E-mail encryption method, mail server and system
A mail server and e-mail technology, applied in the field of communication security, can solve problems such as too simple passwords, stolen mailbox passwords, and users lack of awareness of security protection, and achieve the effect of ensuring security and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
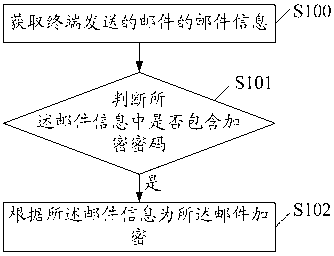
[0025] figure 1 It is a flow chart of the first embodiment of an email encryption method of the present invention, including:
[0026] S100, acquiring mail information of the mail sent by the terminal.
[0027] The email information includes recipients, subject, body and attachments. The user sends an email to the mail server through the terminal, and the email information includes the recipient, title and body. At the same time, the user can add attachments to the email, and the number of attachments can be one or more.
[0028] S101. Determine whether the email information contains an encrypted password.
[0029] It should be noted that not all emails need to be encrypted. The user only encrypts the emails that need to be encrypted and submits the encrypted password. After the user submits the encrypted password, the encrypted password will be stored in the email message. After obtaining the mail information of the mail sent by the terminal, the mail server needs to deter...
no. 2 example
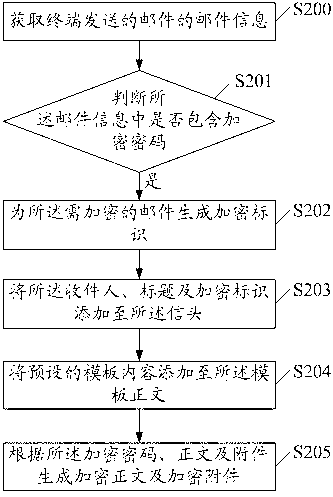
[0038] figure 2 It is a flow chart of the second embodiment of an email encryption method of the present invention, including:
[0039]S200. Obtain email information of the email sent by the terminal.
[0040] The email information includes recipients, subject, body and attachments.
[0041] S201. Determine whether the email information contains an encrypted password.
[0042] It should be noted that not all emails need to be encrypted. The user only encrypts the emails that need to be encrypted and submits the encrypted password. After the user submits the encrypted password, the encrypted password will be stored in the email message. After obtaining the mail information of the mail sent by the terminal, the mail server needs to determine whether the encrypted password is included in the mail information.
[0043] When the mail server judges that the mail information does not contain an encryption password, it means that the mail does not need to be encrypted and can be s...
no. 3 example
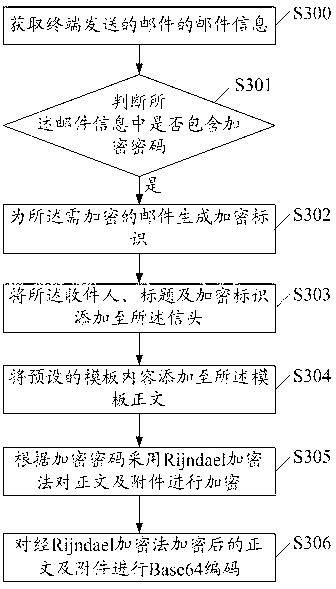
[0055] image 3 It is a flow chart of the third embodiment of an email encryption method of the present invention, including:
[0056] S300. Obtain email information of the email sent by the terminal.
[0057] The email information includes recipients, subject, body and attachments.
[0058] S301. Determine whether the email information contains an encrypted password.
[0059] It should be noted that not all emails need to be encrypted. The user only encrypts the emails that need to be encrypted and submits the encrypted password. After the user submits the encrypted password, the encrypted password will be stored in the email message. After obtaining the mail information of the mail sent by the terminal, the mail server needs to determine whether the encrypted password is included in the mail information. When the mail server judges that the mail information does not contain an encryption password, it means that the mail does not need to be encrypted and can be sent direct...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com