DoS (Denial of Service) and DDoS (Distributed Denial of service) attack resisting method of DNS recursive server
A recursive server and timer technology, applied in the Internet field, can solve the problems of domain name cache hit rate reduction, destruction, recursive server resource occupation, etc., to achieve the effect of improving cache hit rate, ensuring normal response, and maintaining safe operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
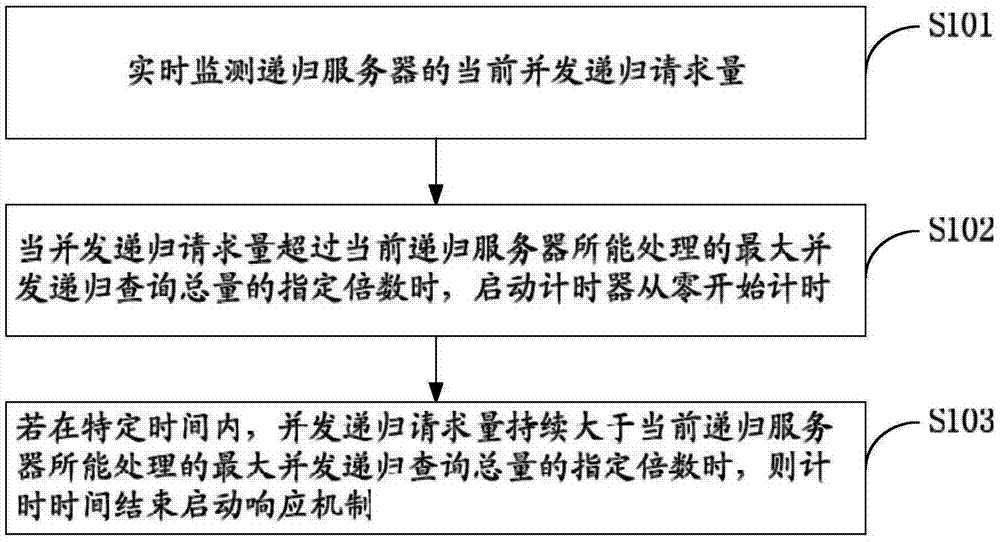
[0047] Embodiment 2 is to limit the number of concurrent recursive queries, specifically including the following steps:
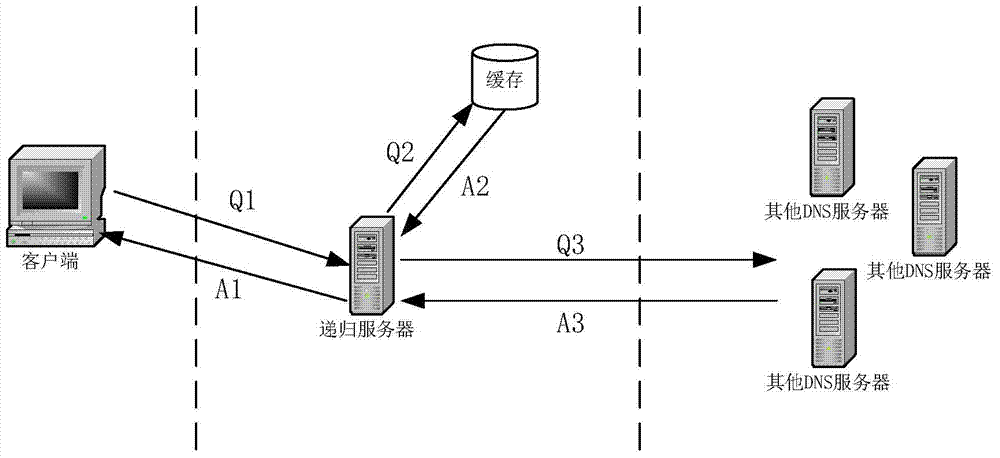
[0048] From the domain name requests that need recursive resolution, select the domain name requests with the maximum number of concurrent recursive queries that the current recursive server can handle to respond, and the domain name query requests that are not selected will be directly discarded.
[0049] Specifically, for requests without a cache hit, the recursive server will initiate recursive queries to obtain the results of these queries. Count the number M of recursive query domain name resolution requests that need to be initiated by the current recursive server (that is: the total number of current DNS requests-Cache hits). When M is greater than N, the recursive server will use each C= Select one of the M / N (rounded up) requests to respond to, and the domain name query requests that are not selected for execution will be discarded directly. (such...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com