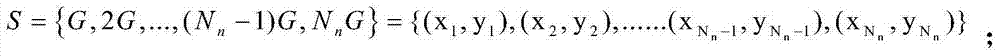Combination public key authentication password method based on conic curves
A technology of conic section and combined public key, which is applied in the field of authentication cryptography based on conic section combined public key, and can solve the problems of configuring complex cloud computing environment and so on.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be further described below in conjunction with the accompanying drawings.
[0030] For realizing above-mentioned technical task, the technical solution that the present invention takes the following steps:
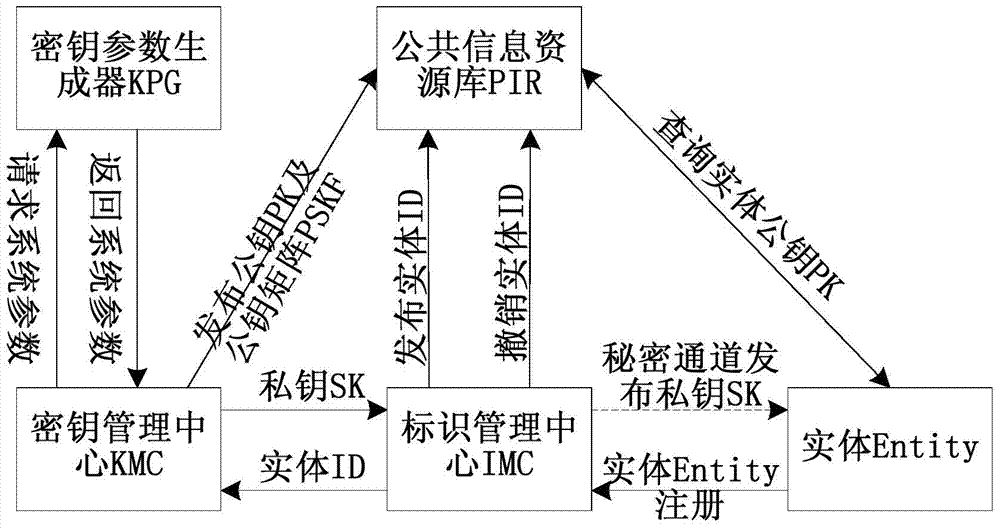
[0031] Step 1. Generate a ring based on the remaining class Public cryptographic parameters of conic sections
[0032] Assume is a remainder-like ring modulo n, defining the ring Conic section C on n (a,b) is the congruence equation y 2 ≡ax 2 -bx(mod n) in The solution set above, where a, b∈Z, (a, n)=(b, n)=1, n=pq, p, q are two different large odd prime numbers, mod is a modulo operation; the origin O =(0,0)∈C n (a,b), remember If satisfied And p+1=2r, q+1=2s, r and s are prime numbers, then the curve C n (a,b) exists a point G whose order N n =lcm{|C p (a,b)|,|C q (a,b)|}={p+1,q+1}=2rs, where lcm(x,y) is the function for calculating the least common multiple, |C p (a,b)| and |C q (a,b)|respectively are the conic c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com