Method, device and system for checking and killing malicious application programs
A malicious application and killing technology, applied in the computer field, can solve the problems of no stubborn Trojan killing method, inability to detect and kill, and inability to operate mobile terminals.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0118] The embodiment of the present invention provides a method for checking and killing malicious applications. The method is applied to the PC terminal side. By connecting with the mobile terminal, when the mobile terminal is locked and cannot be operated, the malicious application program on the mobile terminal is completed. The killing.
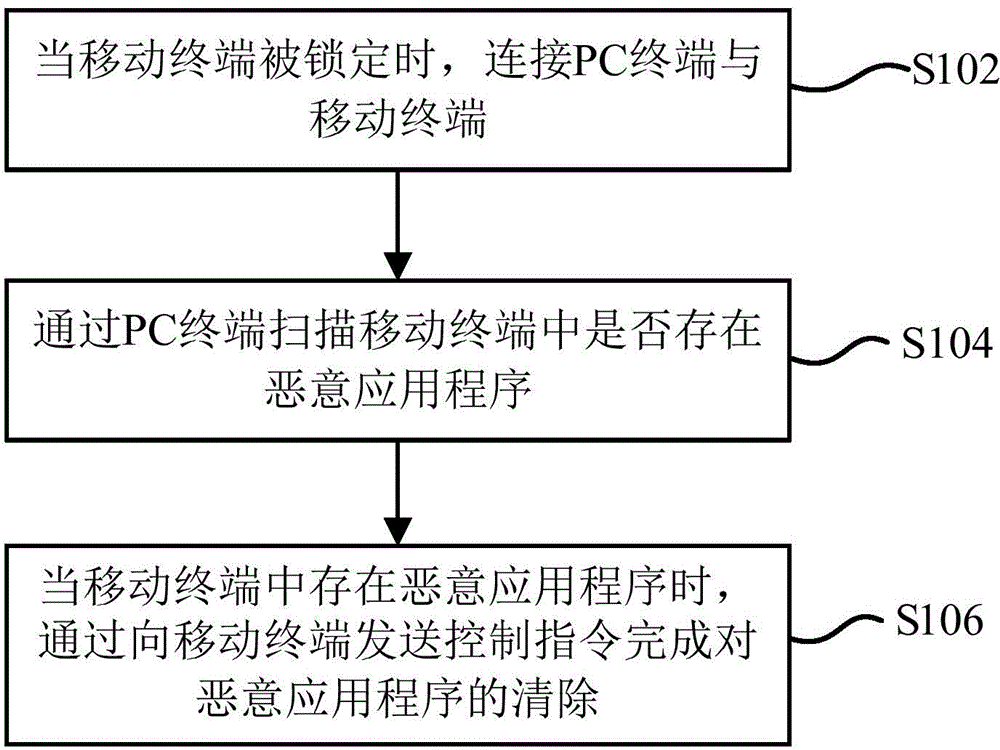
[0119] figure 1 It is a flowchart of a method for checking and killing malicious applications according to an embodiment of the present invention. The method is applied to the PC terminal side and includes steps S102 to S106:
[0120] S102: When the mobile terminal is locked, connect the PC terminal and the mobile terminal.
[0121] S104: Scan the mobile terminal for malicious applications through the PC terminal.
[0122] S106: When there is a malicious application in the mobile terminal, complete the removal of the malicious application by sending a control instruction to the mobile terminal.
[0123] The embodiment of the present invention pro...
Embodiment 2
[0125] The embodiment of the present invention provides a method for detecting and killing malicious applications. The method is applied to the mobile terminal side and is connected with the PC terminal to complete the detection of malicious applications on the mobile terminal when the mobile terminal is locked and cannot be operated. The killing.
[0126] In the present invention, the mobile terminal may be a mobile phone, a tablet computer and other devices.
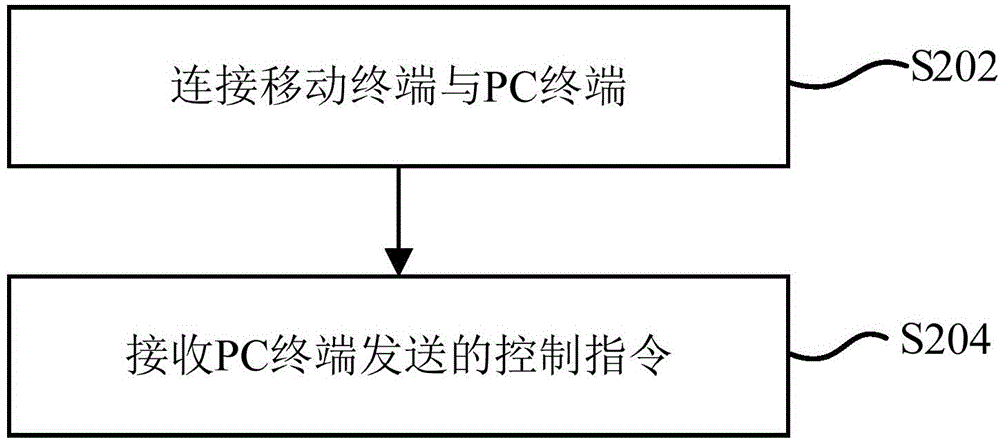
[0127] figure 2 It is a flowchart of a method for detecting and killing malicious applications provided by an embodiment of the present invention. The method is applied to a mobile terminal and includes steps S202 to S204:
[0128] S202: Connect the mobile terminal and the PC terminal.
[0129] S204: Receive a control instruction sent by the PC terminal.
[0130] Wherein, the aforementioned control instruction is used to complete the removal of malicious applications.
[0131] The embodiment of the present invention provides a ...
Embodiment 3
[0133] The method for detecting and killing malicious applications provided by the present invention is realized by the cooperation of a PC terminal and a mobile terminal. The first embodiment is to describe the method for detecting and killing malicious applications on the PC terminal side. The terminal side explains the method of checking and killing malicious applications.
[0134] The third embodiment is a specific application scenario of the first and second embodiments above, and is described in conjunction with the PC terminal and the mobile terminal side. Through this embodiment, the method provided by the present invention can be explained more clearly and specifically.
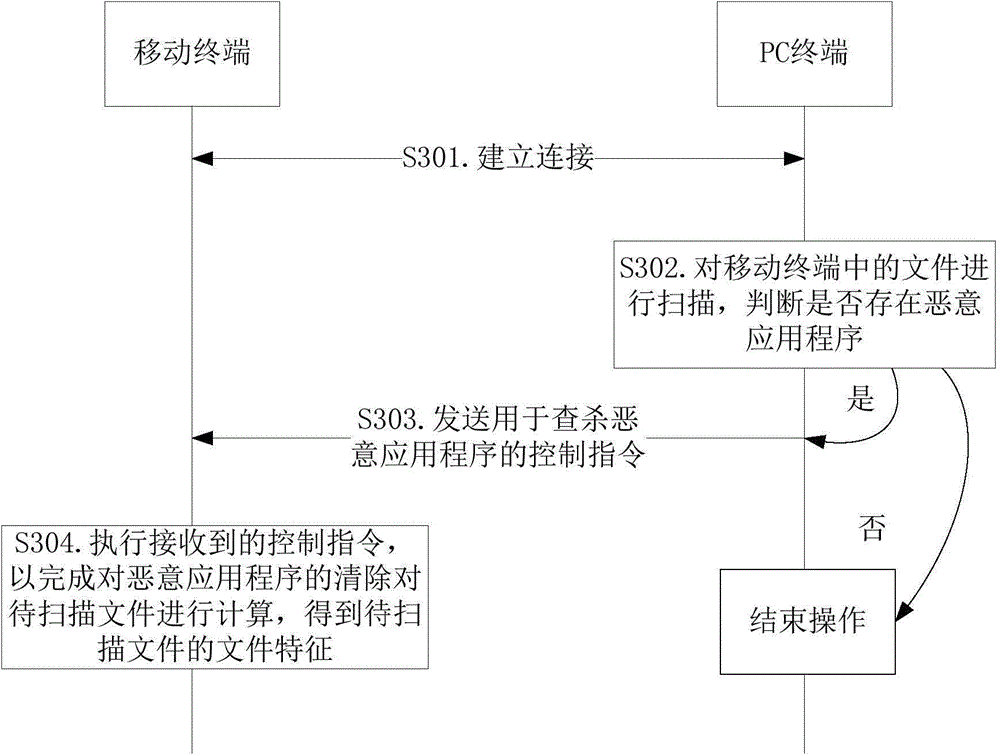
[0135] image 3 It is a flowchart of a specific method for checking and killing malicious applications provided by an embodiment of the present invention, including step S301 to step S304.
[0136] In step S301, when the mobile terminal is locked, a connection between the PC terminal and the mobile termina...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com