A Traffic Identification Method Based on Deep Packet Inspection
A traffic identification and message technology, applied in the field of communication, to achieve the effect of easy implementation and optimization of the identification process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
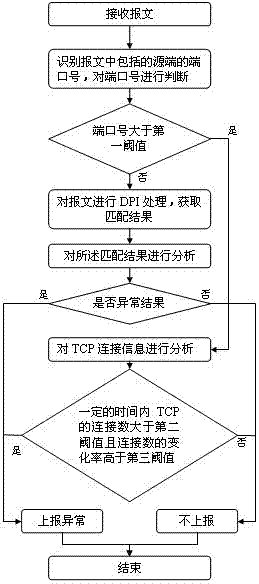
[0030] Embodiment 1 of the present invention provides a method for identifying TCP traffic using DPI technology, including:
[0031] Step 202, receiving a TCP connection message, which includes network control data and data sent by the user;
[0032] Step 204, identifying the port number of the source end included in the message, and judging the port number;
[0033] Step 206, if the port number is greater than the preset first threshold, go to step 212, otherwise go to step 208;
[0034] Step 208, perform DPI processing on the message, extract the character string in the message, pass the character string through a Bloom Filter composed of 1 hash function, and perform rough matching, if the match is successful, directly report the matching result, and enter step 210; If the matching is unsuccessful, then enter fine matching, the string is passed through the Bloom Filter formed by n hash functions, where n>1, to obtain the matching result, and enter step 210;
[0035] Step 2...
Embodiment 2
[0039] After step 214 of the first embodiment is completed, proceed to step 216, store the feature of the abnormal message, and identify the subsequent message with reference to the feature, the feature includes at least one of the following: the TCP connection A quintuple, the matching result.
Embodiment 3
[0041] With reference to this feature of embodiment two, follow-up message is identified, specifically: according to the source IP address and destination IP address of the TCP where abnormal message is located, identify the communication parties that send the abnormal message, for all ports of the communication parties The data sent above is processed by DPI, the matching result is obtained, analyzed, and the abnormal result is reported.
[0042] Those of ordinary skill in the art can understand that all or part of the processes in the methods of the above embodiments can be implemented through computer programs to instruct related hardware, and the programs can be stored in a computer-readable storage medium. During execution, it may include the processes of the embodiments of the above-mentioned methods. Wherein, the storage medium may be a magnetic disk, an optical disk, a read-only memory (Read-Only Memory, ROM) or a random access memory (Random Access Memory, RAM) and th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com