Security key setting method for partitioned wireless sensor network
A wireless sensor and security key technology, applied in the field of wireless sensor network settings, can solve problems such as low computing power, limited energy, and poor balance between security and resource overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] Now in conjunction with accompanying drawing and embodiment the present invention is described in further detail:
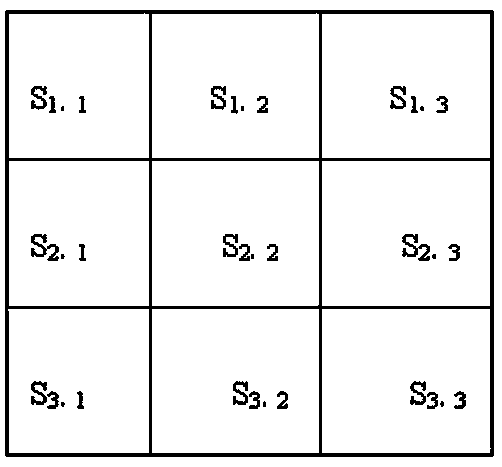
[0029] Step 1: Divide the wireless sensor network deployment area into p×p square grids of the same size, each grid is called the deployment area (i, j), i=1,2,3,...p, j=1, 2,3,...p, p≥2; for example figure 1 The 3×3 square grid shown,
[0030] Step two:
[0031] 1. Generate the key matrix space: by indivual( , ) matrix pair element matrix space ( is a lower triangular matrix, is an upper triangular matrix, , The product of is a symmetric matrix, which is called the key matrix space. Each matrix pair element corresponds to a unique ID value. The generation process is as follows:
[0032] ① First generate a large key pool,
[0033] ②Randomly select m(m+1) / 2 keys from the key pool to form an m-order symmetric matrix K h ,application Matrix factorization method takes the matrix K h decomposed into an m × m lower triangular matrix L h and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com