Access control method and device
An access control and access request technology, applied in the field of communication, can solve the problems of inability to send, unable to meet user needs, not distinguishing UEs, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
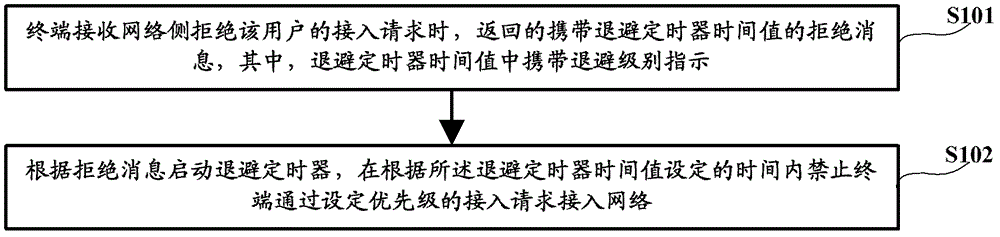
[0036] The time value of the backoff timer is the time value of the specific priority backoff timer used to instruct the terminal to start the specific priority backoff timer for the specific priority access request, and the time value of the specific priority backoff timer The MM Back-off Timer IEI (Back-off Timer Information Element Identifier) of the MM is modified to indicate to the terminal that the time value of the back-off timer is a specific priority back-off timer time value.
[0037] The terminal starts a specific priority backoff timer according to the time value of the specific priority backoff timer;
[0038] The specific priority backoff timer prohibits the terminal from accessing the network through an access request whose priority level is lower than or equal to the specific priority within a set time.
[0039] For example, for a low access priority access request, in the returned rejection message, the time value of the backoff timer is the time value of th...
Embodiment 2
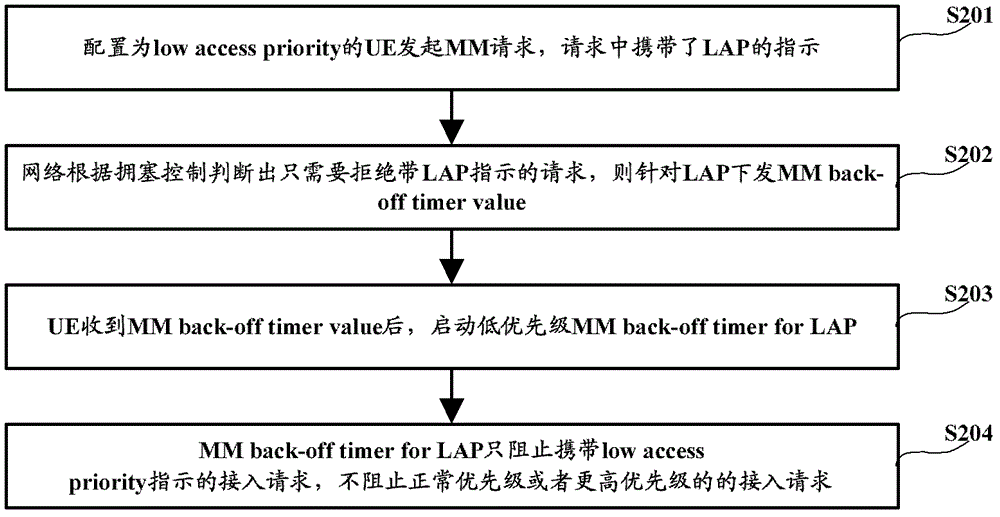
[0048] In the rejection message issued for the access request, there is a backoff timer time value carrying a priority level indication. The priority level indicated by the priority level indication can be the priority level of the access request, or can be set to Priority higher than access requests. After the terminal receives the rejection message, it starts the specified level backoff timer, and the level set in the specified level backoff timer is the priority indicated by the priority level indication; the specified level backoff timer only prohibits the terminal from passing through within the set time. Access requests with a priority lower than or equal to the set level are connected to the network. Specifically, such as image 3 shown, including:
[0049] Step S301, UE configured as low access priority initiates an access request;
[0050] Step S302, the network judges which level of congestion control mechanism is currently used according to the congestion control...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com