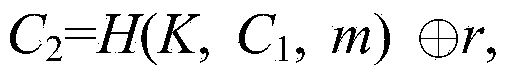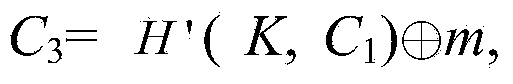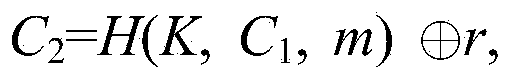ABOOE method capable of being proved to be safe
An encryption method and attribute technology, applied in the construction field of ABOOE
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] 1. At first introduce the definition of relevant basic knowledge with the method of the present invention, mainly comprise
[0017] Symmetric bilinear pair definition: let and is the multiplicative cyclic group of order large prime number p, g is The generator of , if there is a mapping e: Satisfy the following conditions: (1) bilinear: for e(u a ,v b )=e(u,v) ab ; ⑵ Non-degenerate: e(g, g)≠1; ⑶ Calculability: There exists an efficient algorithm to compute e(u,v) in polynomial time; then the above mapping e is said to be a symmetric bilinear pairing.
[0018] l-DBDHI hypothesis definition: The l-DBDHI problem is in The above definition is: randomly select α∈Z p * , g is The generator of , given a (l+2) tuple Determine whether the value of T is e(g,g) 1 / α . If for any probabilistic polynomial time (PPT) algorithm exist The advantages of solving the l-DBDHI problem above are all negligible, then the l-DBDHI hypothesis is said to be in abov...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com