Method and device for portal authentication
A portal authentication and user identity authentication technology, applied in the field of portal authentication methods and devices, can solve the problems of users failing to go online, administrators cannot manage users centrally, Portal users cannot pass authentication, etc., so as to meet the needs of centralized management. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
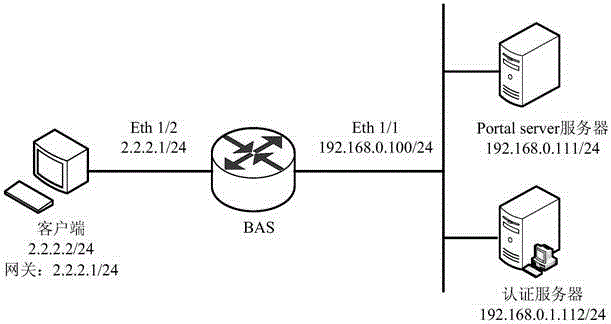
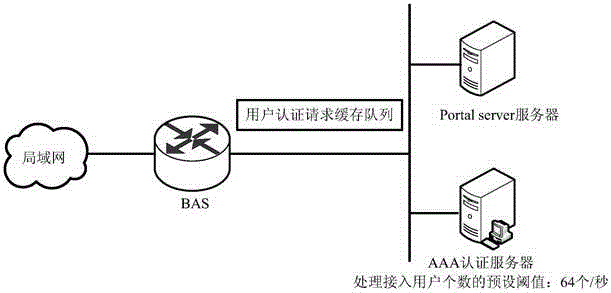
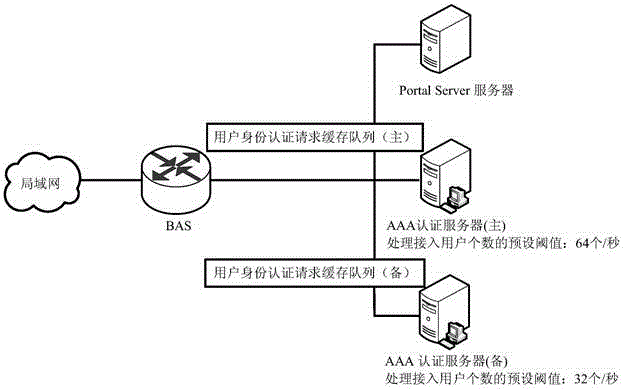
[0067]Method Embodiment 1 Taking the networking of a single AAA authentication server as an example, the technical solution of the present invention is described. In practical applications, operators will also form AAA authentication servers into server groups, that is, one master and multiple backups. When the master server is down , the standby AAA authentication server performs authentication and billing for subsequent users. In this embodiment, a master and a backup AAA authentication server dynamically create a user cache and a scheduling mechanism as an example to further illustrate the technical solution of this embodiment. The preset threshold corresponding to the number of access users processed by the primary AAA authentication server is 64 per second, the preset threshold corresponding to the number of access users processed by the standby AAA authentication server is 32 per second, and the BAS waits for a fixed period of time for authentication responses If the valu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com