Method and device for system login based on autonomously generated password of user
A technology of dynamic password and login method, applied in transmission systems, user identity/authority verification, digital data authentication, etc., can solve the problems of being different, being peeped, imitating legitimate users, etc., achieving the effect of no hardware cost and security protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
[0119] Embodiment 2, the login device application of network chat tool
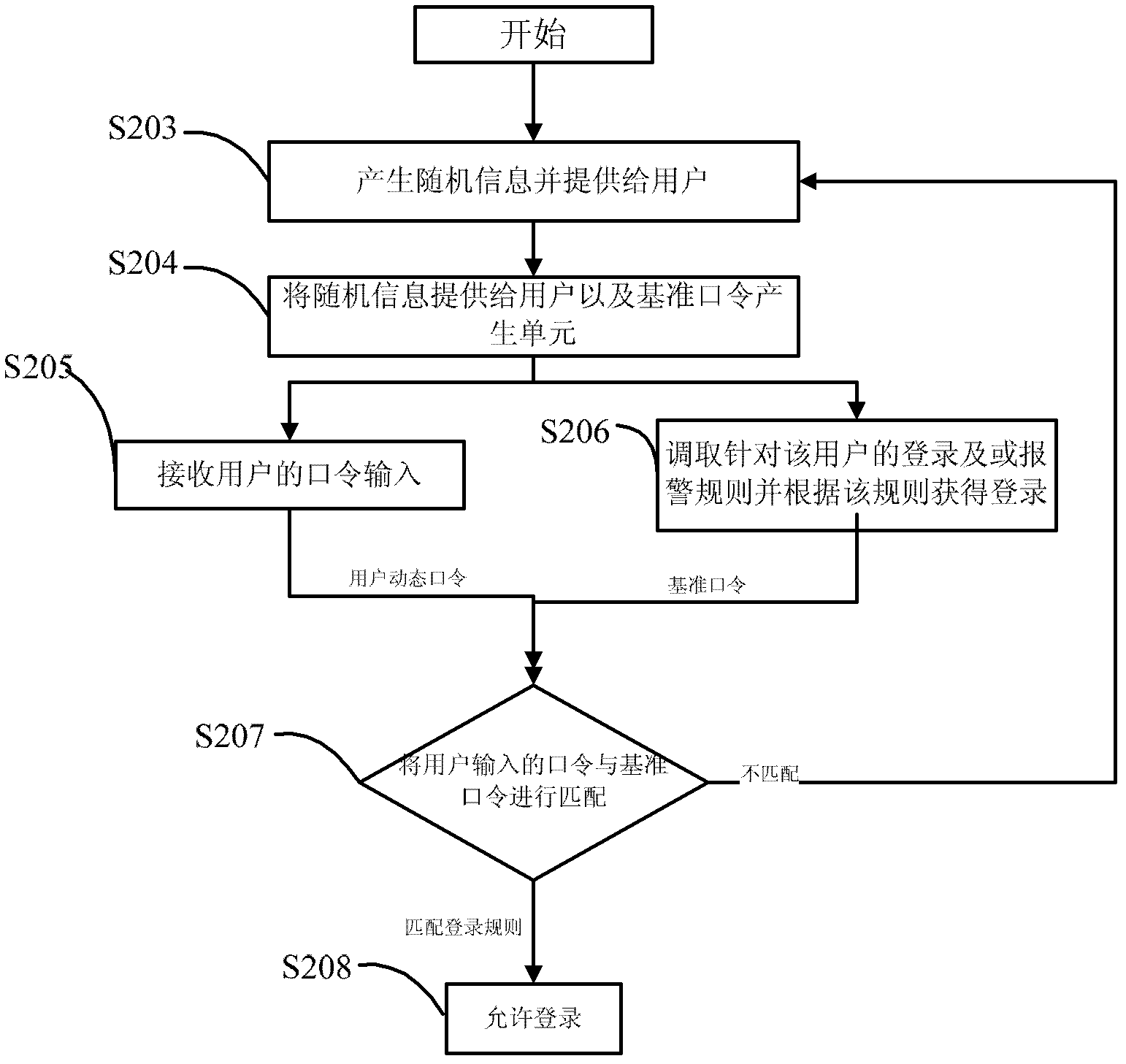
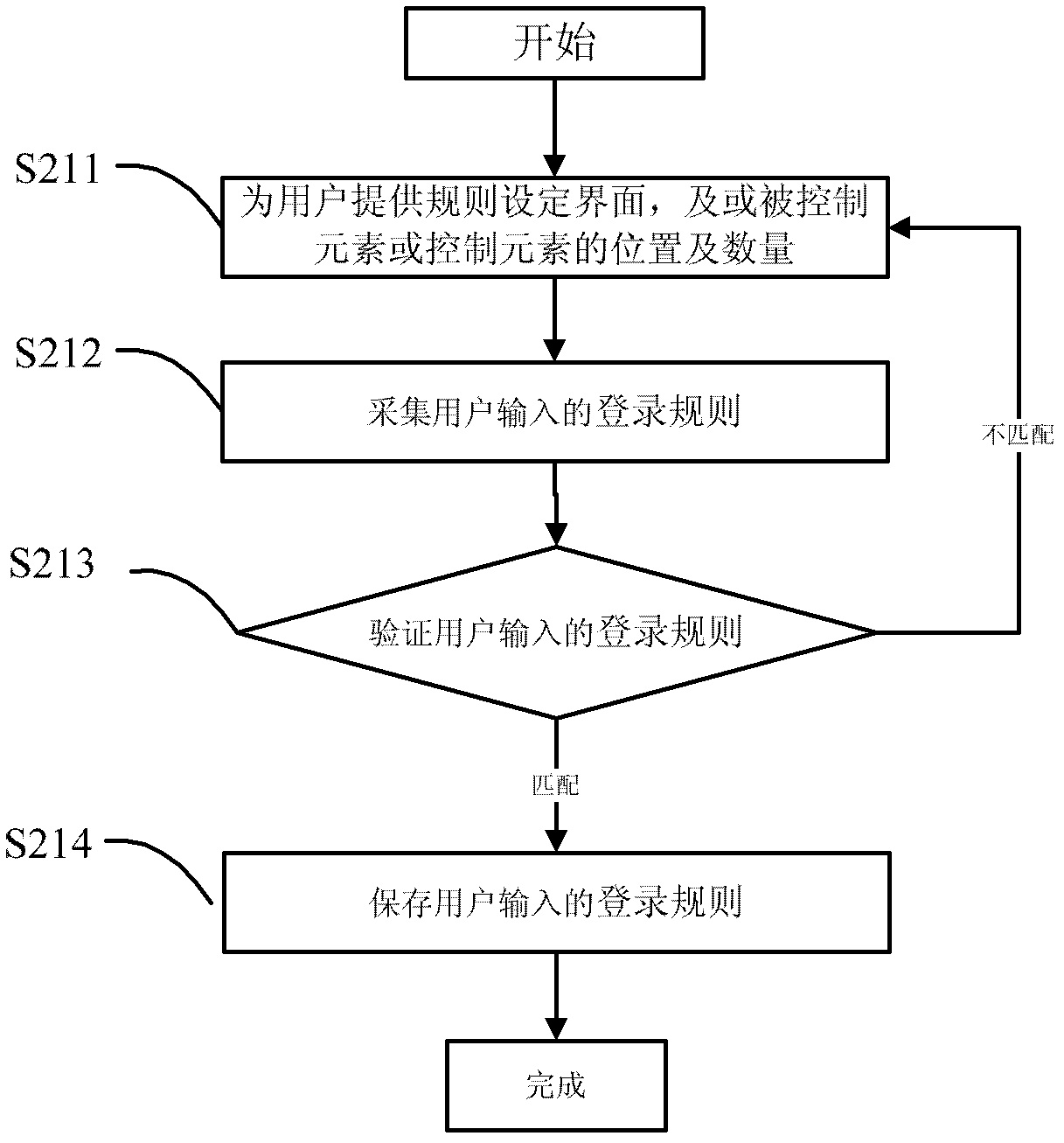
[0120] refer to Figures 3a to 3c , in the method according to another embodiment of the present invention, similar to the previous embodiment, the user can set a login rule for future use when applying the system for the first time, which can be completed by a rule setting unit 101 of the login device ;Such as Figure 3b As shown, the operation process of the rule setting unit 101 includes providing a display area for the user on the user's terminal, and distinguishing the controlled element setting area and the static control element setting area S311 on the display area; Or select and other methods to complete the setting of the controlled element and the setting of the static control element S312 and confirm S313, then the unit considers that the login rule setting is complete, and then the unit will set the completed login rule together with the user's ID in a storage It is stored in the unit for...
Embodiment 3
[0139] Embodiment 3, the application of online banking, online payment, online securities
[0140] refer to Figures 4a to 4c , in the method according to another embodiment of the present invention, similar to the previous embodiment, the user can set a login rule for future use when logging in for the first time, which can be completed by a rule setting 101 unit of the login device; the The rule setting unit includes providing a display area for the user on the display device of the user's terminal 20, and distinguishing the controlled element setting area and the static control element setting area S411 on the display area; The setting of the controlled element and the setting of the static control element S412 and after verification and confirmation S413, then the unit considers that the login rule setting is completed, and then the unit will store the set login rule together with the user's ID in a storage unit for Invoking S402 in the future, the storage can be encryp...
Embodiment 4
[0168] Embodiment 4, the application to the login of bank ATM, POS machine
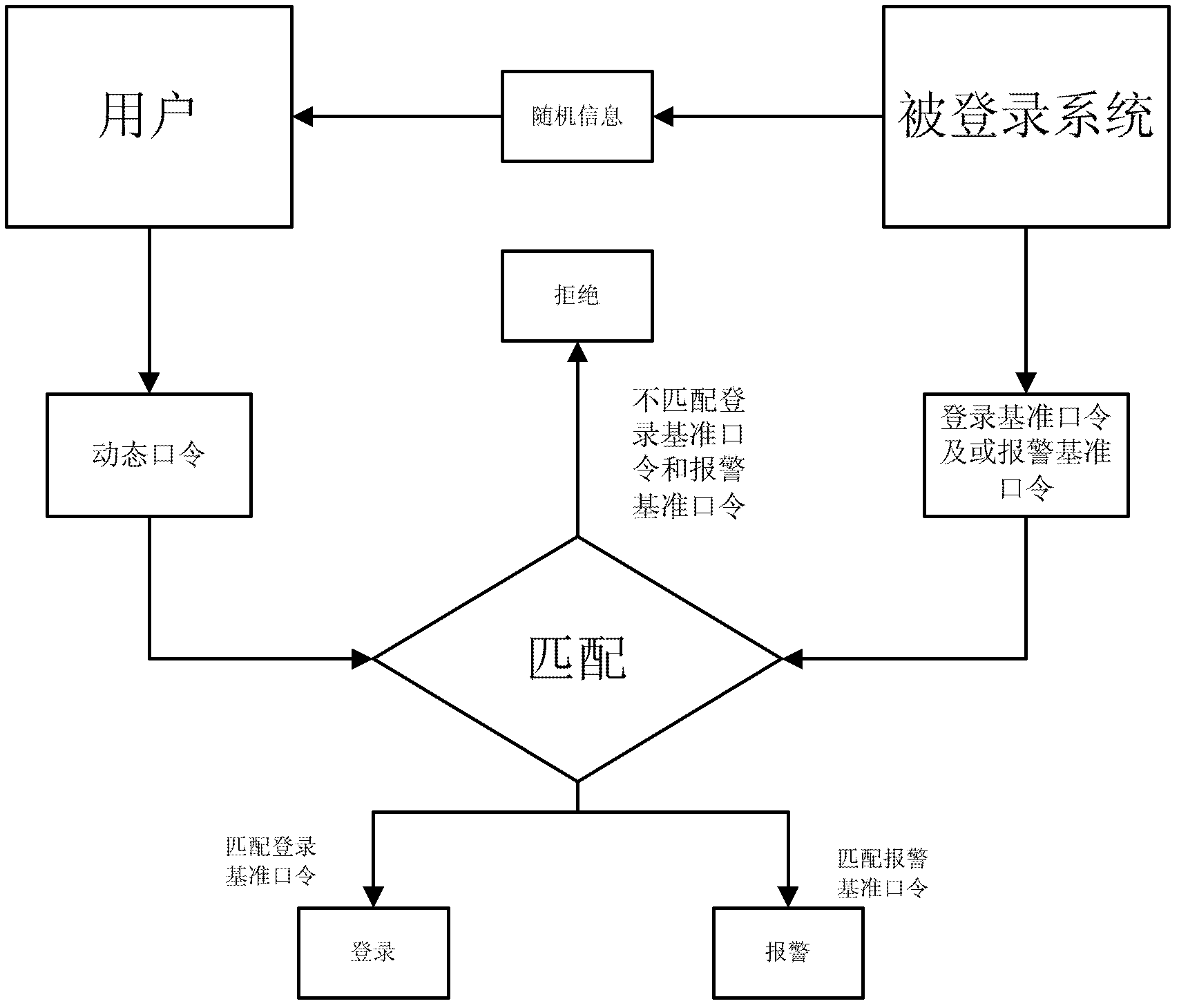
[0169] refer to Figures 5a to 5c , in an example for this application, as Figure 5a As shown, similar to the previous embodiment, it includes login steps 503, 504, 505, 506, 507, etc., and users generally use tools such as bank cards to achieve identity verification. Therefore, the login device and method of the present invention do not need to provide user The interface for inputting the user ID, and the user ID acquisition unit 105 directly determines the user's ID by reading tools such as bank cards, and subsequent steps such as the provision of random information and the generation of reference passwords, the acquisition of input dynamic passwords, and password matching The setting of the etc. unit 107 can be such as the way of logging in for network chat tools, or can be like the way of logging in for online banking, which depends on the arrangement of ATMs or POS machines.
[0170] Login r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com