A jtag circuit with a protection module
A technology for protecting modules and circuits, applied in internal/peripheral computer component protection, digital data authentication, etc., can solve problems such as chip attacks, and achieve the effects of preventing attacks, reducing hardware costs, and preventing control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
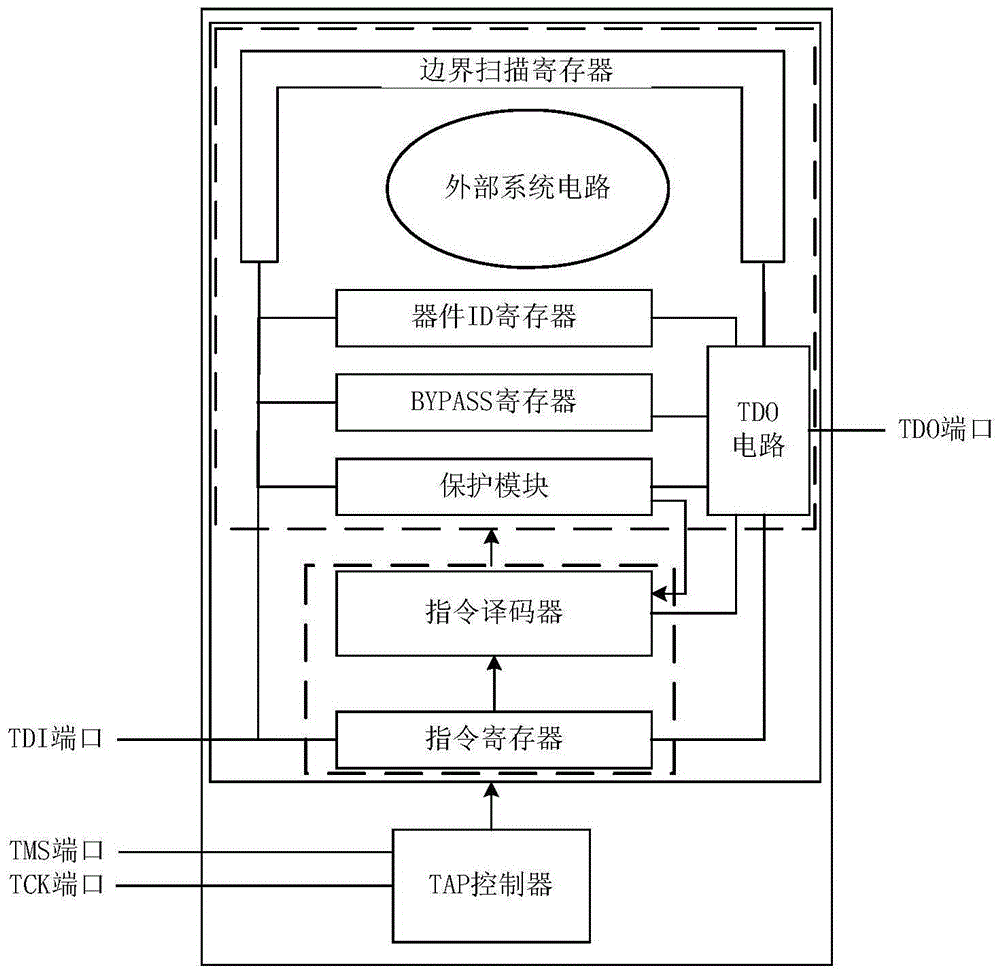
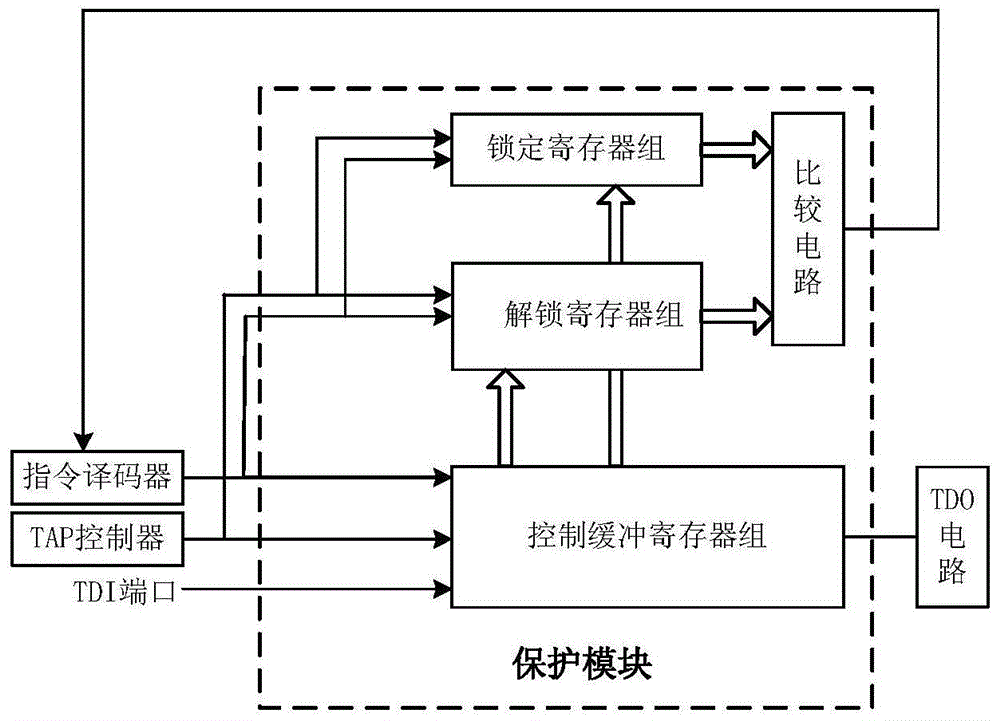
[0042] Such as figure 1 Shown is the composition block diagram of JTAG circuit of the present invention, can know that the JTAG circuit that the present invention has protection module comprises TAP controller, instruction register, instruction decoder, protection module, BYPASS register, device ID register, boundary scan register, TDO circuit, and TDI port, TMS port, TCK port and TDO port, where:
[0043] The TDI port, the TMS port, and the TCK port are the input ports of the JTAG circuit, and the TDO port is the output port of the JTAG circuit;
[0044] The TAP controller generates a state transition control signal according to the mode selection data input by the TMS port and the clock signal input by the TCK port, and sends the state transition control signal to the instruction decoder, the protection module, the BYPASS register, the device ID register, and the boundary scan register;
[0045] The instruction register receives the serial instruction data input through th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com