Method for rapidly detecting and positioning illegal base station intrusion
An illegal base station and positioning method technology, applied in the field of wireless networks, can solve the problems of lack of accurate location of attacking mobile phones, high cost of drive testing, and inability to locate illegal base stations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
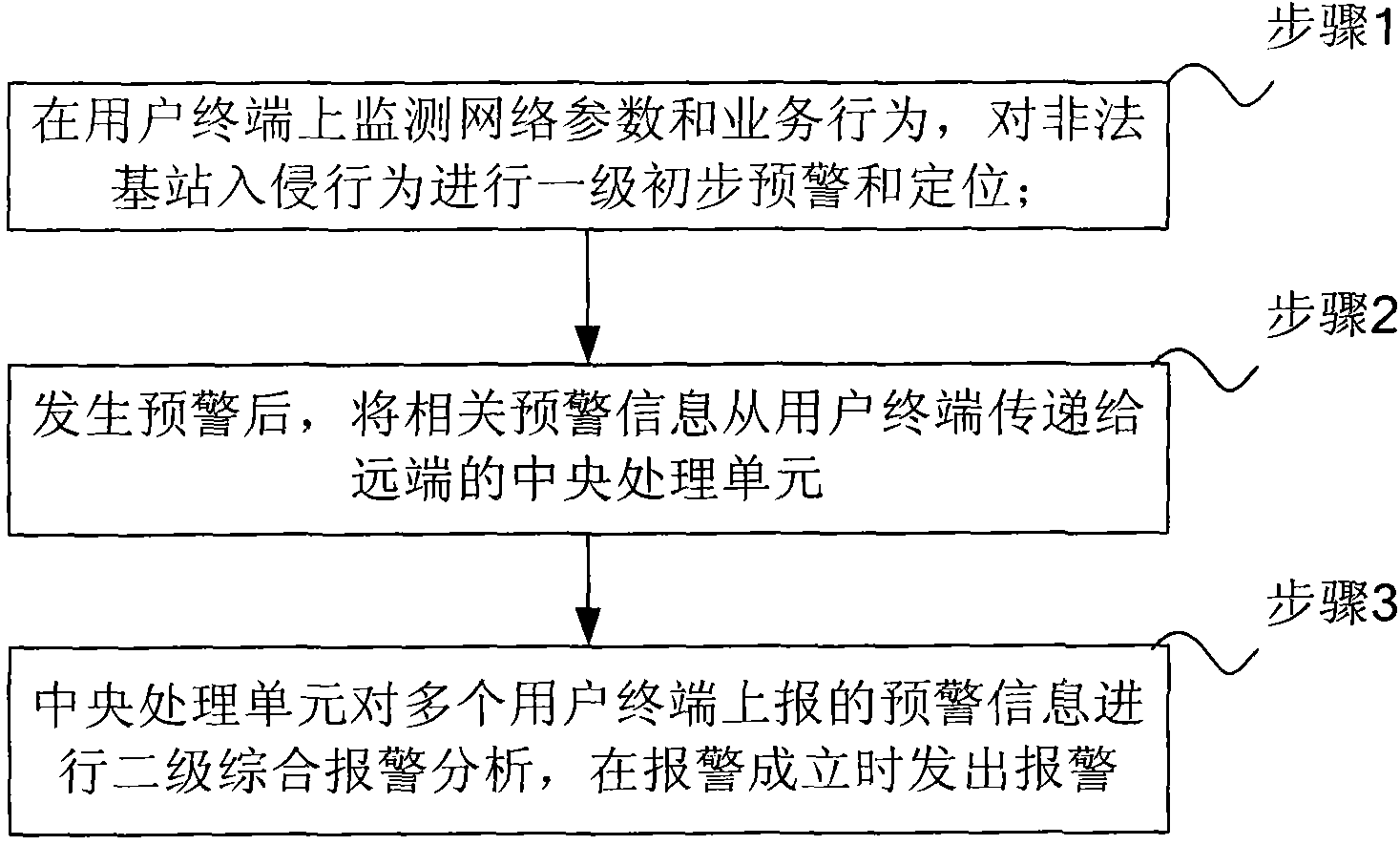
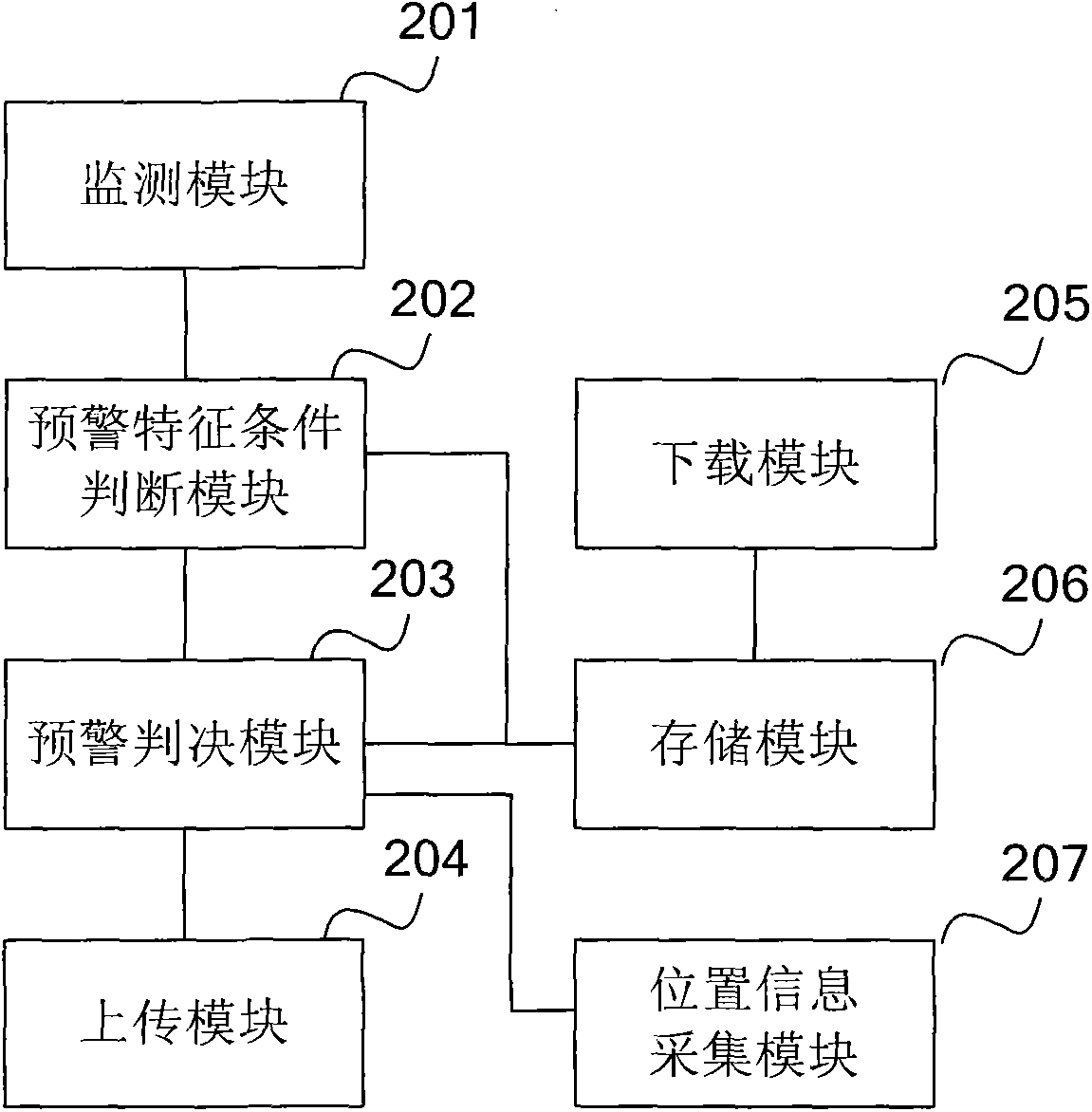
[0059] In order to make the purpose, technical solution and advantages of the present invention more clear, the present invention will be further described in detail below with reference to the accompanying drawings and examples.
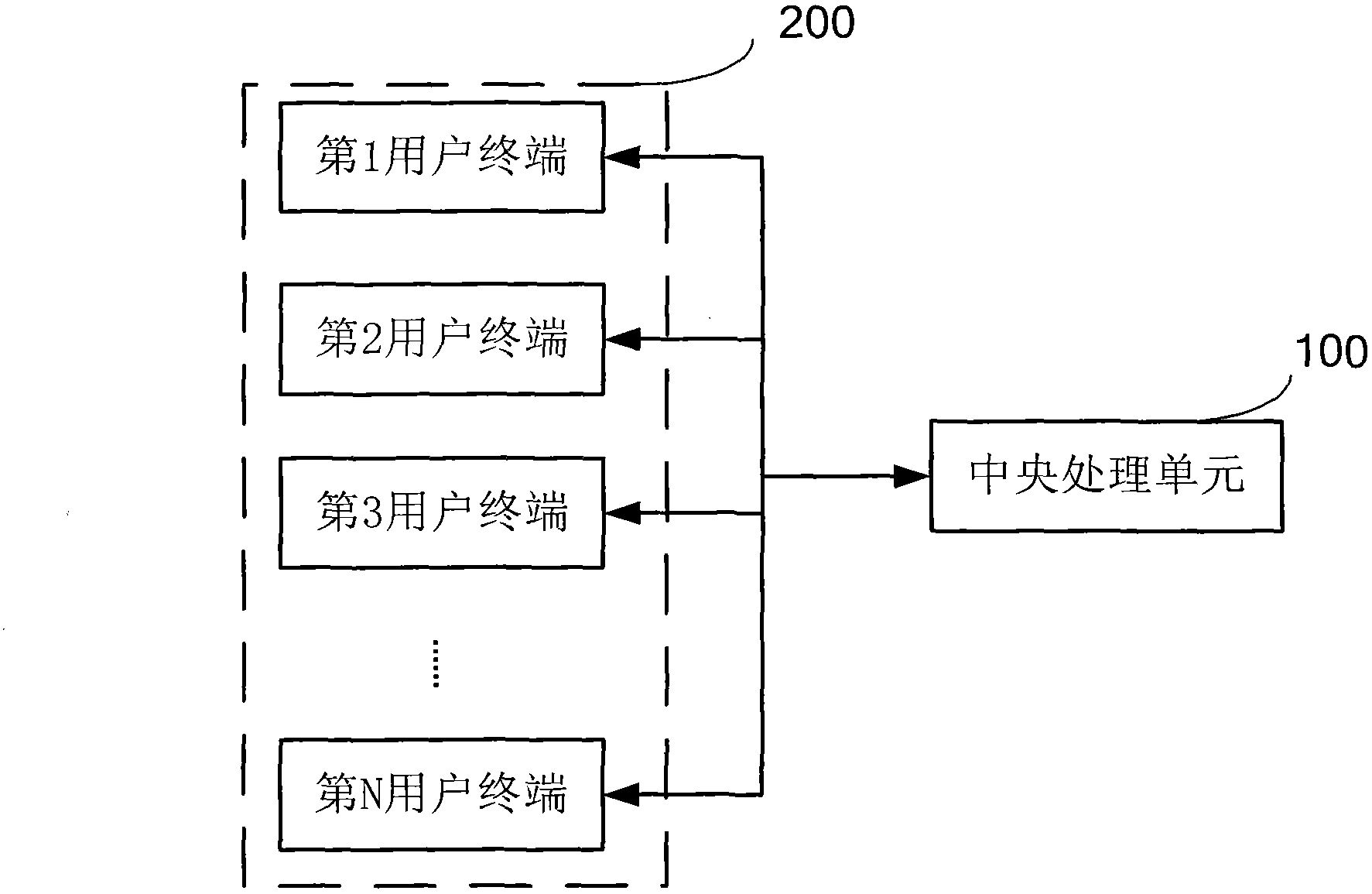
[0060] Such as figure 1 As shown, the illegal base station intrusion detection and positioning system in the present invention includes a central processing unit 100 and a plurality of user terminals 200 corresponding to it and performing information interaction. The user terminals 200 include a first user terminal, a second user terminal, a 3 user terminals...the Nth user terminal. figure 1 Among them, there are N user terminals, where N≥1, and the number depends on the needs of system deployment. figure 1 What is shown is for illustrative purposes only, and is not intended to limit the content of the present invention.
[0061] figure 1 Among them, the user terminal 200 collects the network parameters and business sending and receiving informat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com