Methods and nodes for random access
A technology of random access and random access response, applied in electrical components, wireless communication, network topology, etc., to achieve the effect of improving accuracy, network planning and/or coverage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment A
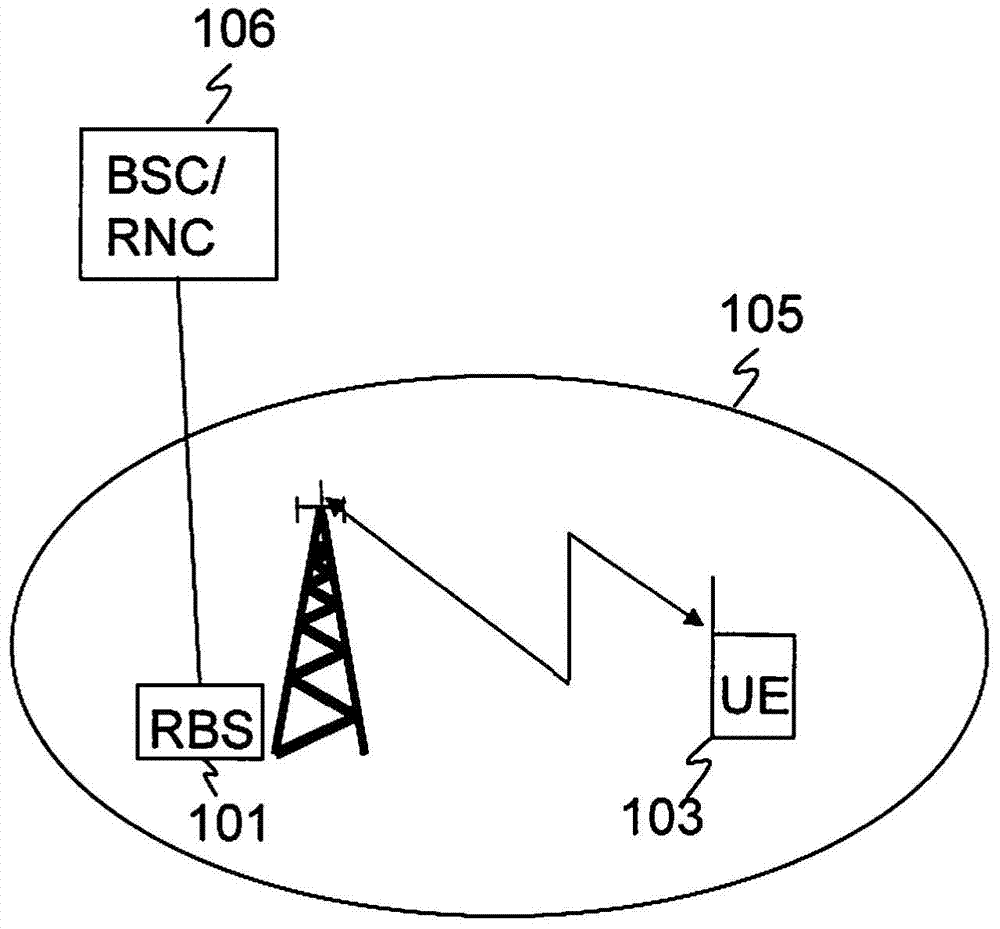
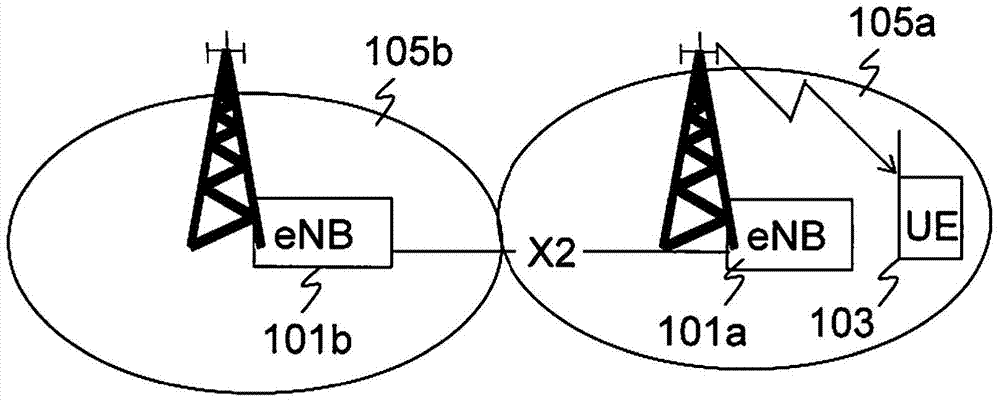
[0143] Embodiment A is particularly useful in scenarios where a victim cell such as a pico eNodeB or relay node receives high interference from an aggressor cell such as a macro eNodeB or aggressor UE on both DL and UL. However, embodiments are not limited to scenarios with both DL and UL ABS subframes.
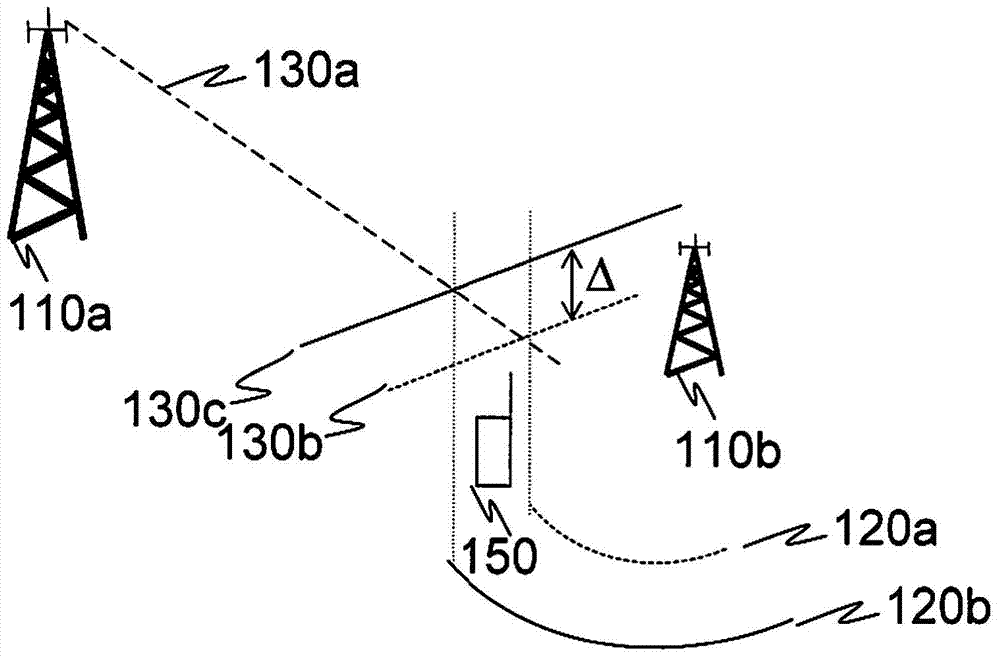
[0144] according to Figure 8b In the first aspect of embodiment A shown in the first RACH 801, the legacy RACH is at a first time-frequency location, while the second RACH 804, the ABS RACH or alternatively the restricted mode RACH is configured at a second frequency- time position. The location of the second RACH 804 overlaps with UL low-interference frequency-time resources, such as UL ABSs associated with the aggressor UE in the aggressor cell. This results in low interference at the victim base station when it receives transmissions on the second RACH 804 .
[0145] The second RACH position is thus suitable for UEs located in the extended cell range segment. UEs loca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com