Security protocol based on received signal intensity in wireless sensor network
A technology of receiving signal strength and wireless sensors, which is applied in the field of establishment and dynamic key management, can solve the problems of high encryption and decryption overhead, and achieve the effect of reducing space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0059] In order to solve the security problem in the wireless sensor network, the invention combines the establishment of the security route and the management method of the dynamic key to form an efficient security protocol. In order to realize above-mentioned result, main steps of the present invention are as follows:
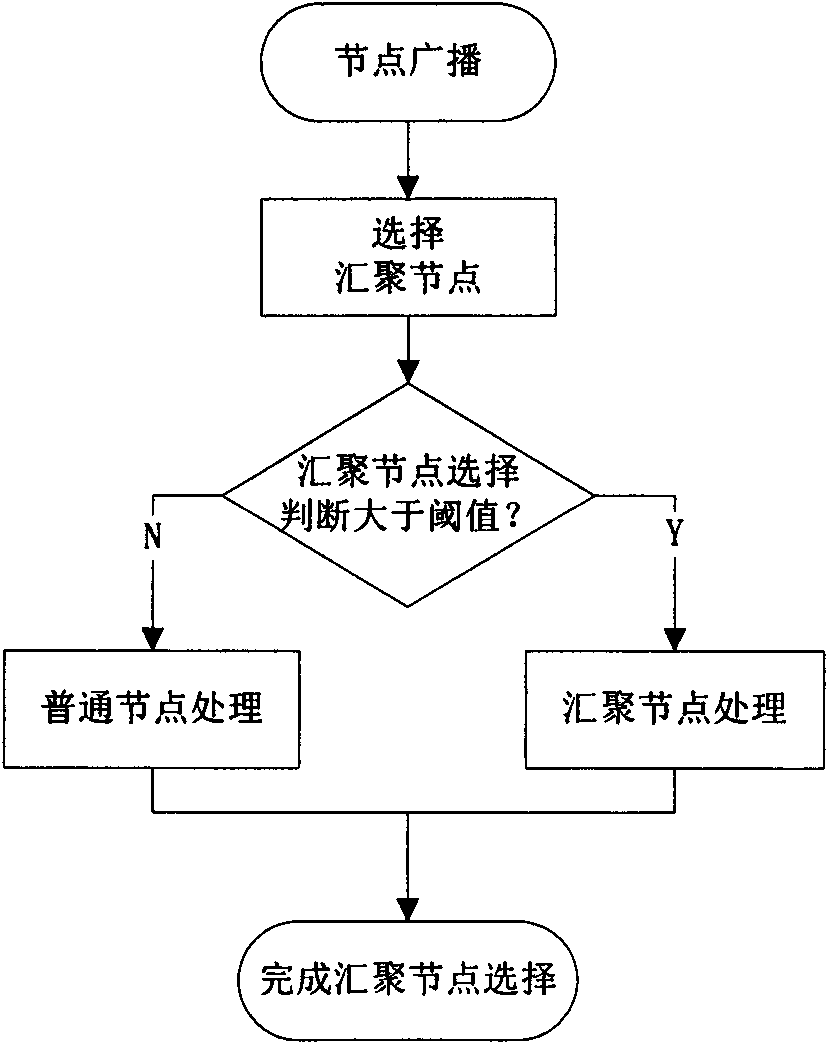
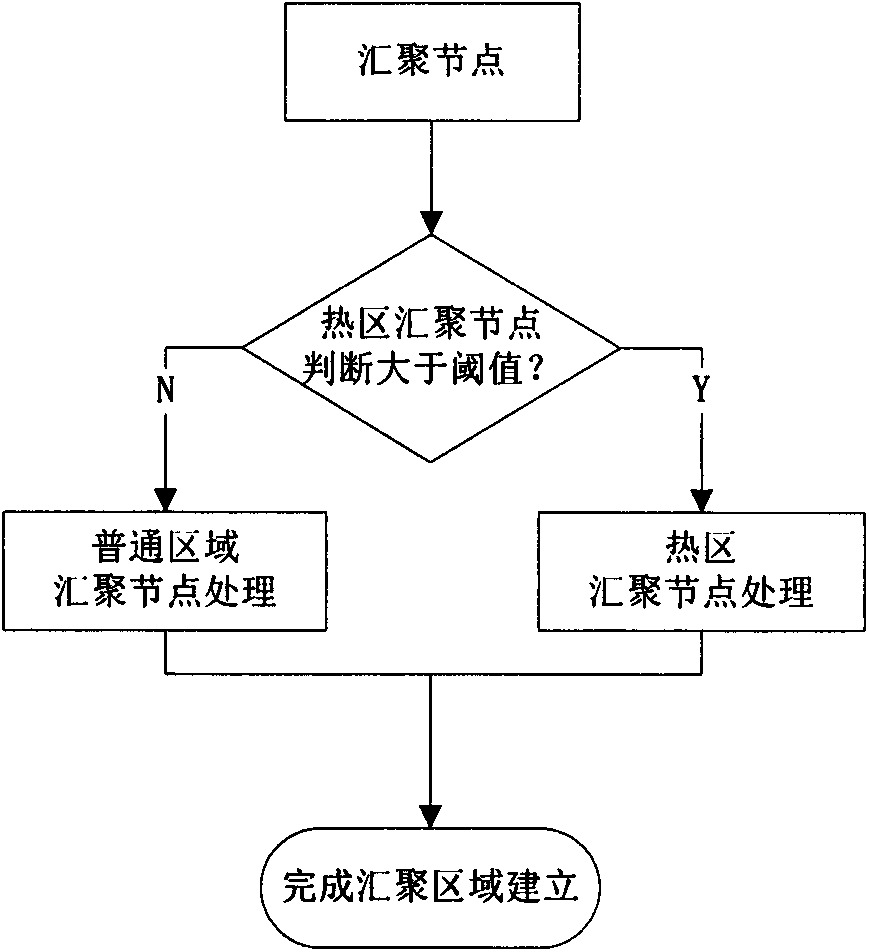
[0060] combine figure 1 As shown in the figure, we can know the steps to establish the sink node and hot zone:
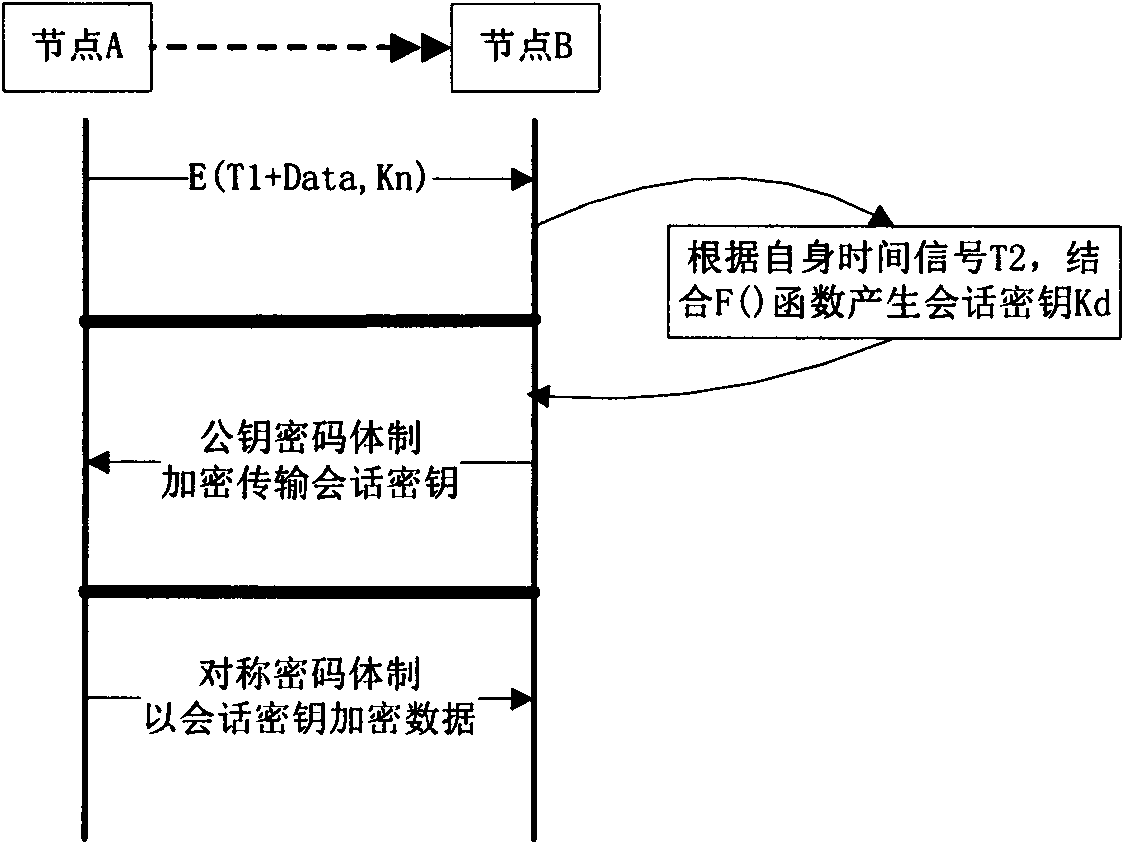
[0061] 1) There are N nodes in the unknown area, using the pre-stored key K n Encrypted broadcast, transmission data content has 5 items;
[0062] 2) The format and examples of sending data messages are as follows:
[0063]
[0064] 3) Each node uses the key K n Decrypt the received message, and then use the sink node selection formula to calculate the sink node selection factor θ according to the number of neighbor nodes, received signal strength and its own energy value, if θ is greater than F Th , it will be converted from a normal node ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com