Software protection method based on microchip
A software protection and chip technology, applied in program/content distribution protection, instruments, electrical digital data processing, etc., to achieve the effects of high performance, small amount of computation, and low cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] In order to facilitate the understanding of those skilled in the art, the technical solution of the present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments:
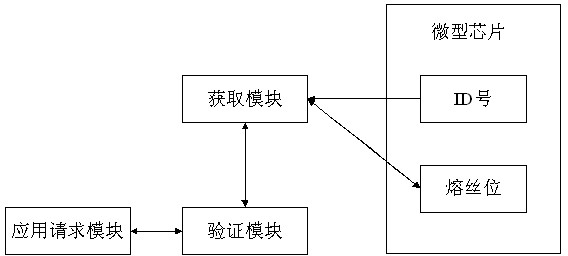
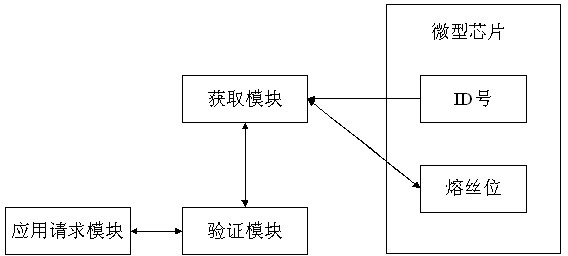
[0022] A method for protecting software based on a microchip, including an application request module, an ID number operation module, a software verification and encryption module, such as figure 1 As shown, its implementation steps are:
[0023] Before use, the step of encrypting the software is to use the acquisition module to read the ID number X of the microchip, and the verification module encrypts the read ID number X to obtain the ciphertext Y, and then write Y to the microchip through the acquisition module in the fuse bit.
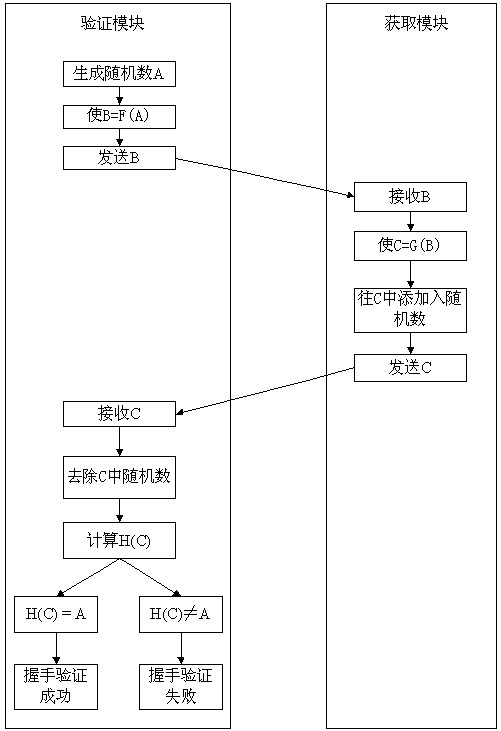
[0024] When in use, the steps of reading and verifying the software encrypted information are:
[0025] (1) When the microchip is applied, the application request module requests access to the software module, the ac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com