Webpage tamper-proofing device and method based on access control and directory protection
A tamper-proof and directory technology, applied in the field of network security, can solve problems such as security risks, and achieve the effect of ensuring security, preventing tampering, and ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
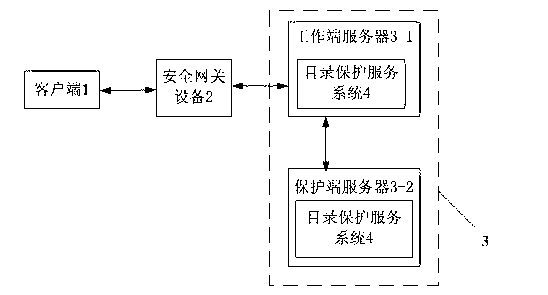
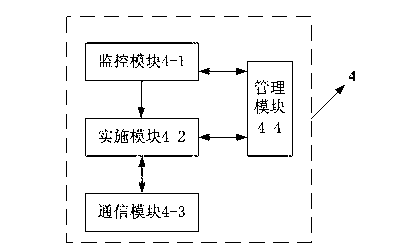
[0046] Such as figure 1 , figure 2 As shown, a webpage anti-tampering device based on access control and directory protection includes a client 1 and a server 3, and the client 1 is interactively connected with the server 3 through a security gateway device 2; the server 3 is composed of The working end server 3-1 for providing Web services to the client through the security gateway device is composed of an interactive connection with the protection end server 3-2 for receiving information, sending operation instructions and updating system files; the working end server 3 -1 is interactively connected with the client 1 through the security gateway device 2; the working server 3-1 and the protection server 3-2 are equipped with a directory protection service system 4, and the working server 3-1 and the protection server 3-2 Perform an interactive connection through the directory protection service system 4 . The directory protection service system 4 includes a monitoring mod...
Embodiment 2
[0048] A webpage anti-tampering method based on access control and directory protection, comprising the following steps:
[0049] (1) Use the security gateway device between the client and the server to determine the user's access rights, and at the same time encrypt the data during network transmission;
[0050] (2) The working-end server monitors the changes of directories or files in its operating system, and first judges whether the protection-end server actively notified it. If so, the working-end server executes the file for synchronous update; Send the changed directory or file information to the protection server;
[0051] (3) The protection server analyzes the file referred to by the received message by a hash table fast search algorithm, compares its hash value with the file hash value sent by the working server, and if they are the same, executes the file operation; if different, it is determined that the file is illegally tampered with, and the result is sent to t...
Embodiment 3
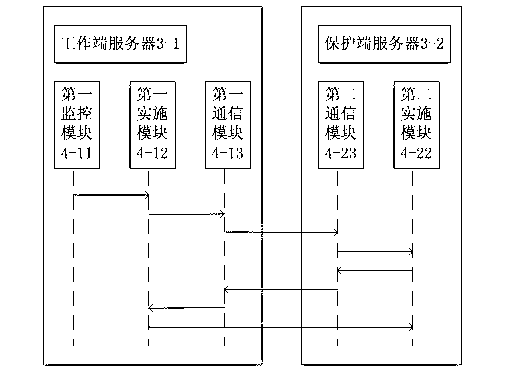
[0054] Such as image 3 As shown, the specific working process of the webpage anti-tampering device is to first judge whether it is the protection end after the first monitoring module 4-11 of the directory protection service system 4 inside the working end server 3-1 monitors that there is a directory or file change. If the server actively notifies, if not, execute the anti-tampering process:
[0055] (1) The working server 3-1 sends the changed directory or file information to the protection server 3-2, and notifies the first communication module 4-13 through the first implementation module 4-12; the first communication module 4-13 After registering the message, the message is sent to the second communication module 4-23 of the protection server 3-2;
[0056] (2) After the second communication module 4-23 receives the message, it forwards the message to the second implementation module 4-22; the second implementation module 4-22 analyzes the file referred to in the received...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com