Malicious attack prevention method and browser
A malicious attack, browser technology, applied in the Internet field, can solve problems such as stealing operation rights and website harm
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
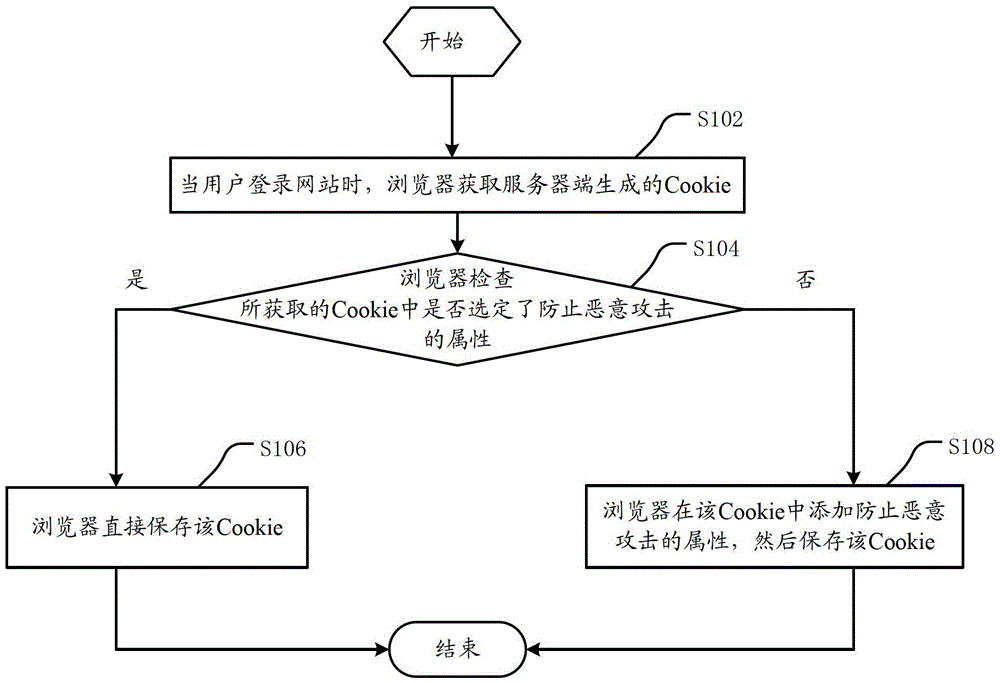
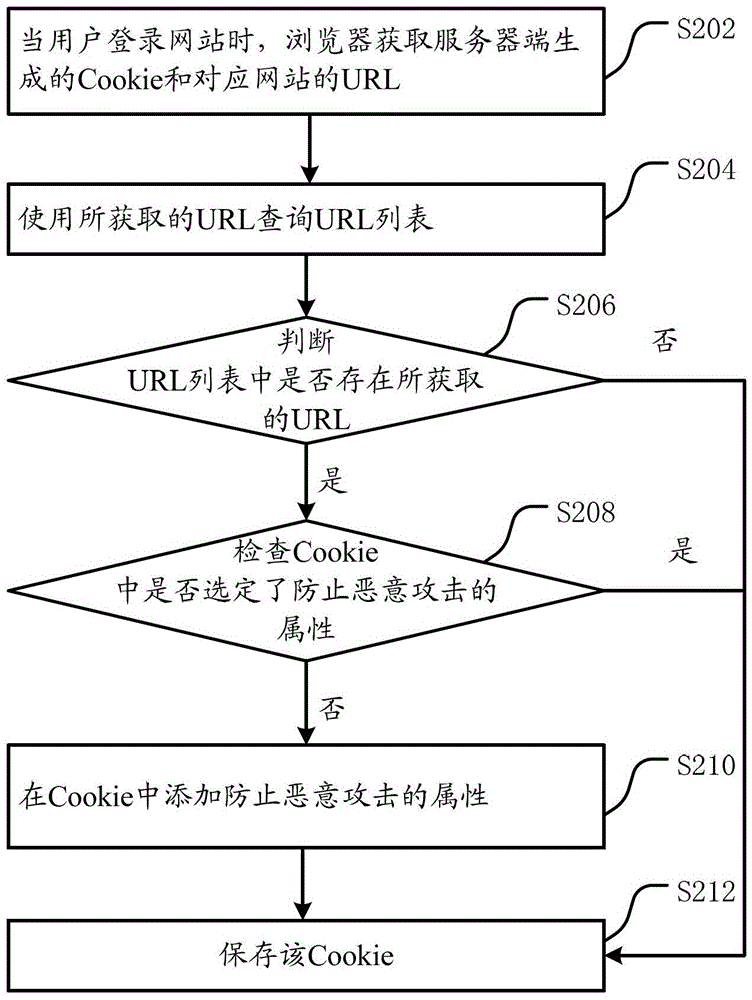
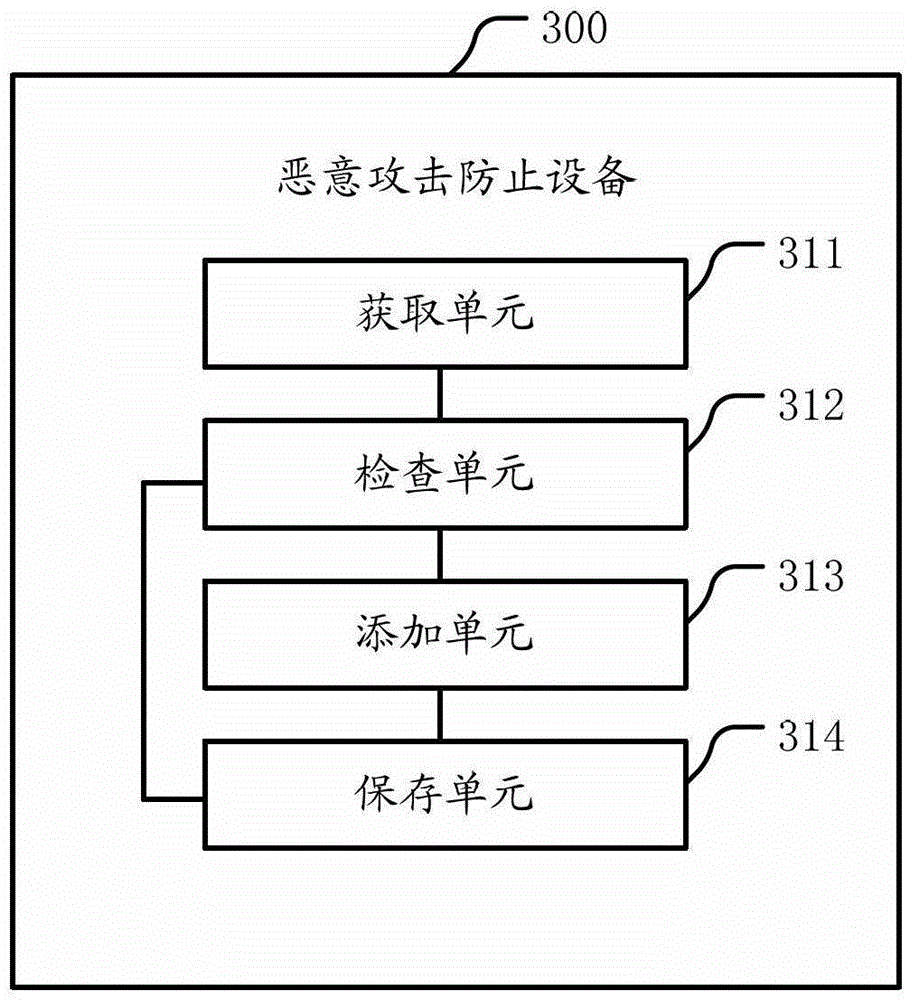
[0038] A cookie is a user's identity verification mark for a specific website. The server can use the arbitrariness of the information contained in Cookies to filter and maintain this information frequently to judge the status in HTTP transmission. The most typical application of cookies is to determine whether a registered user has logged in to the website, and the user may be prompted whether to retain user information when entering the website next time to simplify the login procedure. These are the functions of cookies. Another important application is processing such as "shopping carts". Users may choose different products on different pages of the same website within a period of time, and this information will be written into Cookies so that the information can be extracted at the time of final payment.
[0039] Cookies can keep the login information until the user's next session with the server. In other words, the next time the user visits the same website, the user w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com