IDC business scene-orientated security service arranging method and network structure
A technology for security services and business scenarios, applied in the field of security service orchestration methods and network structures, and can solve problems such as unrealistic deployment of a single device
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] The preferred embodiments will be described in detail below in conjunction with the accompanying drawings.
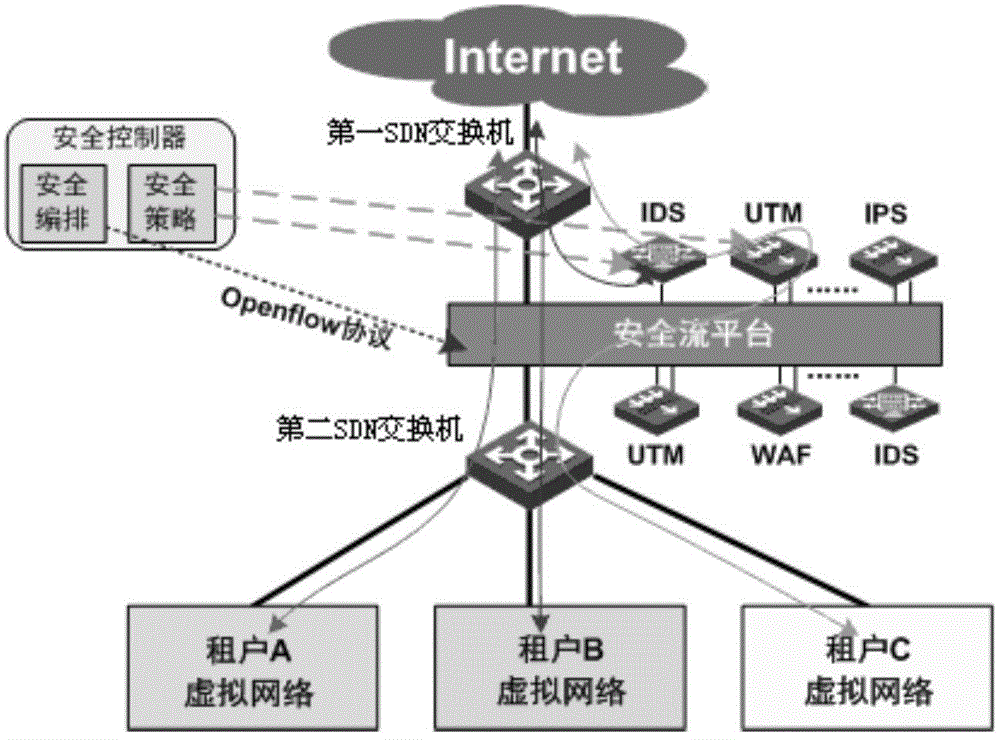
[0018] The present invention proposes a security service orchestration method for IDC business scenarios, such as figure 1 shown, including:
[0019] Step 1. The security streaming platform is deployed at the entrance and exit of IDC (Internet Data Center, Internet Data Center), and one or more UTM (Unified Threat Management, security gateway), IDS (Intrusion Detection Systems, intrusion detection system), IPS (Intrusion Prevention System, intrusion prevention system), WAF (Web Application Firewall, website application level intrusion prevention system) and other security devices are connected to one or more SDN (Software Defined Network, software defined network) switches to form a security resource pool;
[0020] Step 2. The security controller issues a security control command to operate the SDN switch, and draws the network traffic to the designated network...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com