Comprehensive security monitoring method and comprehensive security monitoring system based on sentry
A security monitoring and sentinel technology, applied in the field of comprehensive security monitoring methods and systems based on sentry, can solve the problems of worrying security situation, comatose security personnel, and inability to report sentinel information in time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
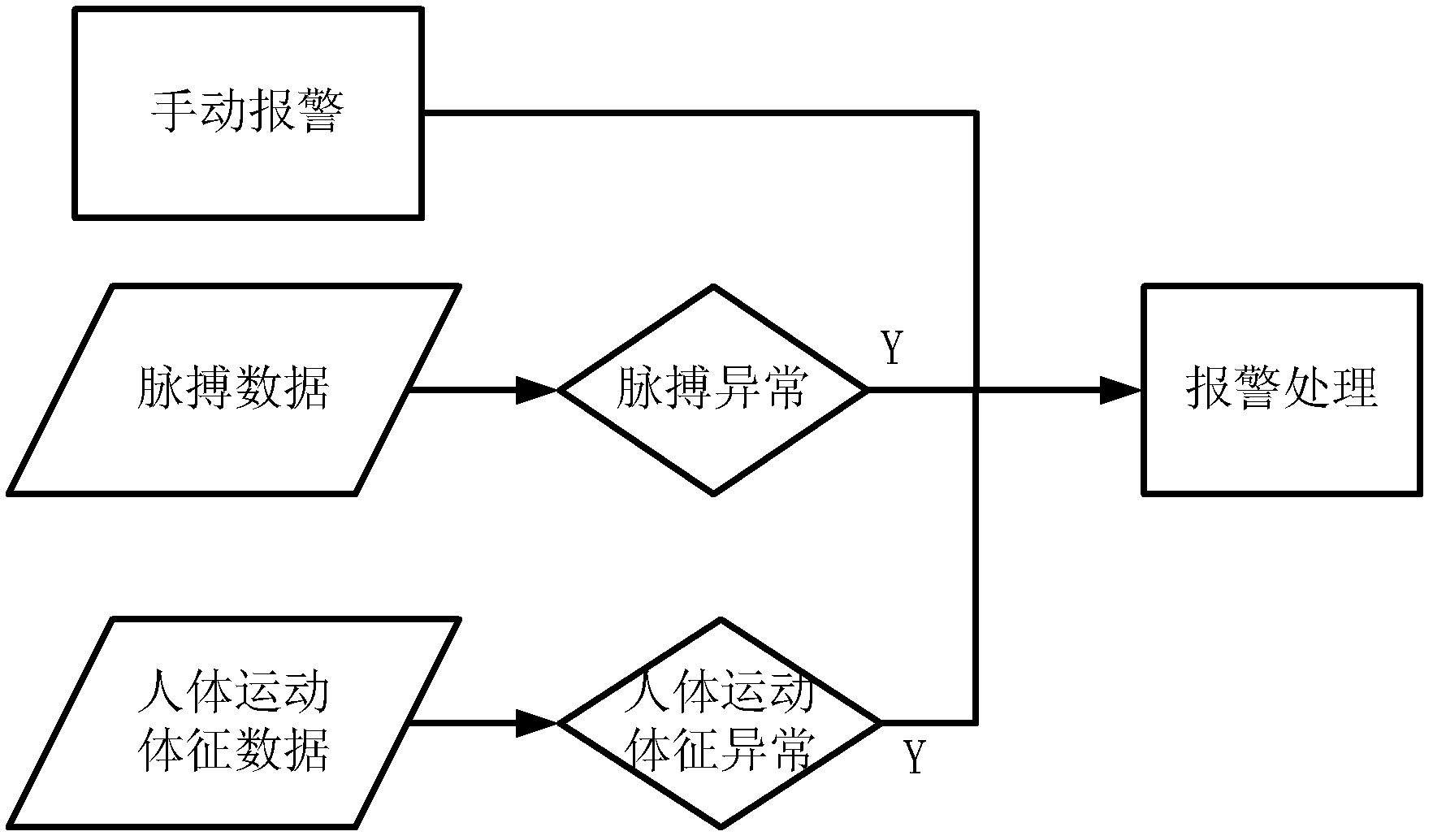
[0058] like figure 1 As shown, the implementation steps of the sentinel-based comprehensive security monitoring method in this embodiment are as follows:
[0059] 1) Set the critical value of the sleep pulse, the weak pulse of life and the threshold of human motion signs;
[0060] 2) Real-time collection of the pulse and human movement signs of the security personnel at the sentry position. When it is detected that the pulse of the security personnel is lower than the sleep pulse threshold, the on-site video of the sentry position will be collected through the camera, and the drowsiness warning will be output to the security personnel and sent to the monitoring center. Collected by the camera On-site video; when it is detected that the pulse of the security personnel is lower than the critical value of the weak pulse of life or the physical signs of the security personnel are lower than the critical value of human physical signs, the on-site video of the sentinel will be colle...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com