USB (universal serial bus)-key and application method thereof
A terminal and chip technology, applied in user identity/authority verification and key distribution, can solve problems such as hidden security risks and inability to resist illegal user dictionary attacks, and achieve the effect of improving security and preventing dictionary attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The present invention will be further described in detail below through specific embodiments in conjunction with the accompanying drawings.
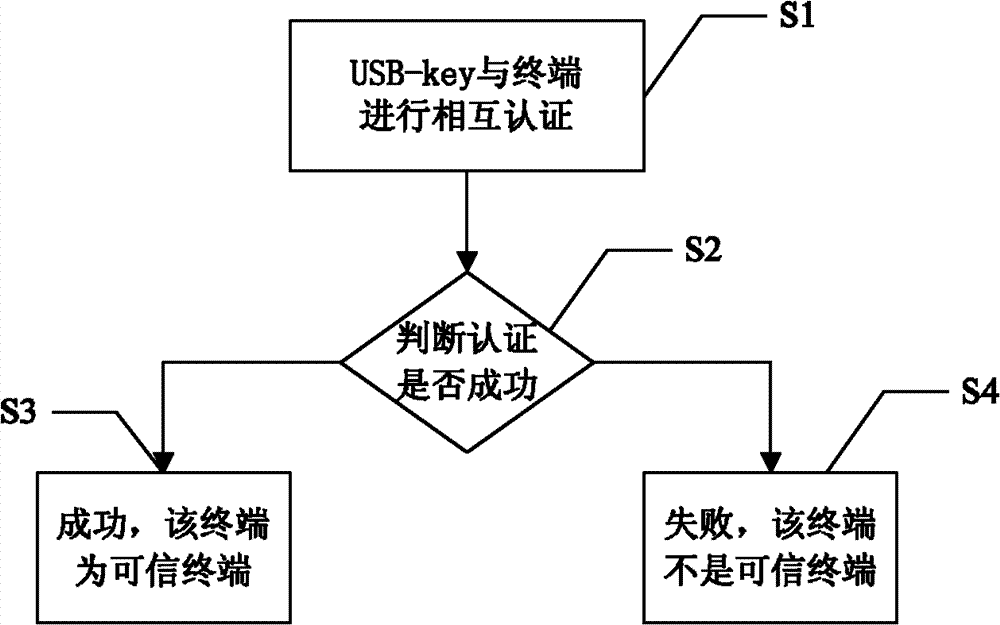
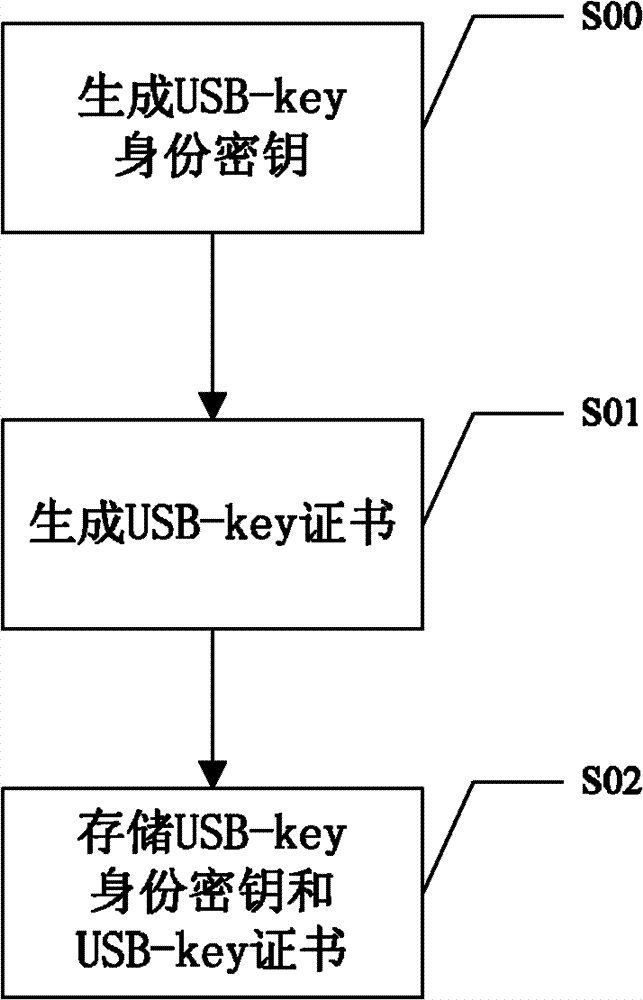
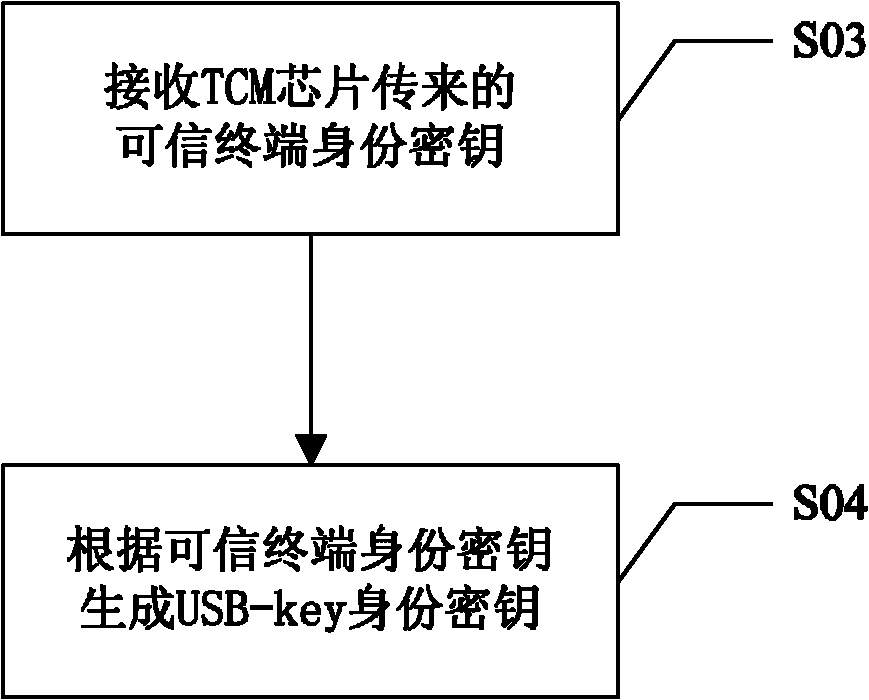
[0045] In the prior art, the main reason for the potential safety hazards in using the USB-key is that the existing USB-key can be used on any computer. Therefore, illegal users can use the USB-key to crack the user's PIN code in an exhaustive manner. In order to solve the potential safety hazards in the use of USB-key in the prior art, when the USB-key is plugged into the terminal for use, the mutual authentication between the USB-key and the terminal is performed first, and if the authentication passes, the USB-key It can be used on the terminal. If the authentication fails, the USB-key cannot be used on the terminal. In this way, the illegal user has no chance to crack the user's PIN code through dictionary attack.
[0046]Furthermore, if the USB-key is bound to a terminal trusted by the user, the bound USB-key can only be use...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com