Migration of credentials and/or domains between trusted hardware subscription modules
A certificate and destination technology, applied in the direction of electrical components, wireless communication, security devices, etc., can solve problems such as restrictions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
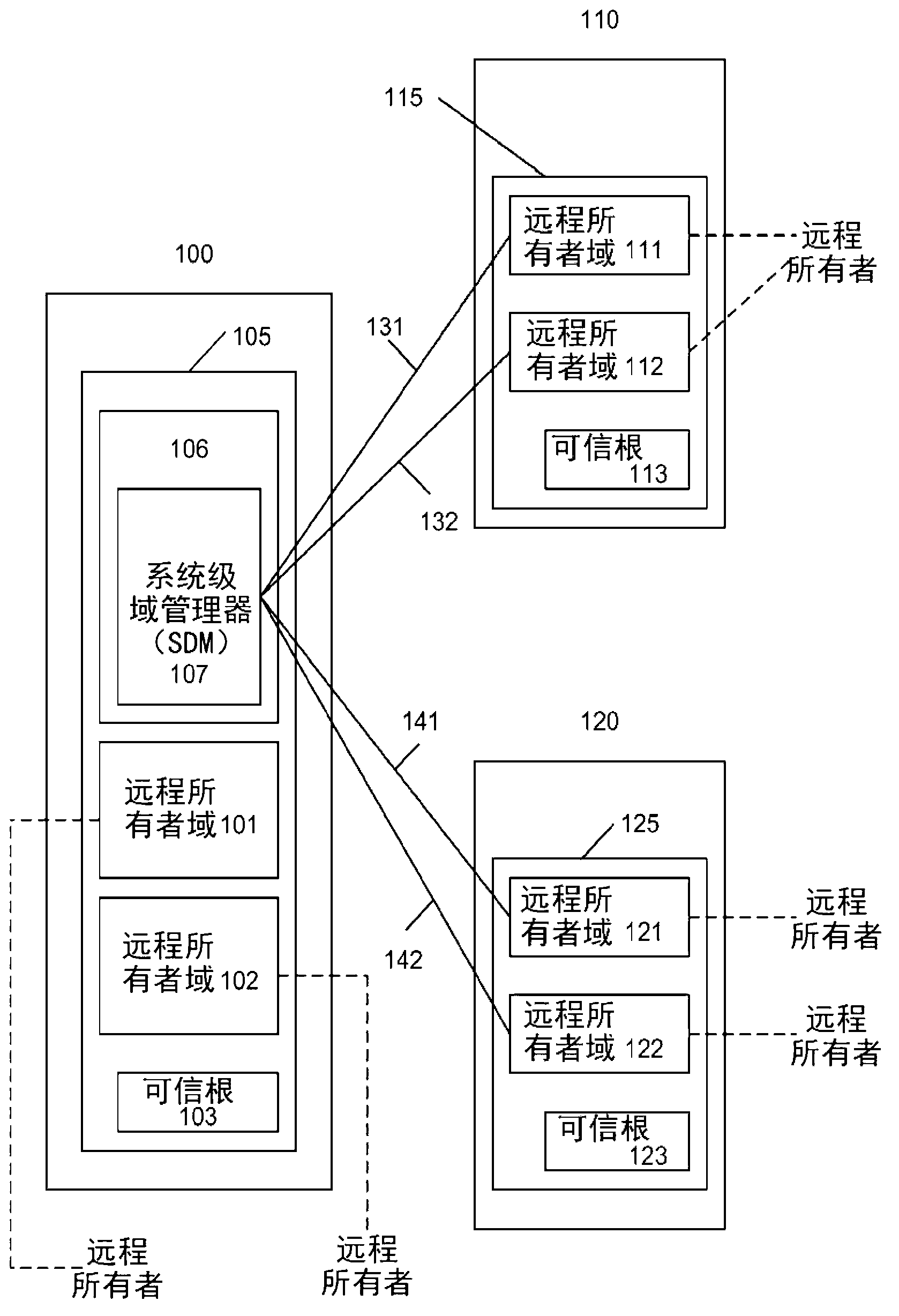
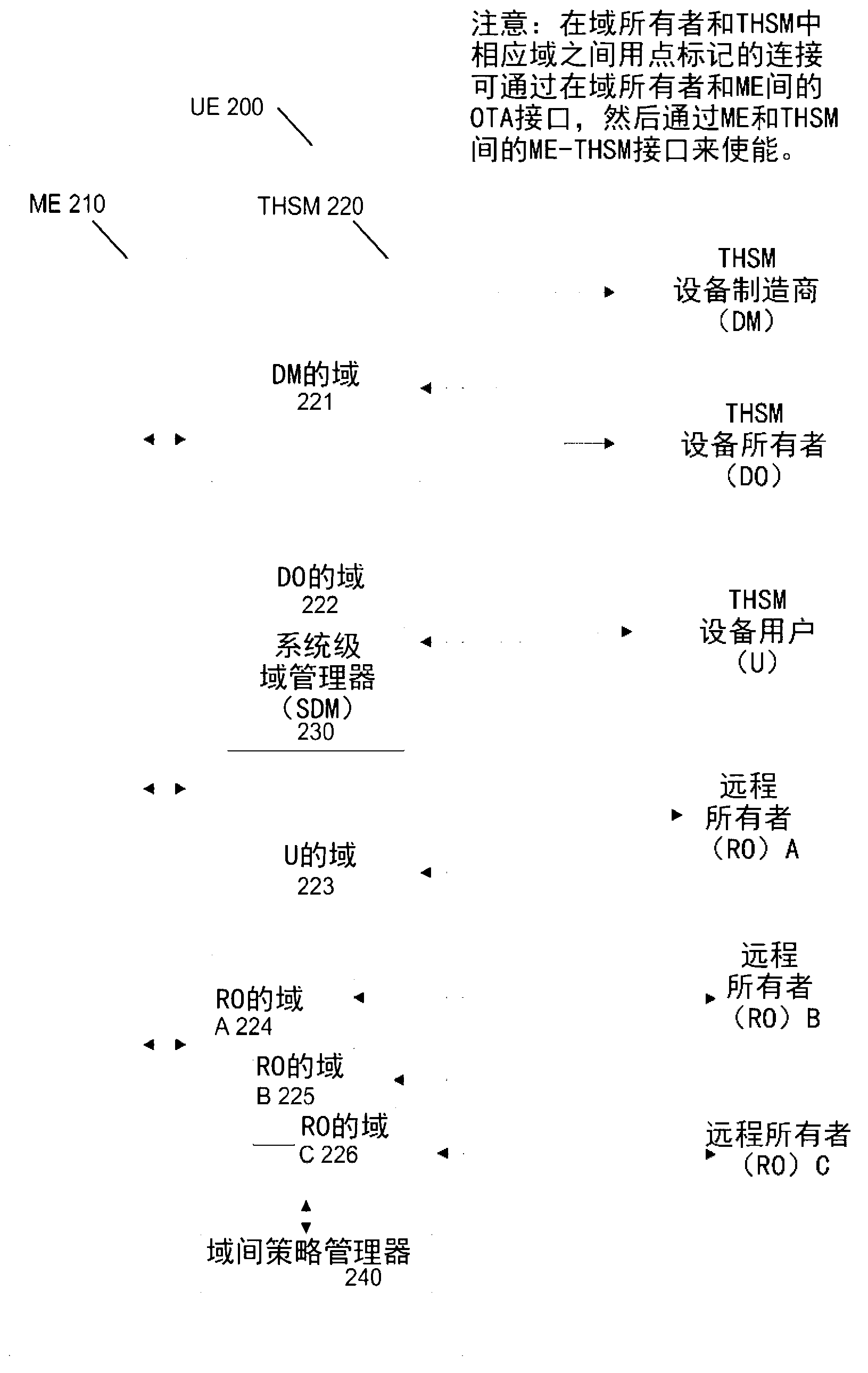
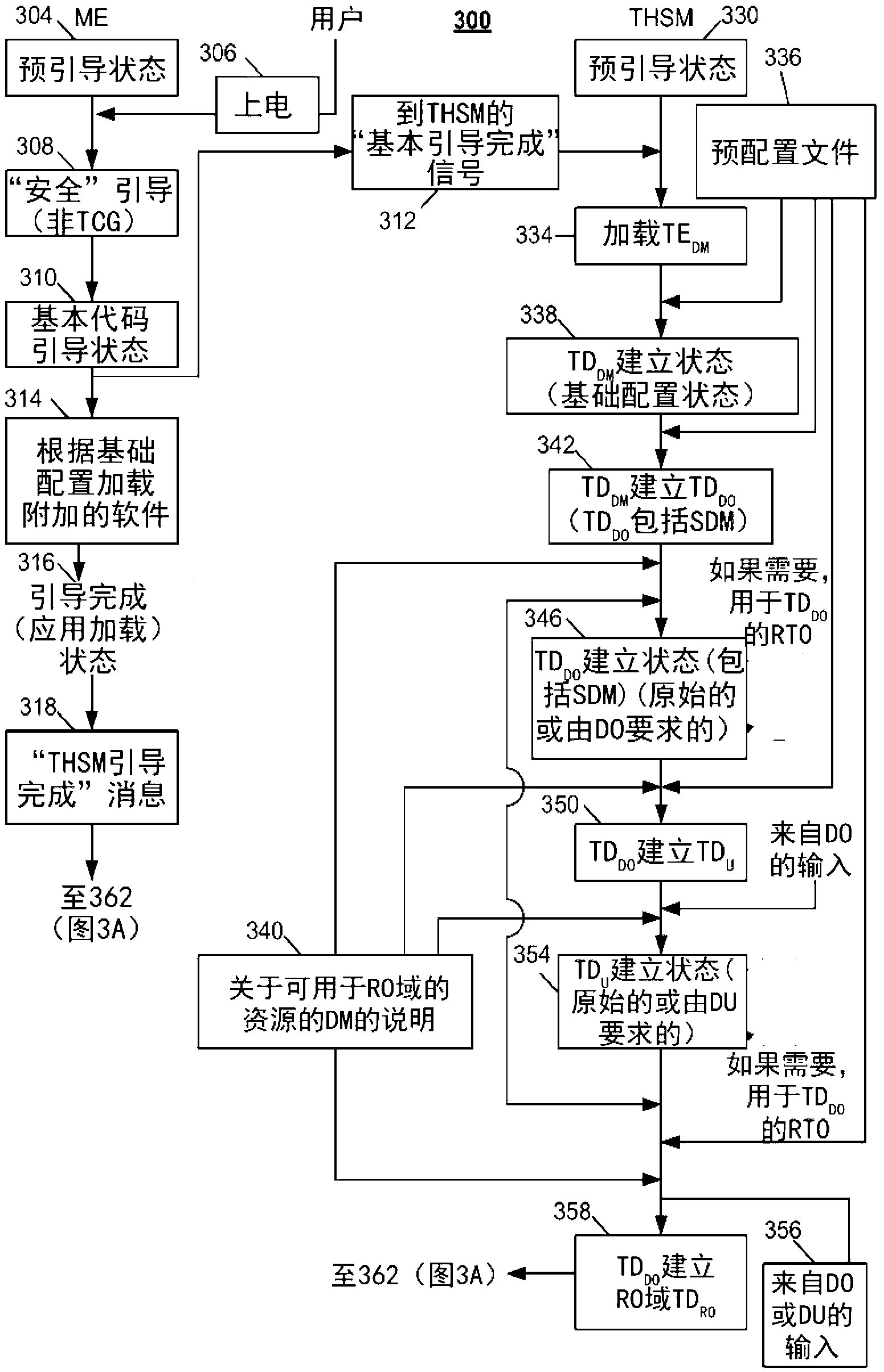
[0022] figure 1 -9 may relate to example embodiments in which the disclosed systems, methods and means may be implemented. However, while the present invention may be described in conjunction with example embodiments, it is not limited thereto and it should be understood that other embodiments may be used, or that modifications and additions may be made to the described embodiments to achieve the same functionality of the present invention, without out of the invention. Furthermore, the figures may illustrate call flows, which are intended to be examples. It should be understood that other embodiments may be used. Additionally, the order of the flows may be changed as appropriate. Also, the flow can be omitted if not needed, and additional flow can be added.
[0023] Systems, methods, and means are disclosed that allow users to migrate certificates from one domain to another. This migration can occur in a system that includes one or more devices with one or more separate ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com