Simple network management protocol (SNMP)-based terminal security access control method
A control method and terminal security technology, applied in the direction of digital transmission system, electrical components, transmission system, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
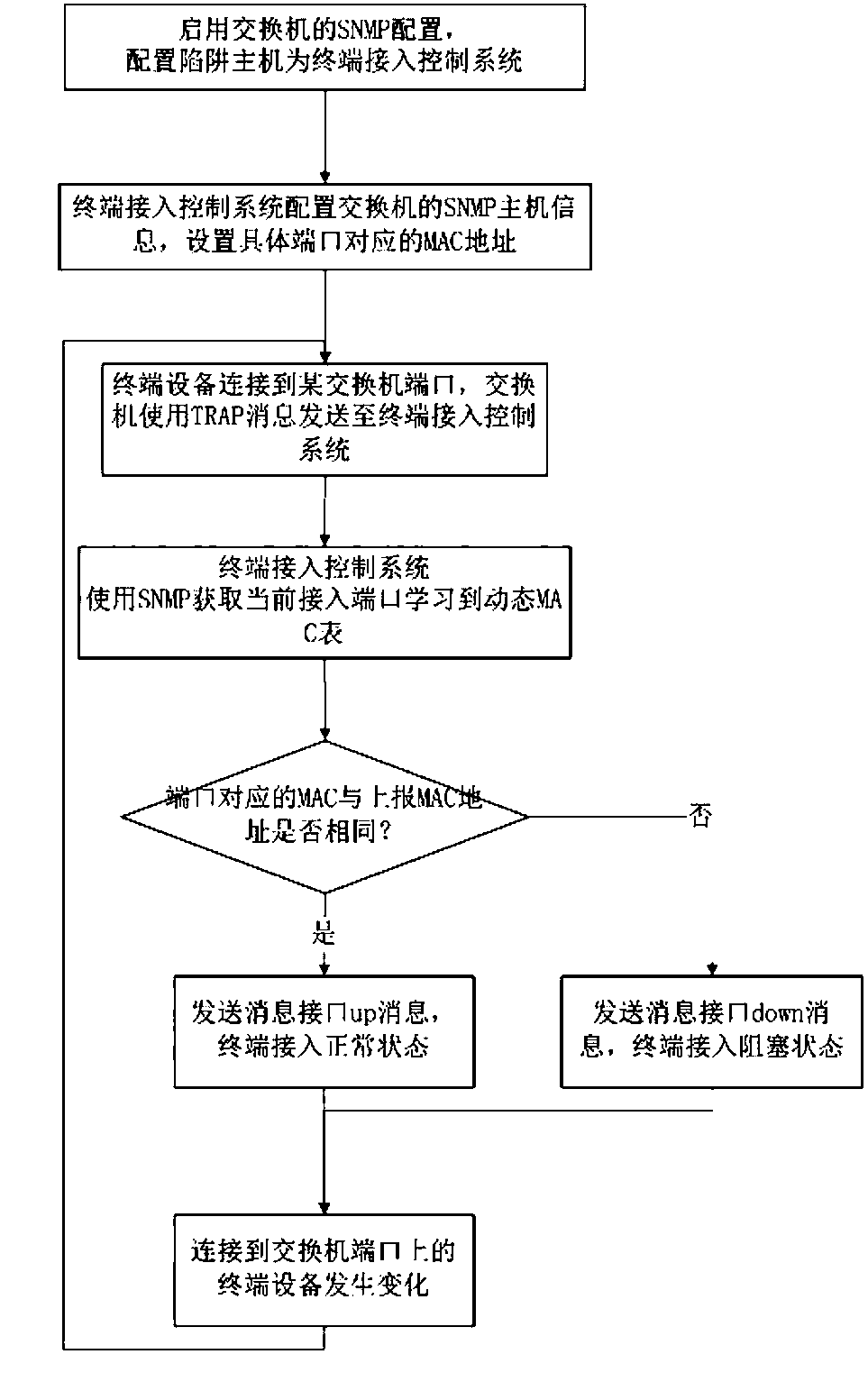
[0028] It mainly realizes the specific port binding between the terminal and the specific switch. In this method, the terminal access control system and the switch jointly realize the port access control. The specific method includes the following steps:
[0029] Step 1: Enable the SNMP module of the switch, configure the switch to trap the host as the terminal access control system, configure the SNMP host information of the switch in the terminal access control system, and set the legal MAC address corresponding to the specific port;
[0030] Step 2: The terminal device is connected to a certain switch port, and the switch uses a TRAP message to send the port access information to the terminal access control system;
[0031] Step 3: The terminal access control system uses SNMP to obtain the dynamic MAC table learned by the current access port, and compares and matches with the legal MAC address information corresponding to the port to determine whether the current port access...
Embodiment 2
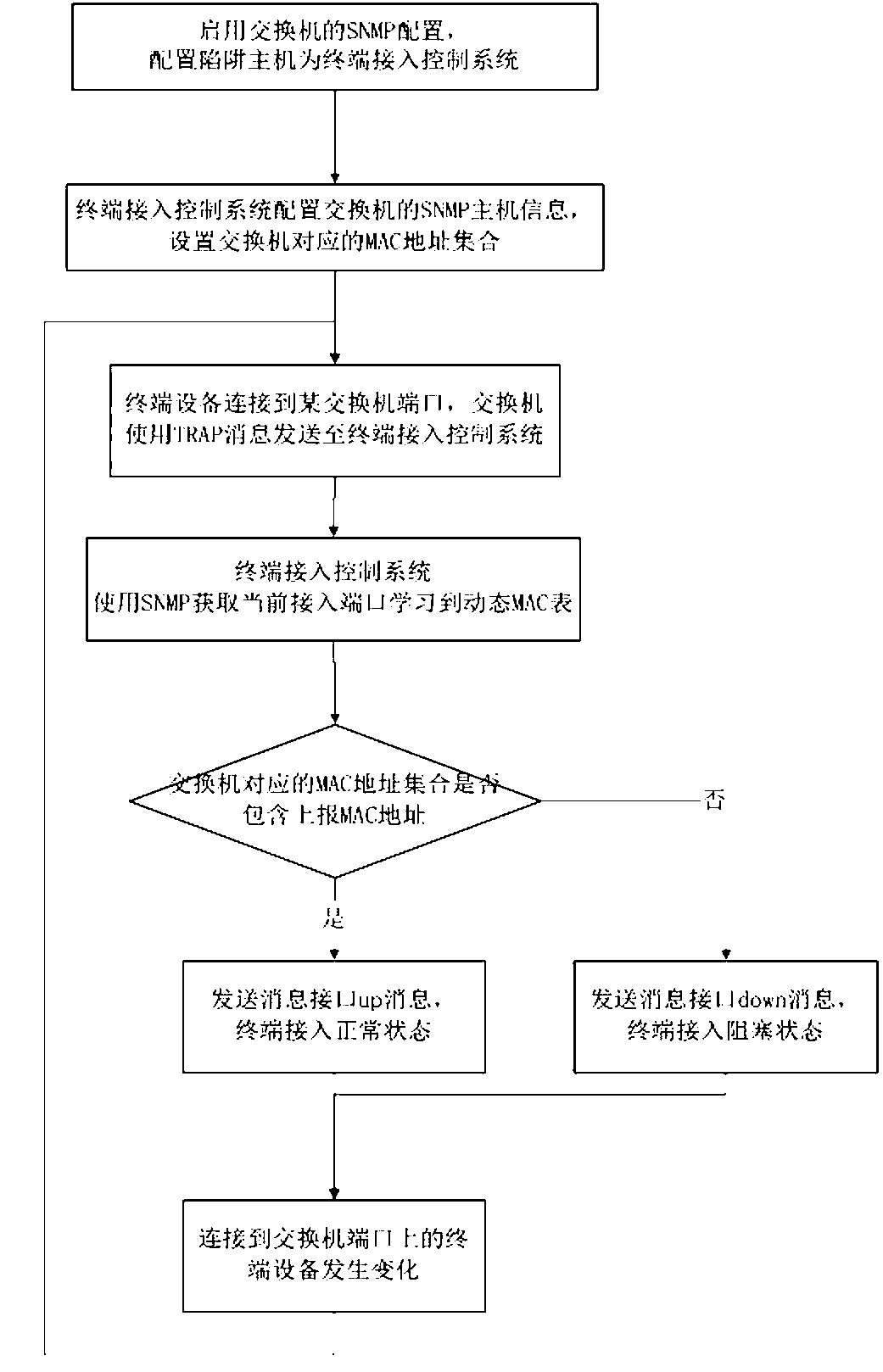
[0035] It mainly realizes the binding between the terminal and a specific switch. In this method, the terminal access control system and the terminal switch jointly realize the port access control. The specific method includes the following steps:
[0036] Step 1: Enable the SNMP module of the switch, configure the trap host on the switch as the terminal access control system, configure the SNMP host information of the switch on the terminal access control system, and set the legal MAC address set corresponding to the switch;
[0037] Step 2: The terminal device is connected to a certain switch port, and the switch uses a TRAP message to send the port access information to the terminal access control system;
[0038] Step 3: The terminal access control system uses SNMP to obtain the dynamic MAC table learned by the current access port, and compares and matches with the legal MAC address information corresponding to the switch to determine whether the current port access MAC add...
Embodiment 3
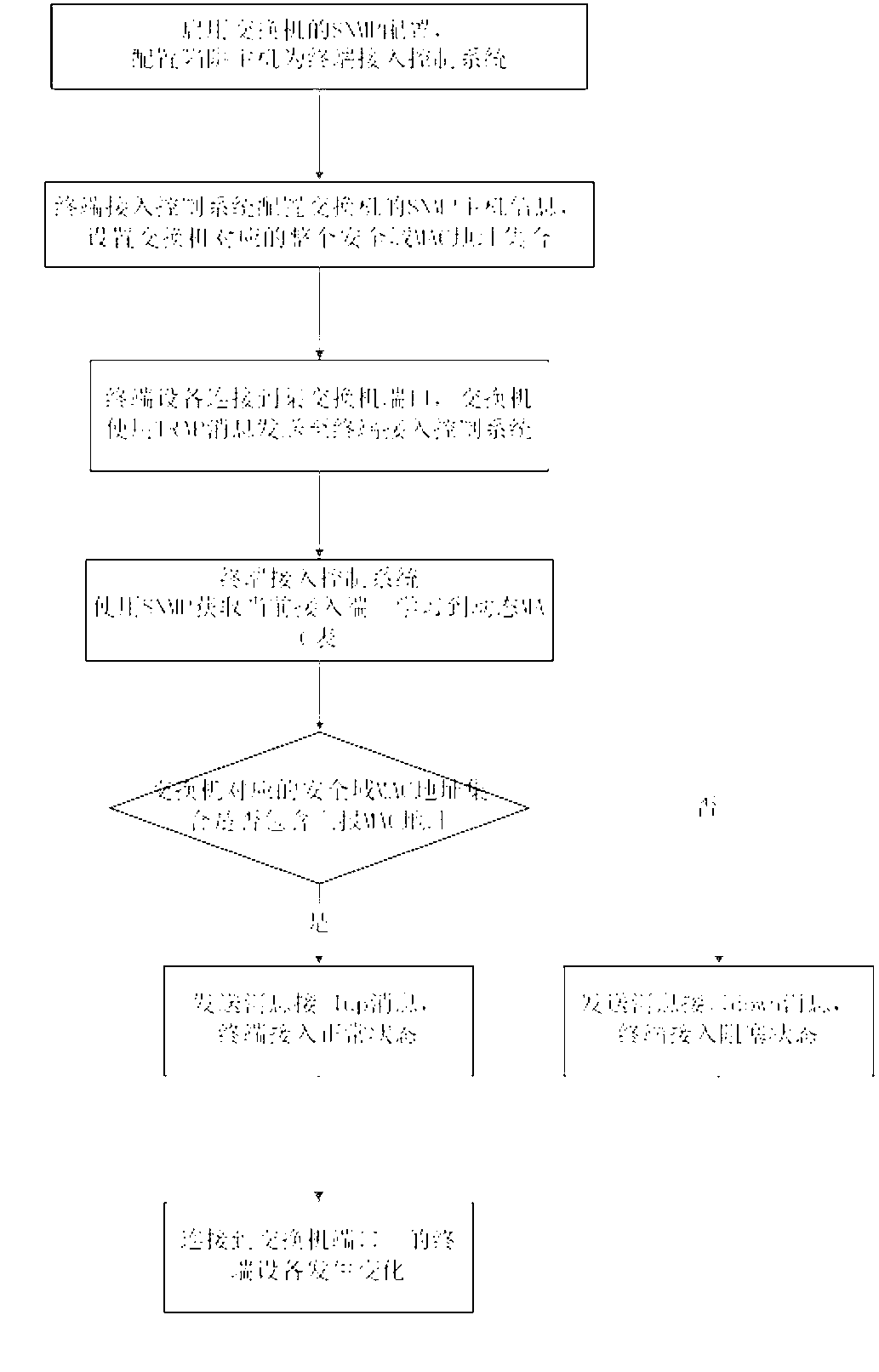
[0042] It mainly realizes the binding between terminals and all switches in a specific security domain. This method realizes port access control jointly by the terminal access control system and switches. The specific method includes the following steps:
[0043] Step 1: Enable the SNMP module of the switch, configure the switch to trap the host as the terminal access control system, configure the SNMP host information of the switch in the terminal access control system, and set the legal MAC address set of the entire security domain corresponding to the switch;
[0044] Step 2: The terminal device is connected to a certain switch port, and the switch uses a TRAP message to send the port access information to the terminal access control system;
[0045] Step 3: The terminal access control system uses SNMP to obtain the dynamic MAC table learned by the current access port, and compares and matches with the legal MAC address information corresponding to the entire security domain...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com