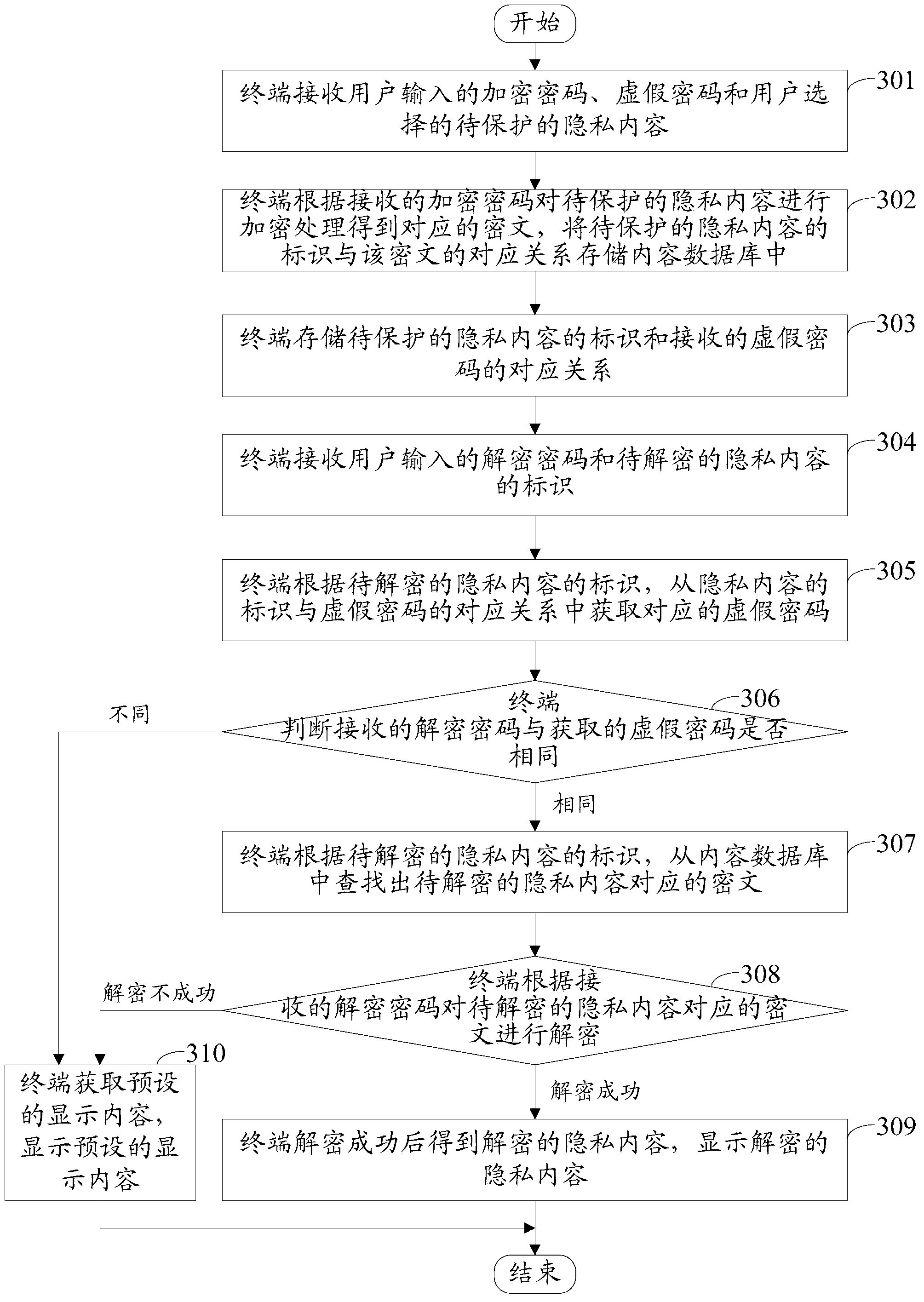Method and device for deciphering private information
A content and privacy technology, which is applied in the field of decrypting private content, can solve the problems of failure to protect private content and low security of private content, and achieve the effect of improving security and protecting security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
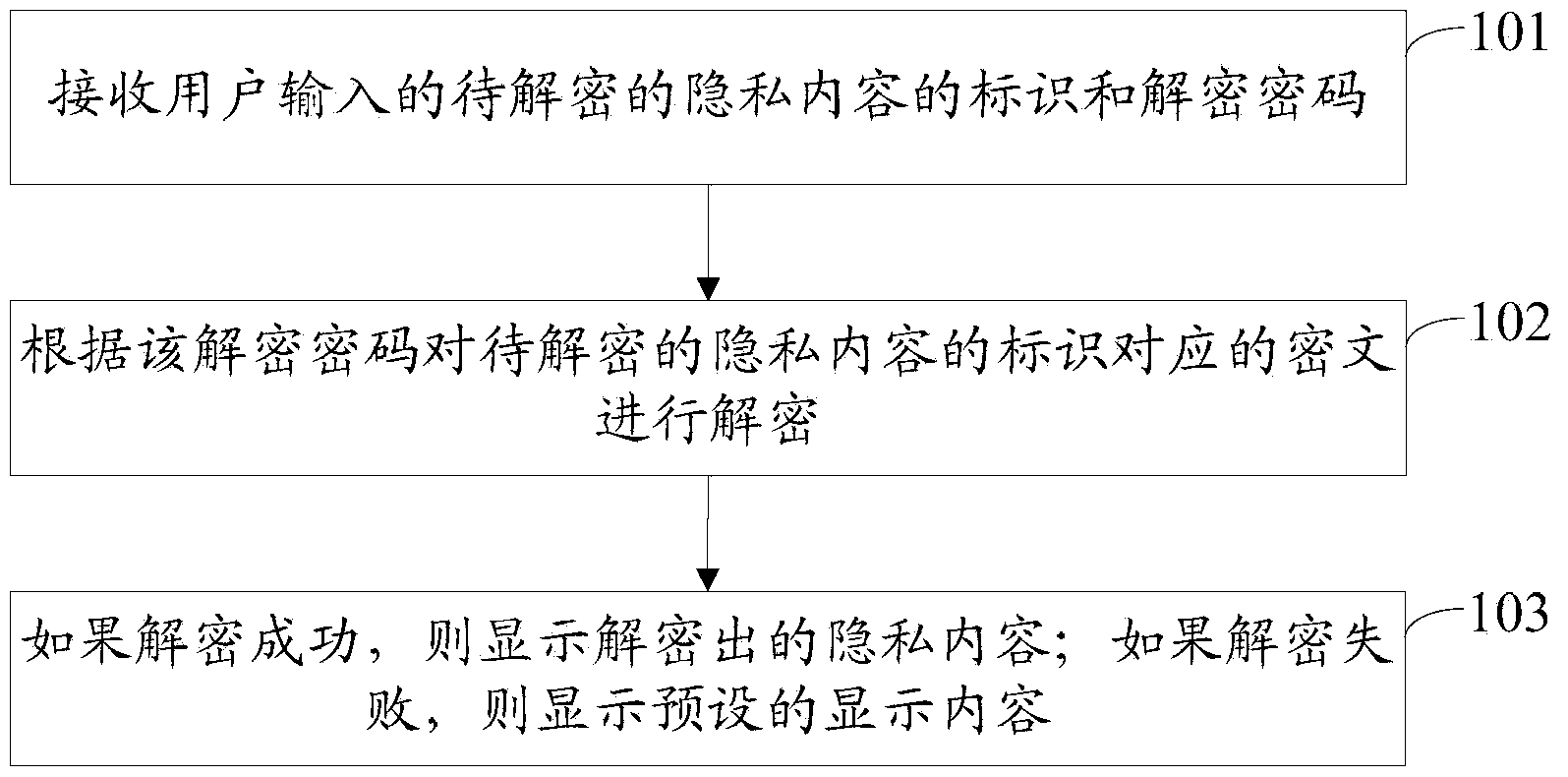
[0035] Such as figure 1 As shown, the embodiment of the present invention provides a method for decrypting private content, including:
[0036] Step 101: Receive the identification and decryption password of the private content to be decrypted input by the user;
[0037] Step 102: Decrypt the ciphertext corresponding to the identifier of the private content to be decrypted according to the decryption password;
[0038] Step 103: If the decryption is successful, display the decrypted private content; if the decryption fails, display the preset display content.
[0039] Wherein, the private content may be the content of the short message or the mobile phone number of the user.
[0040] In the embodiment of the present invention, the identification of the private content to be decrypted and the decryption password input by the user are received, and the ciphertext corresponding to the identification of the private content to be decrypted is decrypted according to the decryption...
Embodiment 2
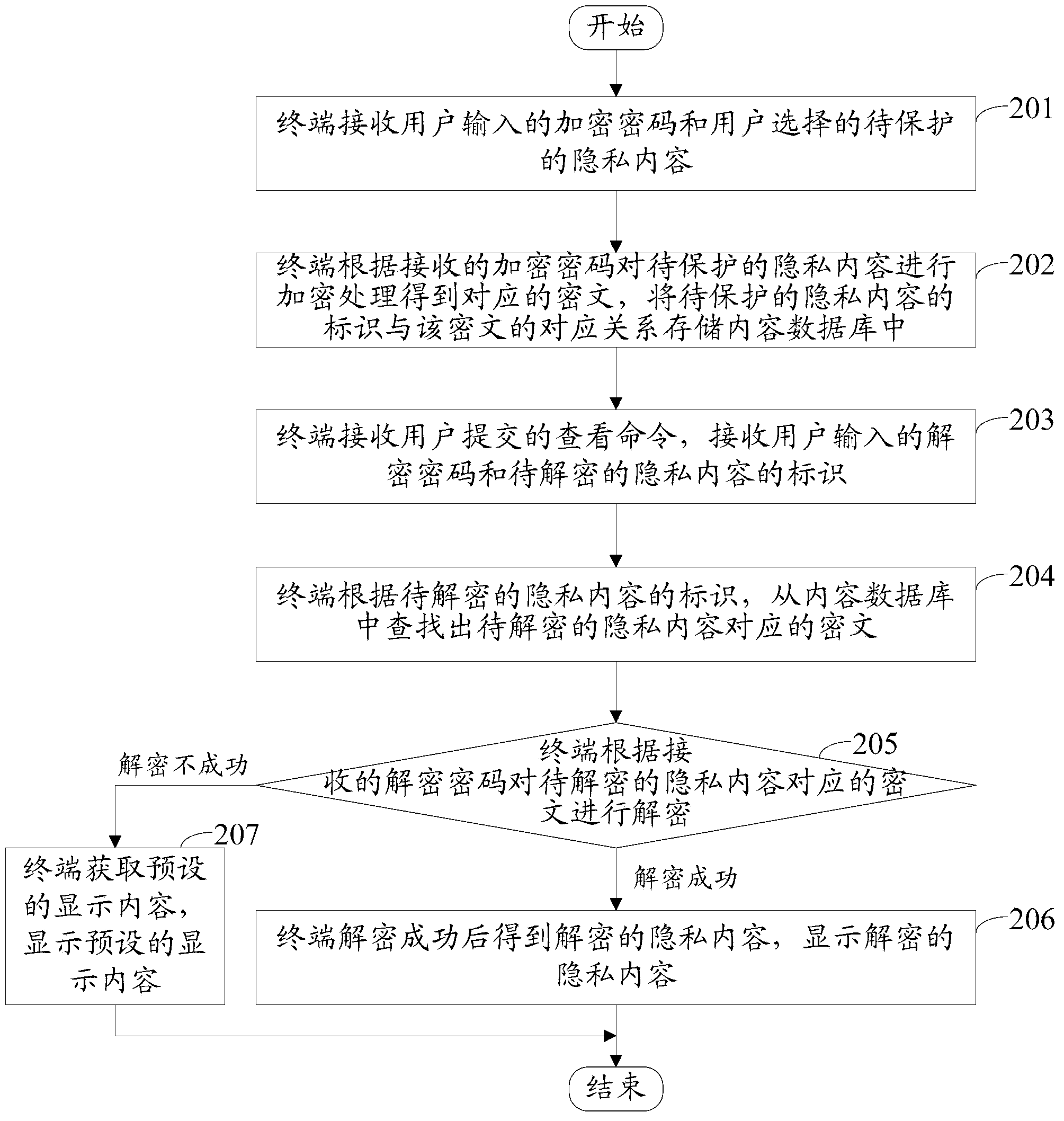
[0042] see figure 2 , the embodiment of the present invention provides a method for decrypting private content, including:
[0043] Step 201: the terminal receives the encrypted password input by the user and the privacy content to be protected selected by the user;
[0044] Specifically, the terminal receives the command submitted by the user for setting the privacy protection content, displays the input interface, and when the user enters the encrypted password in the input interface, receives the confirmation command submitted by the user, and reads the encrypted password input by the user from the input interface; After the user selects and submits the privacy content to be protected in the terminal, the privacy content to be protected selected by the user is received.
[0045] Among them, the terminal will display a button for setting the privacy protection content. When the user needs to protect the privacy content in the terminal, the user can click this button to sub...
Embodiment 3
[0068] see image 3 , the embodiment of the present invention provides a method for decrypting private content, including:
[0069] Step 301: the terminal receives the encrypted password input by the user, the false password and the privacy content to be protected selected by the user;
[0070] Specifically, the terminal receives the command submitted by the user for setting the privacy protection content, and displays the input interface. After the user enters the encrypted password and the false password in the input interface, the terminal receives the confirmation command submitted by the user, and reads the password entered by the user from the input interface. Encrypted password and false password; when the user selects and submits the privacy content to be protected in the terminal, the privacy content to be protected selected by the user is received.
[0071] Among them, the terminal will display a button for setting the privacy protection content. When the user needs...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com