Method for implementing end-to-end cross-base-station transmission of encryption voice of analog cluster system
A technology for encrypted voice and trunking systems, applied in the usage of multiple keys/algorithms, security devices, electrical components, etc., can solve problems such as inconvenience of use and affect the quality of communication transmission, and achieve the effect of reducing bit errors
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0012] The specific implementation manners of the present invention will be described in detail below in conjunction with the accompanying drawings.
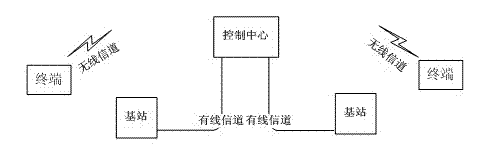
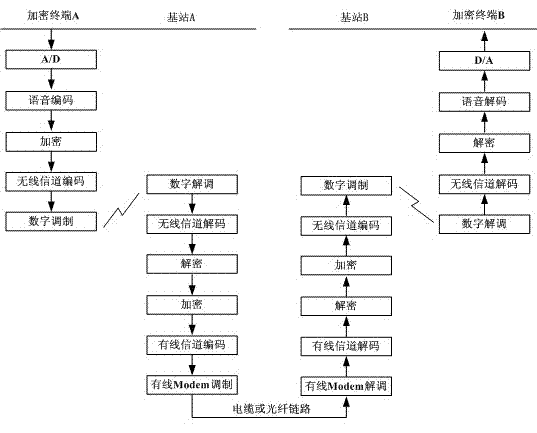
[0013] The invention discloses a method for implementing end-to-end encrypted voice cross-base station transmission in an analog trunking system, which specifically includes the following steps: a sending terminal encrypts A / D sampled and voice coded data and then transmits it to a near-end base station; After digital demodulation, wireless channel decoding and decryption of the received data, the terminal base station takes out effective voice code data; the near-end base station encrypts the voice code data and selects a channel coding method suitable for the characteristics of the wired channel for wired channel coding The above-mentioned channel coded data is modulated by the cable modem and then transmitted to the remote base station through the wired link between the base stations. After receiving the signal, the remote bas...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com