Usage monitoring method supporting traffic detection function and usage monitoring system
A flow detection function and usage monitoring technology, applied in the transmission system, digital transmission system, telephone communication, etc., can solve the problem that the IP-CAN level usage monitoring function cannot be accurately performed, TDF cannot detect the flow information application or data flow, and monitor Control and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
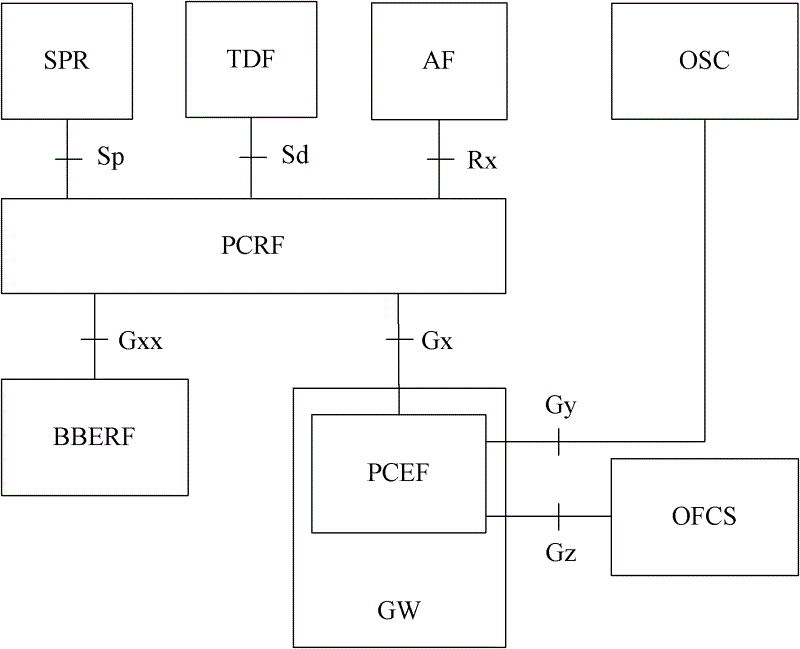
Image
Examples
Embodiment 1
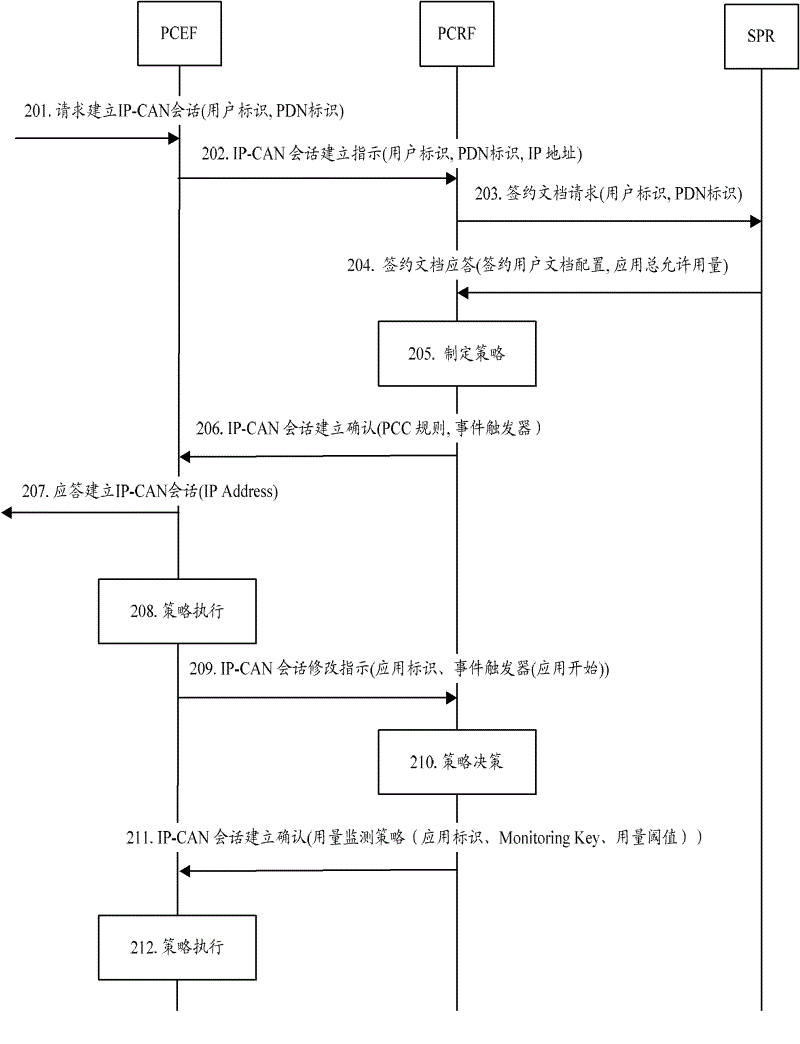
[0081] Embodiment 1: The PCEF integrates the TDF function, and the TDF adopts a report request mode.
[0082] figure 2 It is a flow chart of the usage monitoring method of Embodiment 1 of the present invention, such as figure 2 As shown, the process includes the following steps:
[0083] Step 201, in the process of the UE requesting to establish an IP-CAN session, the gateway where the PCEF is located receives the IP-CAN session establishment request message, and carries the user identifier and the PDN network requested for access in the IP-CAN session establishment request message The PDN identifier.
[0084] In step 202, the PCEF sends an IP-CAN session establishment instruction message to the PCRF, and the IP-CAN session establishment instruction message carries the user identifier, the PDN identifier and the IP address (IPAddress) allocated to the UE.
[0085] In step 203, the PCRF judges that there is no subscription information of the user according to the user iden...
Embodiment 2
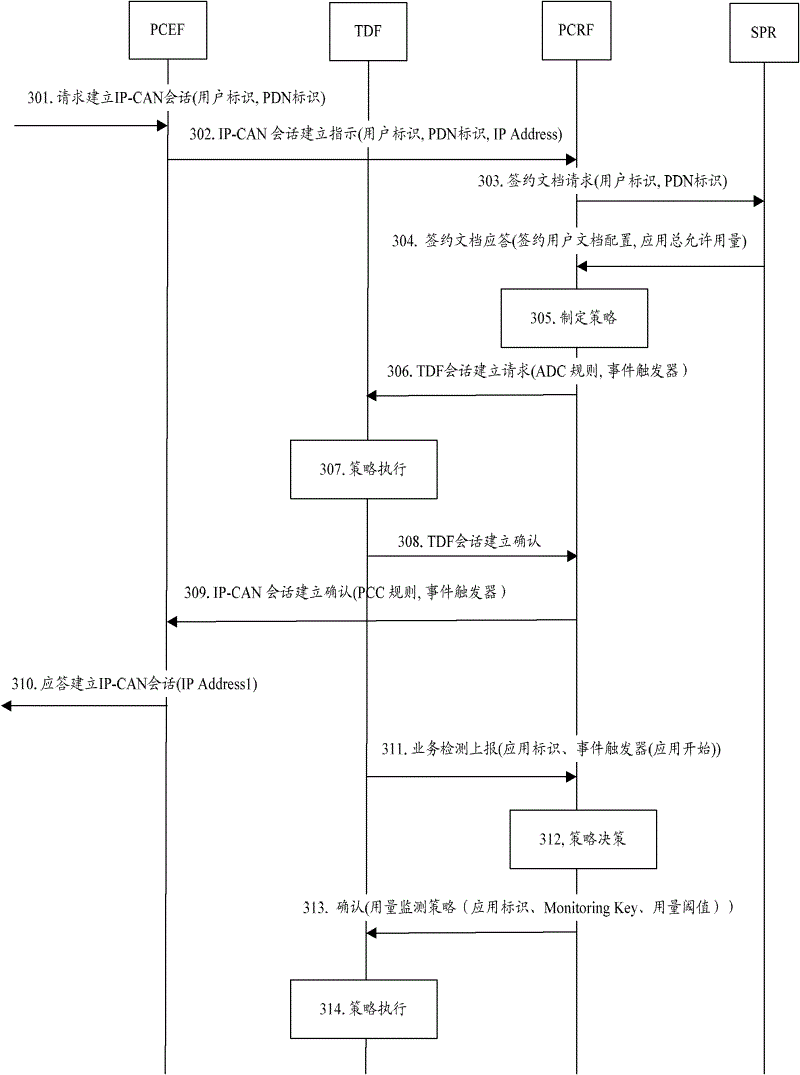
[0098] Embodiment 2: The TDF is independently deployed, and the TDF adopts a report request mode.
[0099] image 3 It is a flow chart of the dosage monitoring method of Embodiment 2 of the present invention, such as image 3 As shown, the process includes the following steps:
[0100] Step 301, in the process of the UE requesting to establish an IP-CAN session, the gateway where the PCEF is located receives the IP-CAN session establishment request message, and carries the user identification and the PDN network requested for access in the IP-CAN session establishment request message The PDN identifier.
[0101] In step 302, the PCEF sends an IP-CAN session establishment indication message to the PCRF, and the IP-CAN session establishment indication message carries a user identifier, a PDN identifier, and an IP address (IPAddress) allocated to the UE.
[0102] Step 303 , the PCRF judges that there is no subscription information of the user according to the user identifier, ...
Embodiment 3
[0116] Embodiment 3: The PCEF integrates the TDF function, and the TDF adopts an unsolicited reporting mode.
[0117] Figure 4 It is a flow chart of the usage monitoring method of the embodiment of the present invention, such as Figure 4 As shown, the process includes the following steps:
[0118] Step 401, in the process of the UE requesting to establish an IP-CAN session, the gateway where the PCEF is located receives the IP-CAN session establishment request message, and carries the user identifier and the PDN network requested for access in the IP-CAN session establishment request message The PDN identifier.
[0119] In step 402, the PCEF sends an IP-CAN session establishment instruction message to the PCRF, and the IP-CAN session establishment instruction message carries the user identifier, the PDN identifier and the IP address (IPAddress) assigned to the UE.
[0120] Step 403 , the PCRF judges that there is no subscription information of the user according to the us...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com