Function template based software behavior analysis method
A function template and behavior analysis technology, applied in the field of information security, can solve the problem of insufficient detection of malicious software behavior, and achieve the effect of simple and easy method of software behavior detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
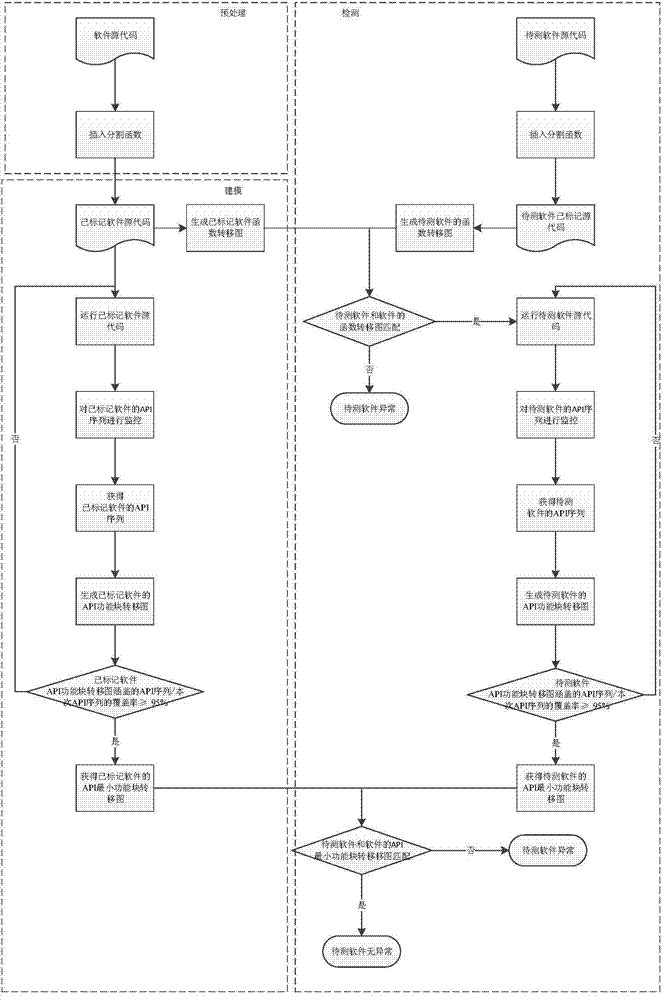
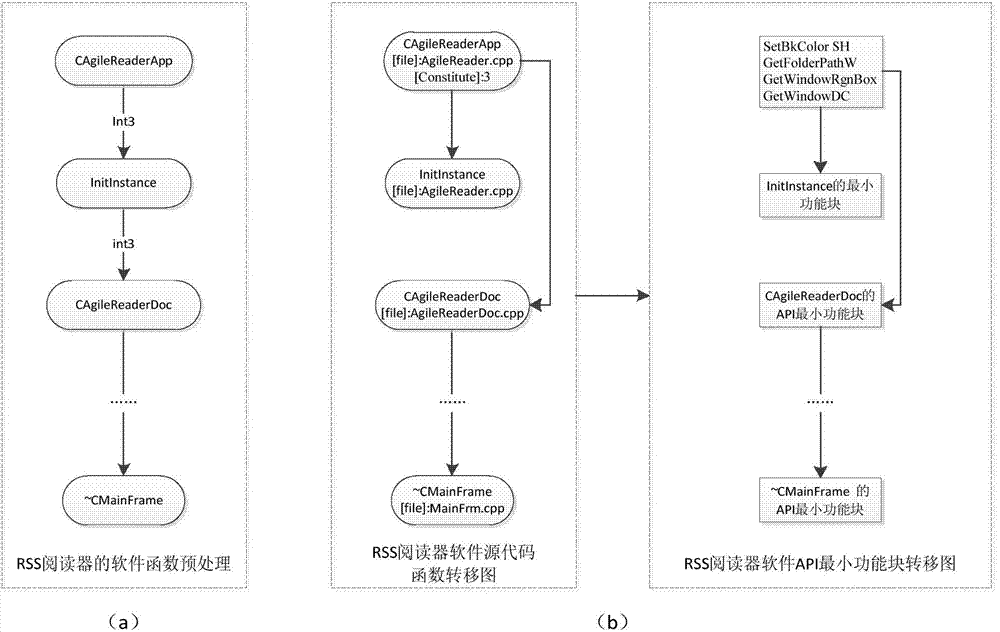
[0036] Such as figure 2 As shown, the detection of RSS reader software is taken as an example.
[0037] Step 1: Preprocessing.
[0038] Step 1.1: Insert the segmentation function int3 between each two functions of the RSS reader software source code, the segmentation function int3 simulates the operation of the software breakpoint, and use each segmentation function int3 as a mark, and the marked RSS reader software source code is called Tagged RSS Reader Source Code, and the corresponding software is called Tagged RSS Reader Software (see figure 2 (a)).
[0039]
[0040]
[0041] Step 2: Modeling.
[0042] Step 2.1: First define the concepts involved in the modeling:
[0043] Node: This method analyzes the function in the source code of the marked RSS reader as a unit. The definition of the node includes the function in the source code of the marked RSS reader, the source file name to which the function in the source code of the marked RSS reader belongs, and the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com