Networking protocol analysis-based business analysis monitoring method and system
A business analysis and network protocol technology, applied in the field of business analysis, can solve the problems of no unified monitoring interface, business system performance degradation, and inability to realize information docking, etc., and achieve excellent scalability and excellent reproducible effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
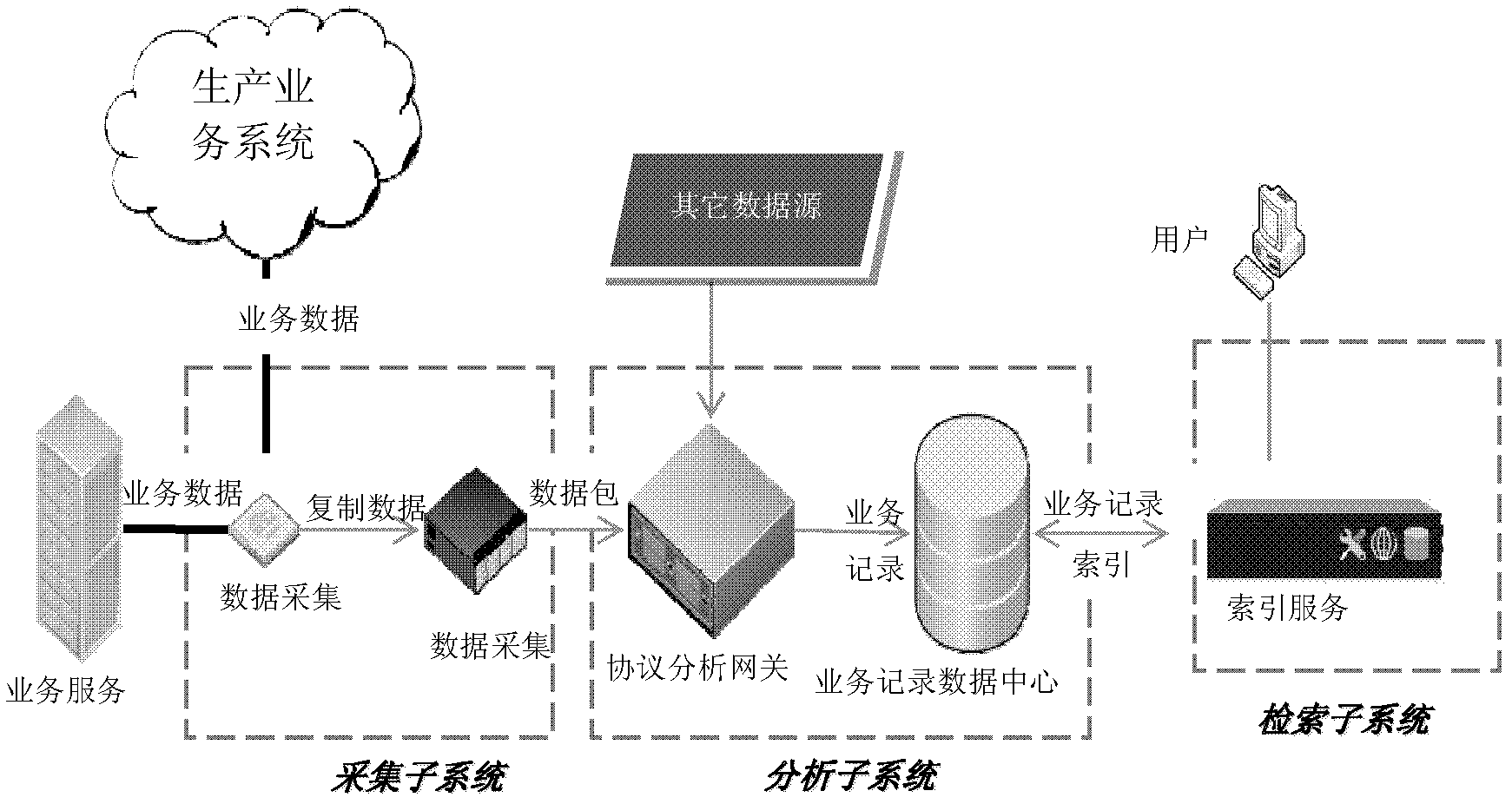
[0032] like figure 1 As shown, in step 401, the read configuration is used to filter and generate business records. Data acquisition module reading, data collector, protocol analysis gateway, etc., all need to read configuration.
[0033] In step 402, monitoring service data is accomplished through network deployment.
[0034] In step 403, judging whether there is a service data packet is also completed by the network device.
[0035] In step 404, it is judged whether to end the system, which can be realized by multiple methods, including semaphore, event, global variable and so on.
[0036]In step 405, the capture of data packets is done by network equipment, which may be a professional capture network card, or a promiscuous mode of a common network card, or others.
[0037] In step 406, whether to copy the data acquisition module is judged according to the configuration file, generally according to the host, port, protocol, etc.
[0038] In step 407, the function of dupl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com