Certificateless signature method based on Schnorr signature algorithm
A certificate-free, signature verification technology, applied in the field of network security, can solve the problems of ignoring public key replacement attacks, few system parameters, and more bilinear equivalence, achieving high trust level, reducing the number of uses, and low honesty.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The present invention will be further described below in conjunction with the accompanying drawings.
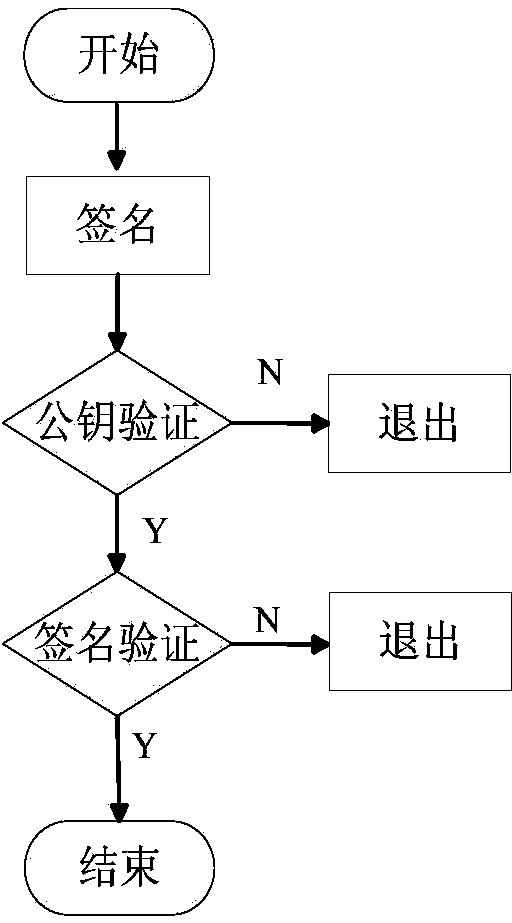
[0026] refer to figure 1 , the implementation steps of the present invention are as follows:
[0027] Step 1, the key generation center KGC generates system parameters.
[0028] (1a) Set the security parameter l of the certificateless signature system according to actual requirements;
[0029] (1b) The key generation center KGC selects a large prime number p according to the set system security parameter l, where p>2 l , to construct an additive cyclic group G of order p 1 and p factorial cyclic group G 2 , so that it satisfies the bilinear map e:G 1 ×G 1 →G 2 , that is, from the additive cyclic group G 1 Take any two elements in arbitrarily as the input of the bilinear map e, then its output must be the multiplicative cyclic group G 2 an element in
[0030] (1c) The key generation center KGC selects a function f(Q): if the input Q is an odd number, then outp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com