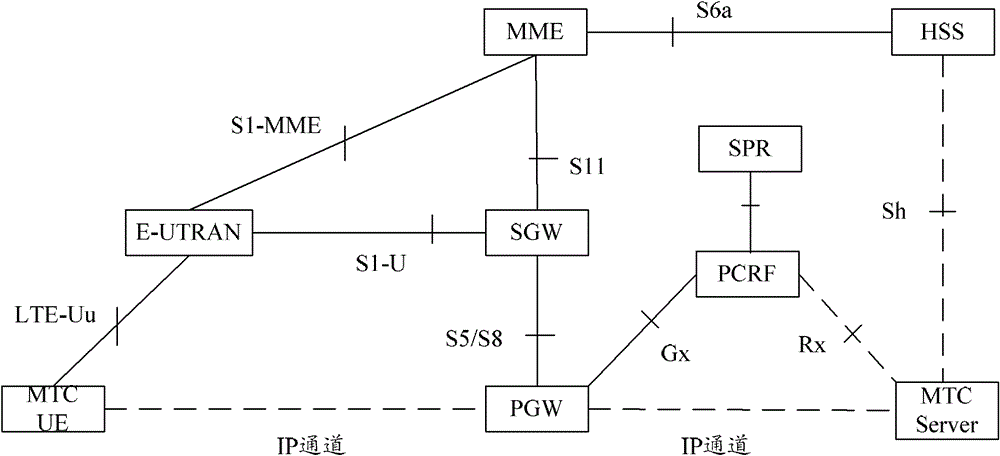
Access control method and system for a shared network
一种接入控制、共享网络的技术,应用在通信领域,能够解决没有区分PLMN接入控制、不能保证终端接入控制公平性等问题,达到保证公平性的效果
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
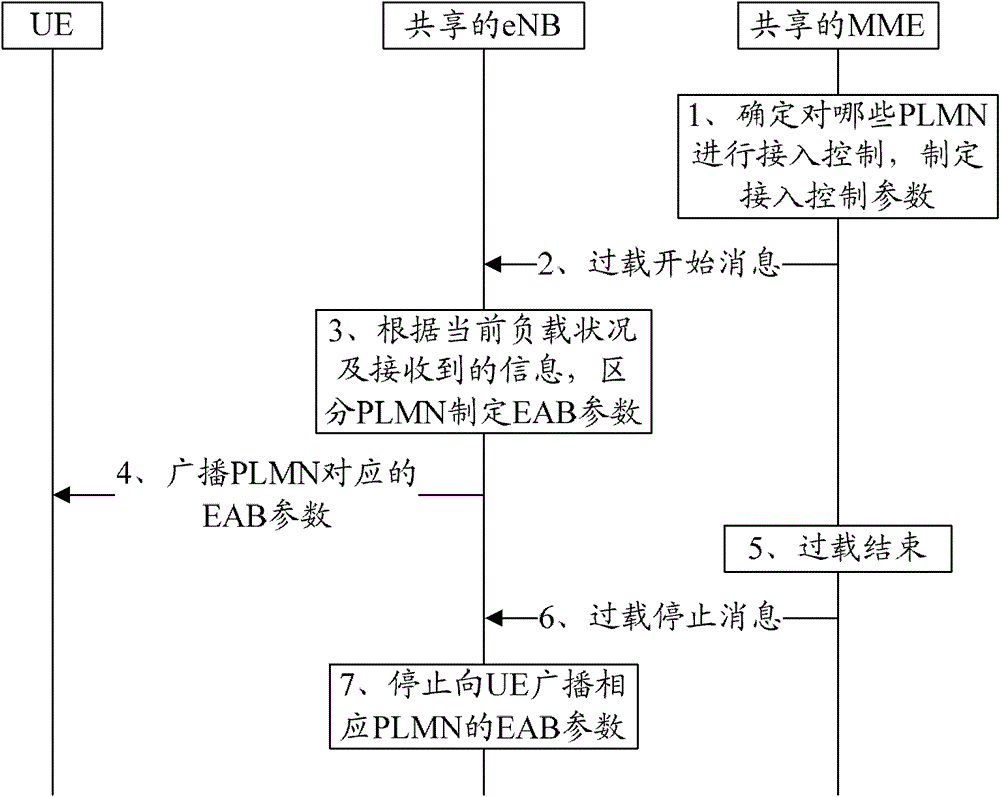
[0061] like figure 2 As shown, in the EPS shared network, the specific implementation process of the shared eNB using the EAB mechanism to perform access control is as follows:
[0062] 1. When the shared MME is overloaded, determine which PLMNs need to perform access control, and optionally formulate corresponding access control parameters.
[0063] 2. The shared MME sends an overload start message to the shared eNB, where the message carries the identity of the PLMN requiring access control and the corresponding access control parameters (optional).
[0064] 3. The shared eNB formulates corresponding EAB parameters for each PLMN requiring access control according to the current load condition and the received information.
[0065] 4. The shared eNB broadcasts to the UE the EAB parameters corresponding to the PLMN that needs to perform access control.
[0066] 5. The shared MME overload condition has ended, and the load returns to normal.
[0067] 6. The shared MME sends ...
Embodiment 2
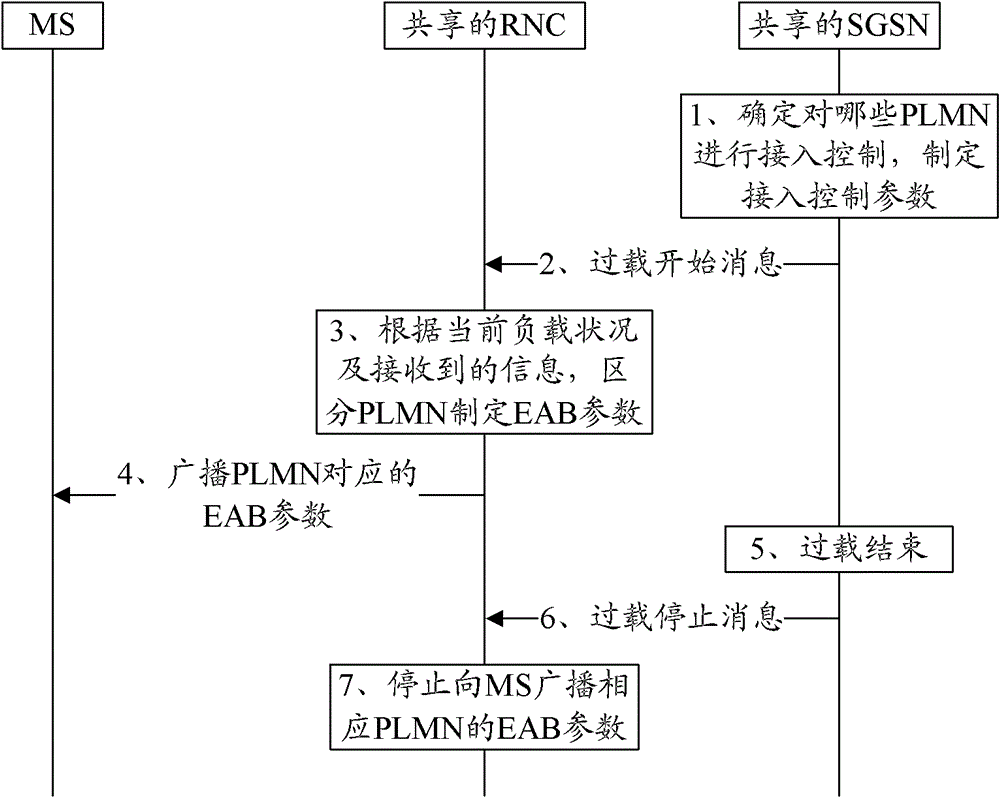
[0070] like image 3 As shown, in the UMTS shared network, the specific implementation process of the shared RNC using the EAB mechanism to perform access control is as follows:
[0071] 1. When the shared SGSN is overloaded, determine which PLMNs need to perform access control, and optionally formulate corresponding access control parameters.
[0072] 2. The shared SGSN sends an overload message to the shared RNC, where the message carries the PLMN identity that needs access control and the corresponding access control parameters (optional).
[0073] 3. The shared RNC formulates corresponding EAB parameters for each PLMN requiring access control according to the current load condition and the received information.
[0074] 4. The shared RNC broadcasts to the MS the EAB parameters corresponding to the PLMN that needs to perform access control.
[0075] 5. The shared SGSN overload condition has ended, and the load returns to normal.
[0076] 6. The shared SGSN sends an overl...
Embodiment 3
[0079] like Figure 4 As shown, in the EPS shared network, the specific implementation process for the shared eNB to perform access control by releasing the wireless connection of the UE is as follows:
[0080] 1. When the shared MME is overloaded, determine which PLMNs need to perform access control, and optionally formulate corresponding access control parameters.
[0081] 2. The shared MME sends an overload start message to the shared eNB, where the message carries the identity of the PLMN requiring access control and the corresponding access control parameters (optional).
[0082] 3. The shared eNB stores the identity of the PLMN that needs to perform access control.
[0083] 4. The shared eNB obtains the PLMN identity selected by the UE.
[0084] 5. If the acquired PLMN identifier selected by the UE is one or one of the PLMN identifiers that are stored by the shared eNB and require access control, the eNB determines to release the RRC connection of the UE.
[0085] 6. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com