Processing method and device for transaction sensitive information
A technology of sensitive information and processing method, which is applied in the field of processing method and processing device of transaction sensitive information, can solve the problems of forged transactions, being rewritten, etc., and achieves the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0029] The inventor of this case proposes that the encrypted font content can be stored in a non-updatable manner, so that during the transaction process, the electronic signature device searches the decrypted font file for the characters corresponding to the transaction-sensitive information to be displayed in a table look-up manner. Afterwards, the found characters are encrypted and displayed, thereby greatly improving the security of the electronic signature device.
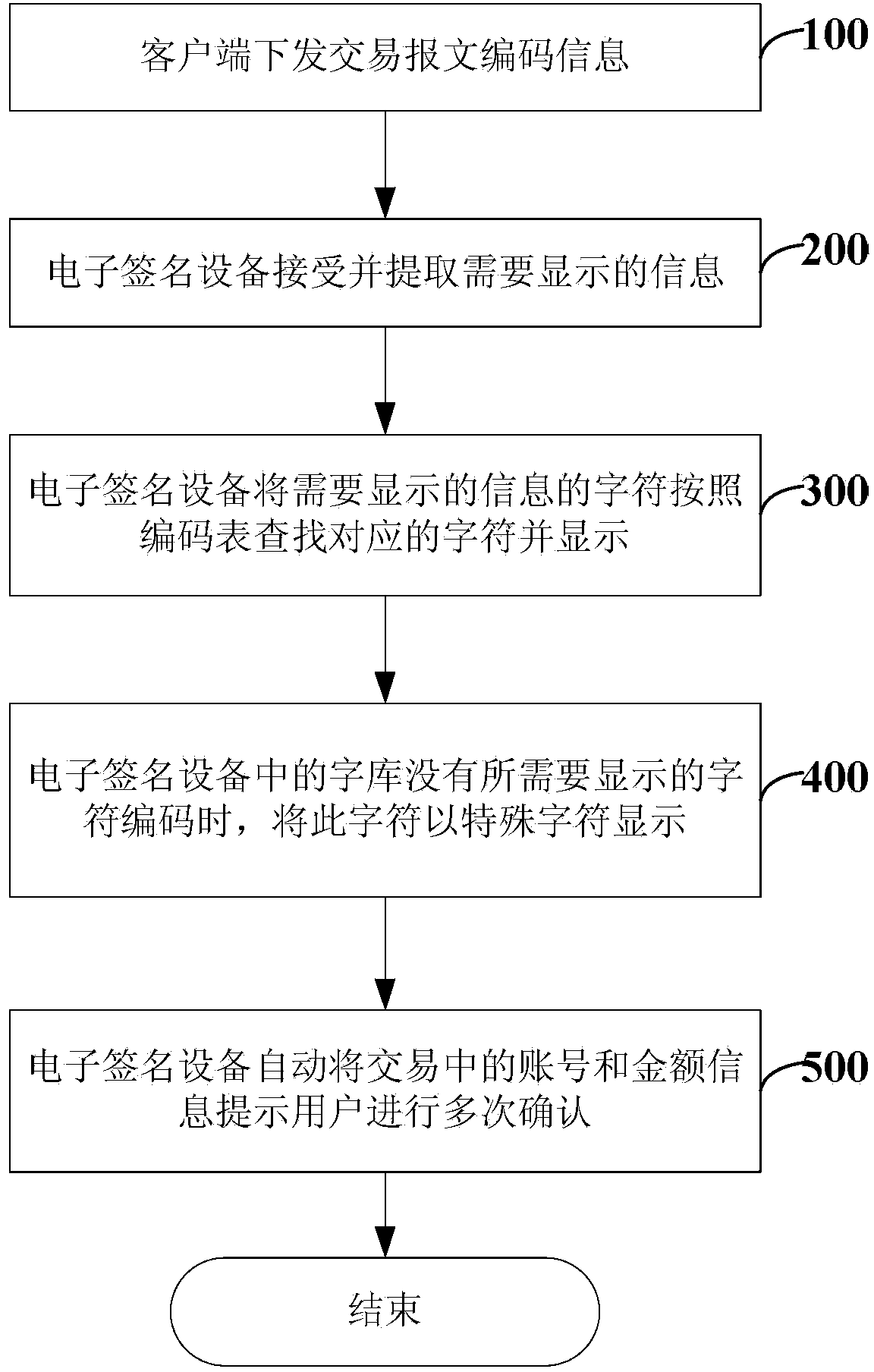
[0030] Based on the above ideas, this embodiment provides a method for processing transaction sensitive information, including the following operations:
[0031] The online banking client running on the PC or smart terminal device sends the transaction message encoding information, and the electronic signature device receives the transaction message encoding information and extracts the transaction sensitive information that needs to be displayed;
[0032] The electronic signature device decrypts the pre-encry...
Embodiment 2
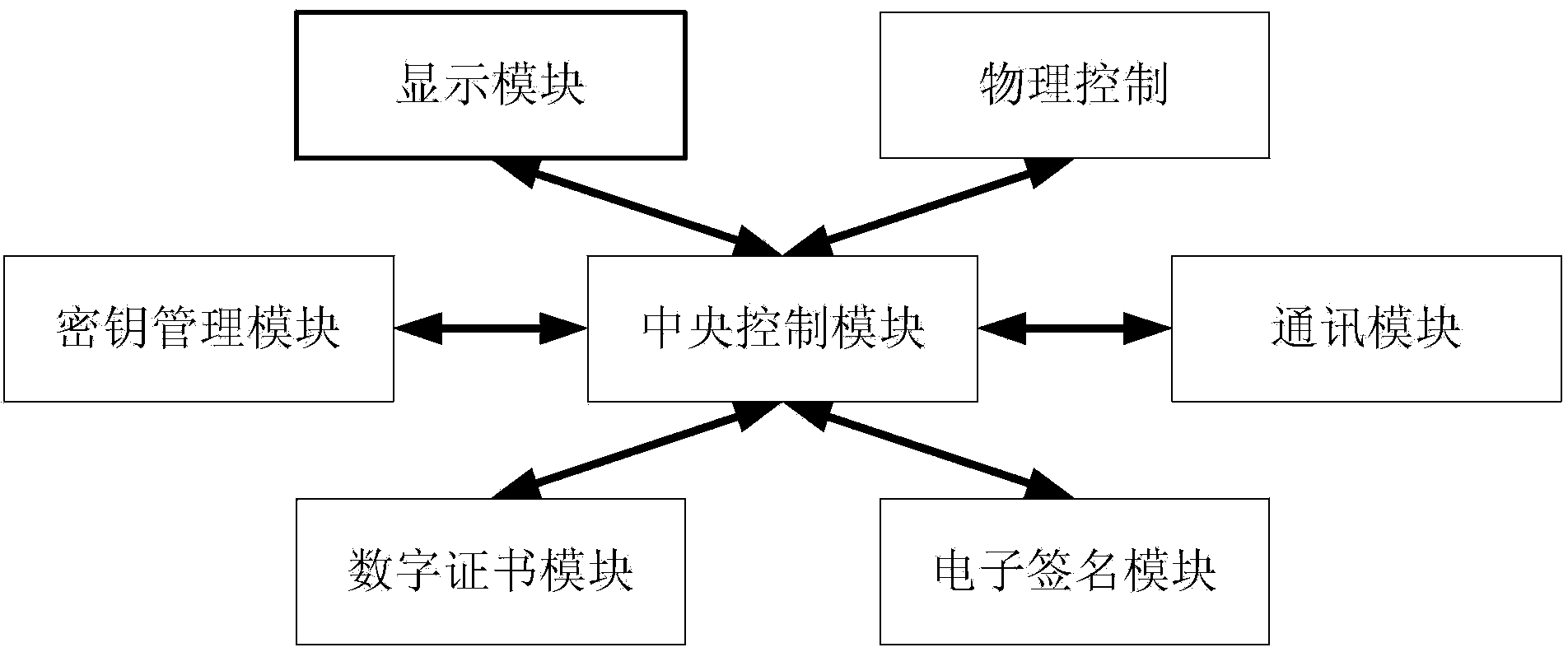
[0076] This embodiment provides a transaction sensitive information processing device, its structure is as follows image 3 As shown, it includes at least the following three units:
[0077] The first unit extracts transaction sensitive information from the received transaction message encoding information;
[0078] The second unit decrypts the encrypted font file according to a preset decryption method, and then searches for the character corresponding to the transaction sensitive information from the decrypted font file;
[0079] The third unit encrypts and displays the found characters.
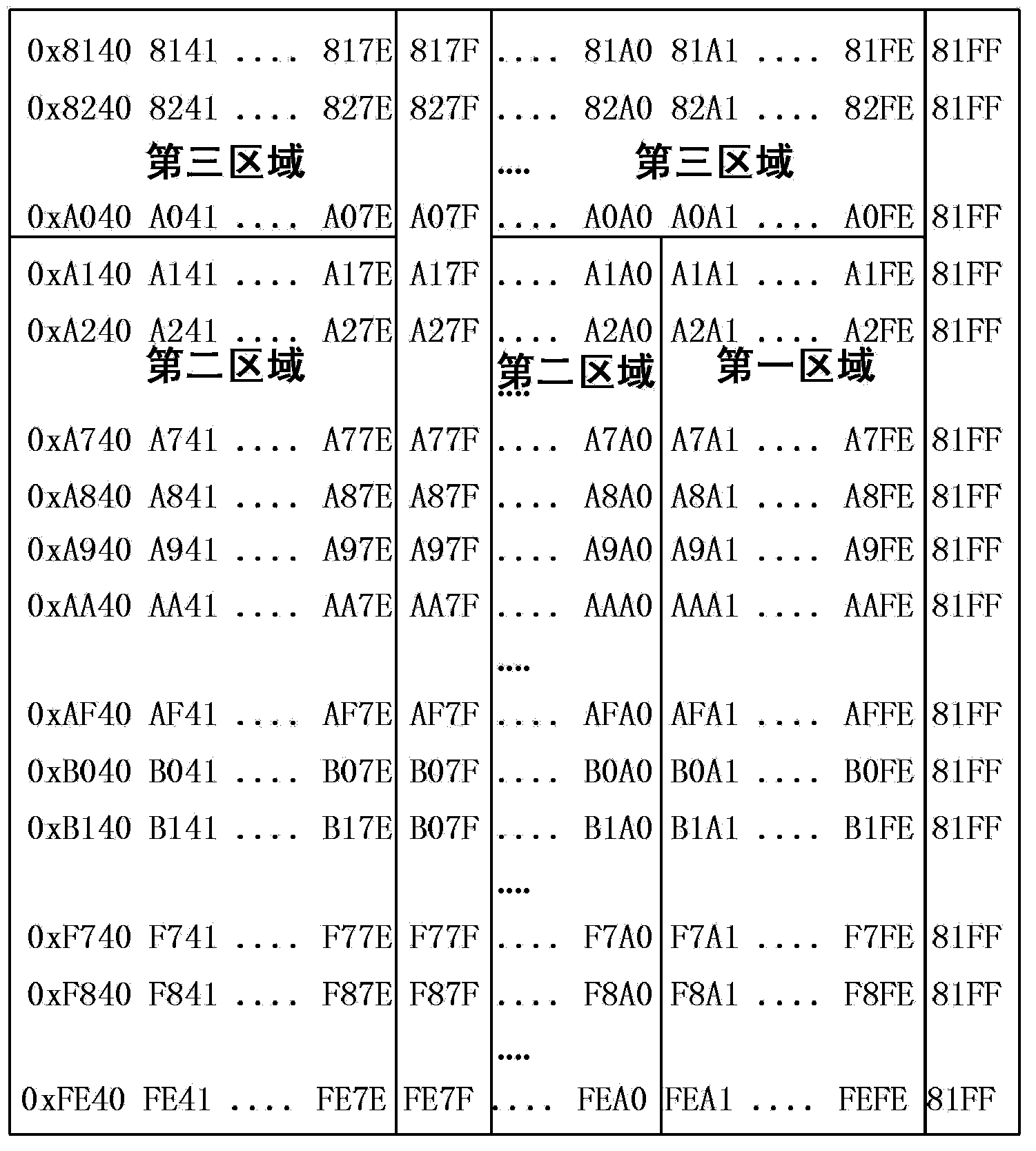
[0080] Specifically, the above-mentioned second unit, the process of finding the characters corresponding to the transaction-sensitive information from the decrypted font file is to first perform binary conversion on the characters of the transaction-sensitive information, and convert the internal code of the character to be displayed into For the location code, it is sufficient to searc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com