Low-complexity electronic circuit protected by customized masking
A circuit and unmasking technology, applied in the field of cryptographic circuits and electronic circuits, can solve the problems of increased circuit complexity and irresistibility, and achieve the effect of unique protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
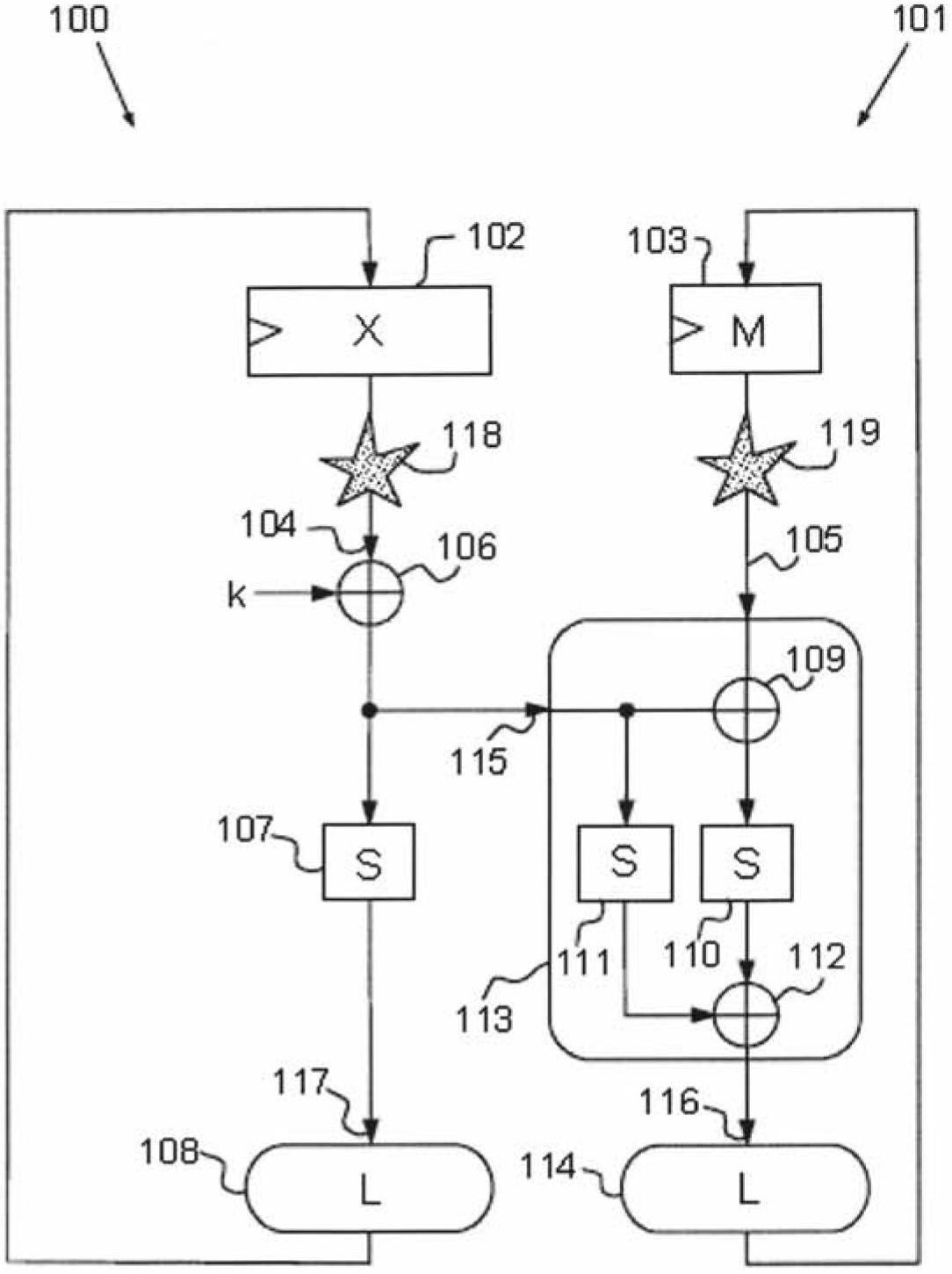
[0049] figure 1 An example of a Feistel function protected by masking is shown.
[0050] Masking principles known to those skilled in the art consist in modifying the representation of the sensitive variable x into a redundant representation. This representation consists of at least two parts, one corresponding to the masked sensitive data denoted by x⊕m and the other corresponding to the mask m. The sum of these two parts in the binary Galois field defining them makes it possible to obtain the variable x by using the following properties:
[0051] x=(x⊕m)⊕m (1)
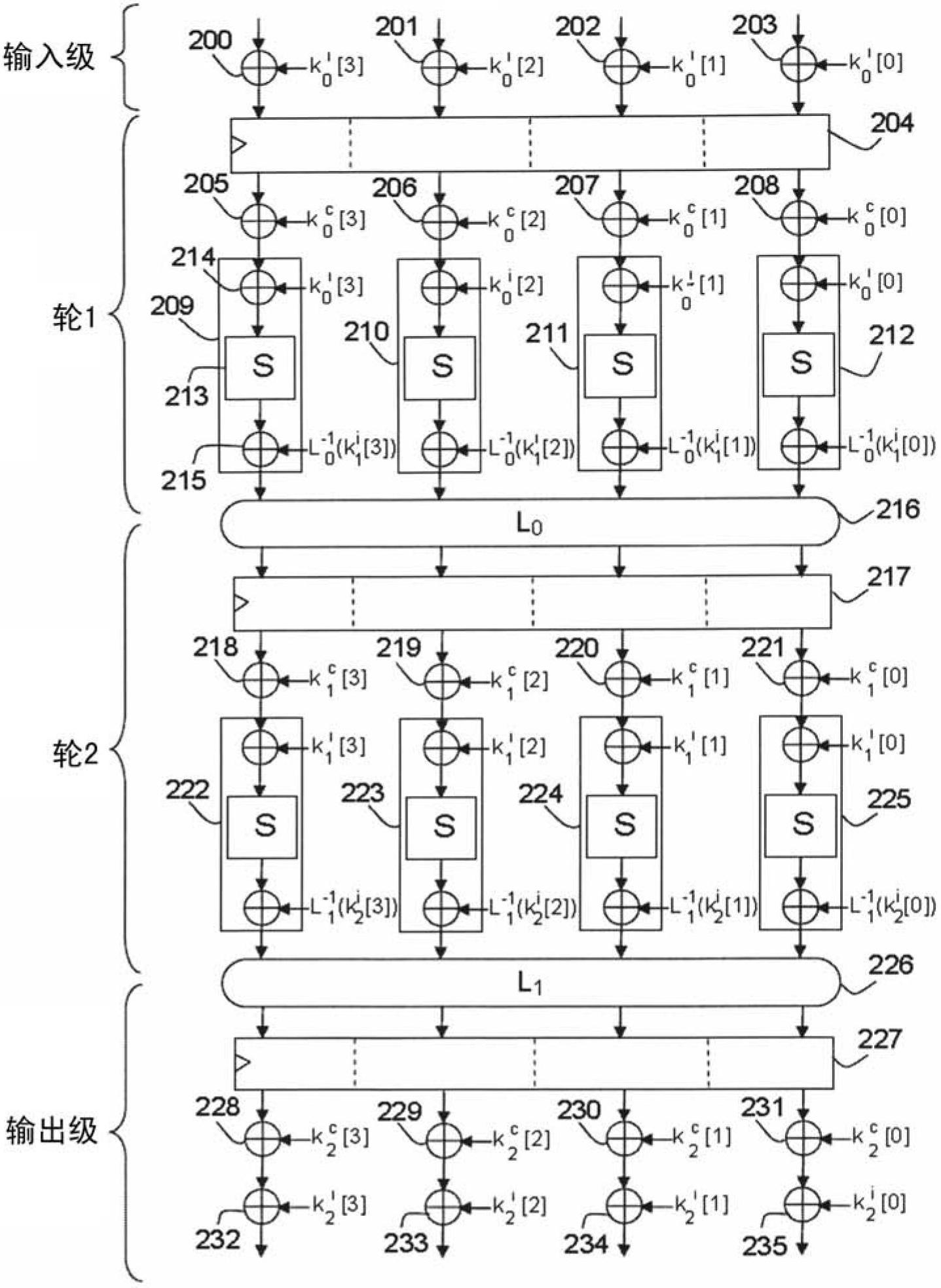
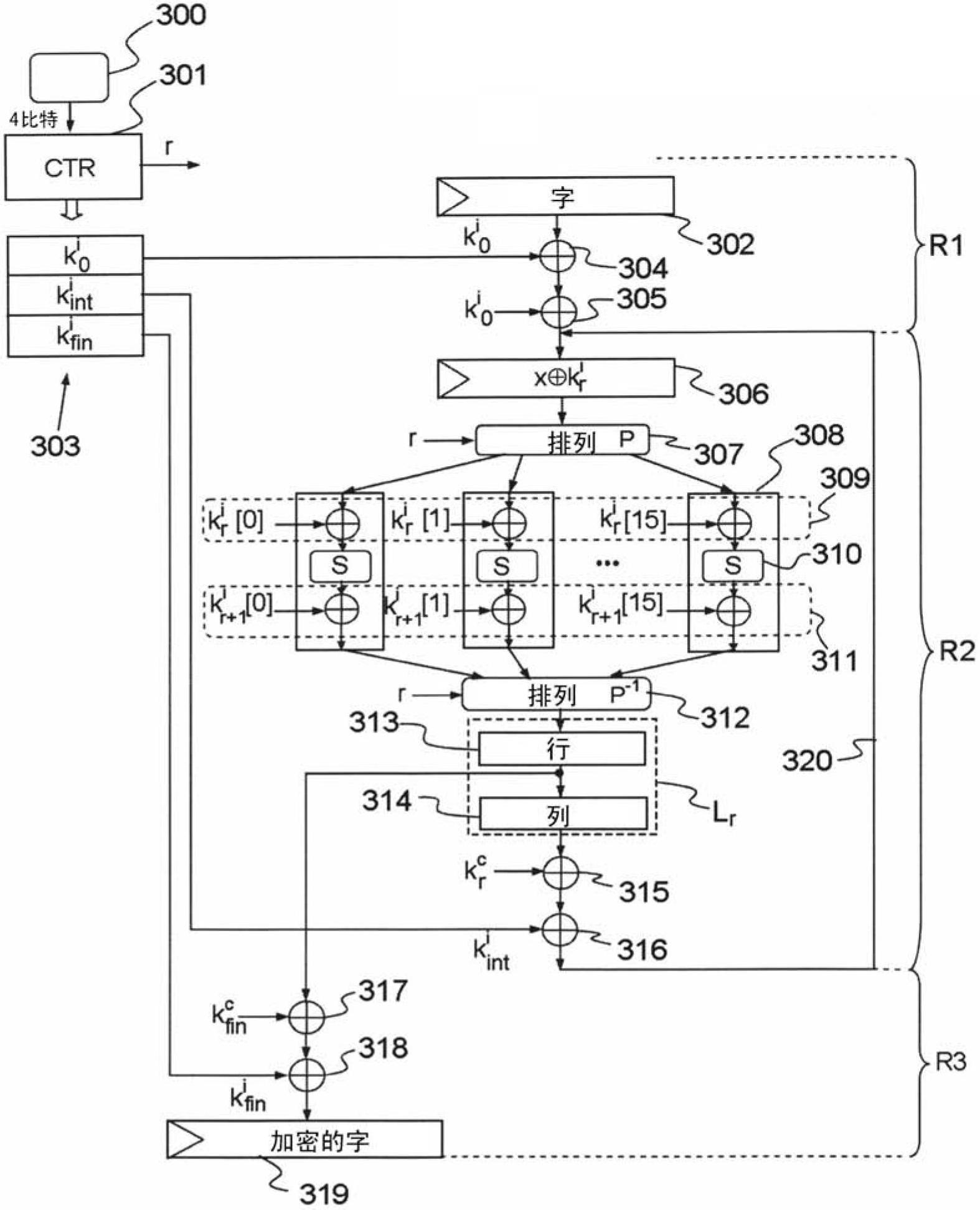
[0052] As an example, in a block encryption algorithm such as DES or AES, the operation result for encrypting a data block is obtained through many rounds of repetition. A "round" is a computational cycle in which at least two types of transformations are performed, one linear and the other non-linear, also called substitution transformations.
[0053] A linear transformation aims to generate dif...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com