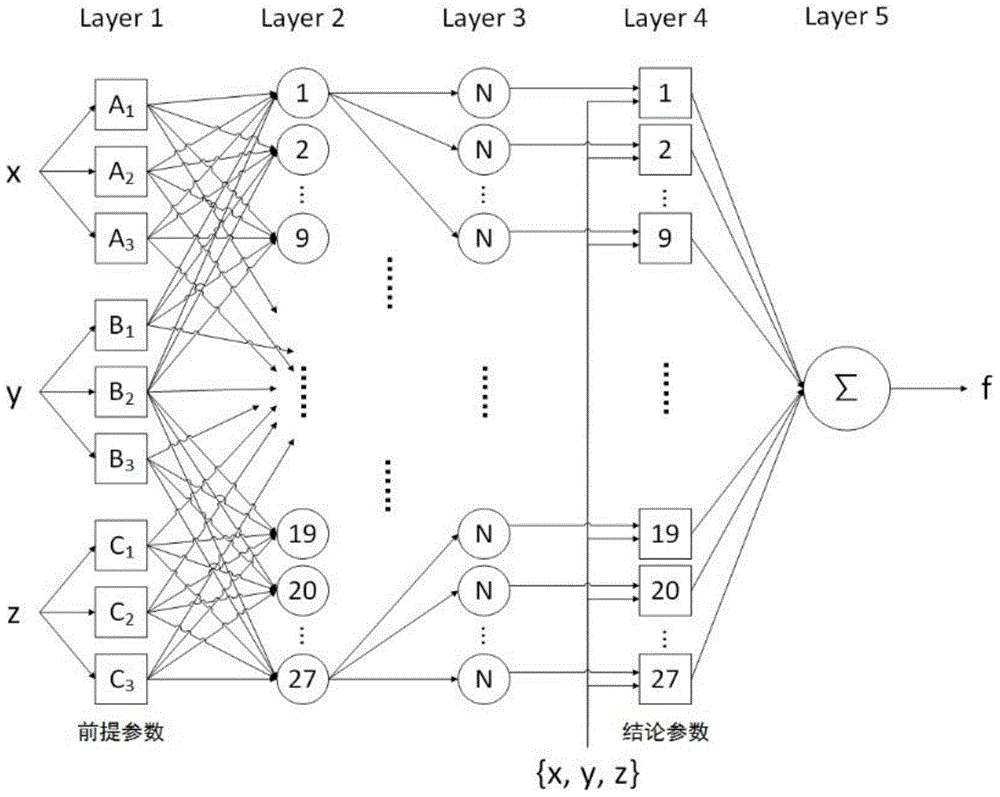
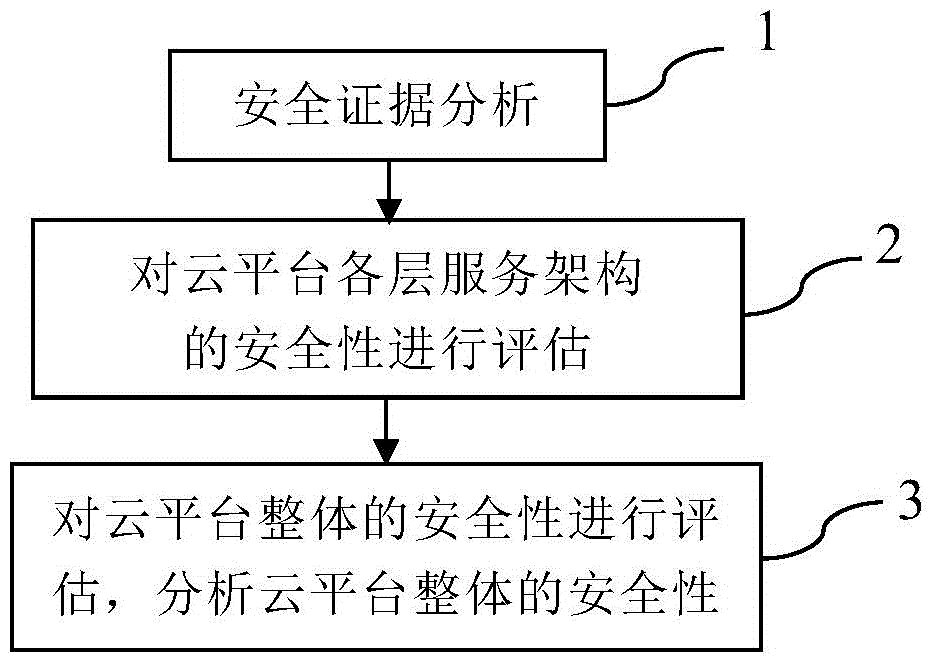
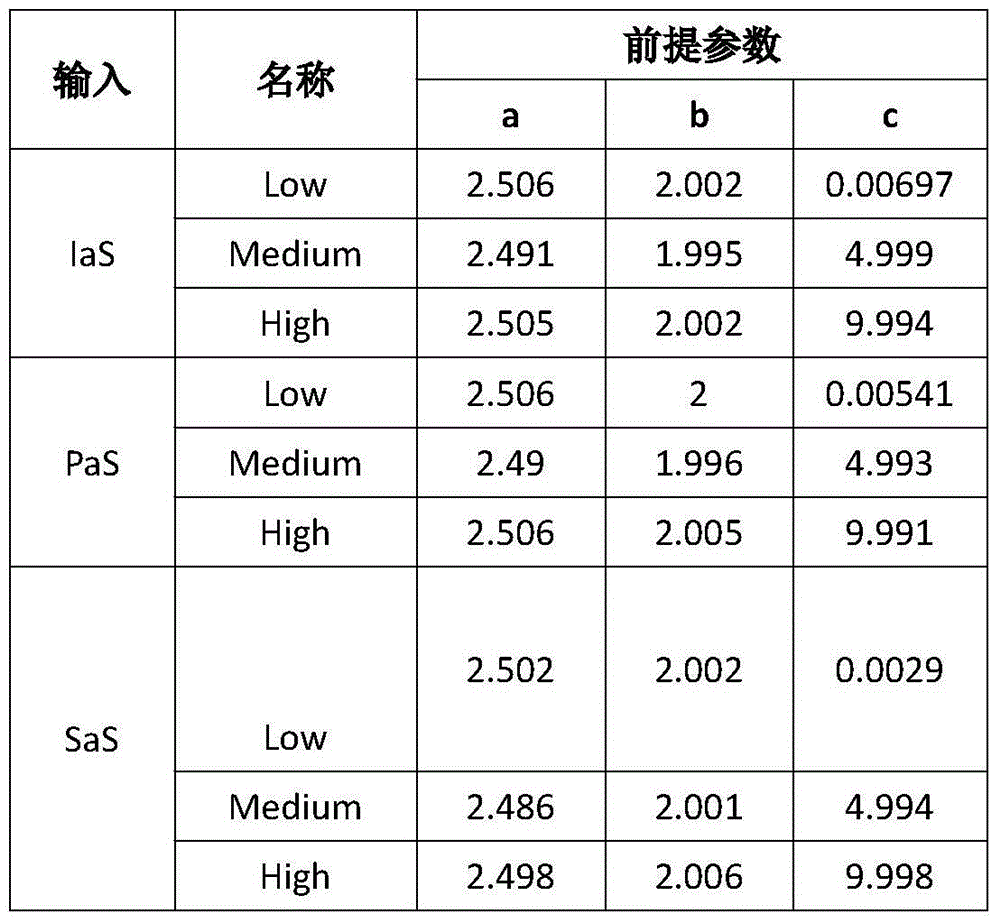
[0029] The present invention is evaluated with the Google cloud platform as a specific embodiment. Select Google Compute Engine as the instance of the IaaS layer, Google App Engine as the instance of the PaaS layer, and Google Apps as the instance of the SaaS layer. First use the security evaluation model of each layer of service architecture, and then use the overall security evaluation model of the cloud platform to finally obtain the overall security value of the cloud platform architecture.
[0030] 1. IaaS instance analysis (Google Compute Engine)
[0031] First, analyze the security issues of GCE and the corresponding security evidence, including:
[0032] Virtual machine security issues: the reliability of the virtual ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com