Biological characteristic remote authentication method based on visual codes
A biometric, remote authentication technology, applied in the field of biometric remote authentication based on visual password, can solve the problems of no longer recovering secret biometric images, stealing and improving secret biometric images, etc., to ensure recoverability, The effect of ensuring safety and ensuring stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
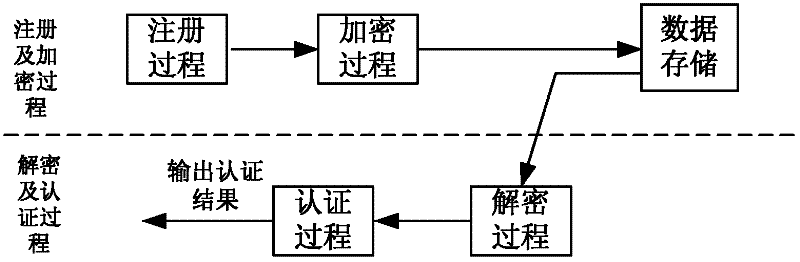
[0029] In the specific implementation manner, with reference to the accompanying drawings, the specific flow of a complete biometric remote authentication method based on visual passwords will be described in detail.
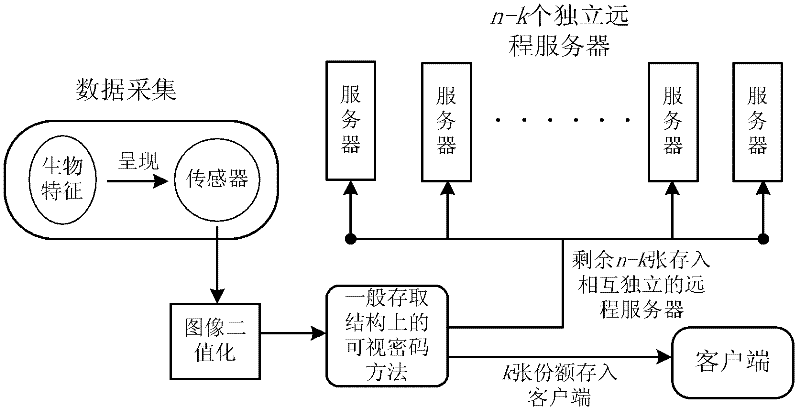
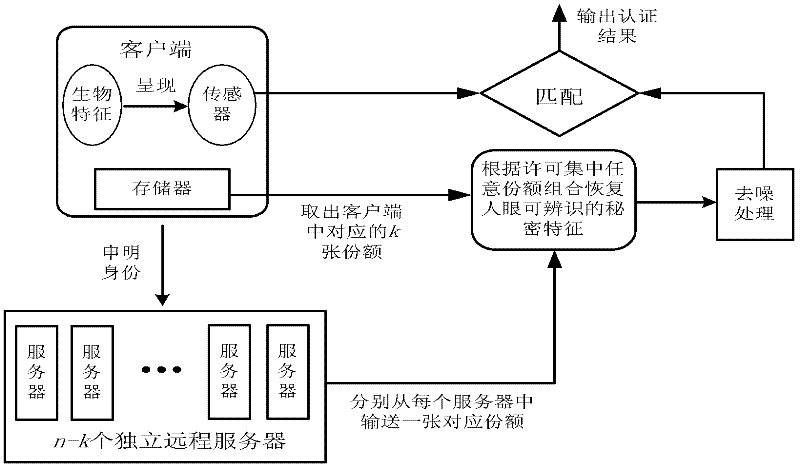
[0030] refer to figure 1 , the biometric remote authentication method based on visual password of the present invention includes several steps of registration, encryption, decryption and authentication, wherein the registration and encryption process is as follows: figure 2 As shown, the decryption and authentication process is as follows image 3 As shown, the specific steps are as follows:
[0031] Step 1: Register the user U in the biometric remote authentication system, and acquire the registered biometric image SI of the user U through the sensor.
[0032] Step 2: Encrypt the obtained registered biometric image SI by using the visual password method on the general access structure:
[0033] 2a) Perform binarization preprocessing on the obtained register...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com