RFID (Radio Frequency Identification Device) mutual authentication method based on secret key and cache mechanism
A two-way authentication and key technology, applied in the field of communication, can solve the problems of inability to effectively prevent denial of service attacks, replay and spoofing attacks, inability to resist eavesdropping, replay, spoofing and tracking attacks, and inability to resist denial of service attacks , to achieve the effect of preventing location tracking problems, reducing the number of searches, and having little impact on authentication speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
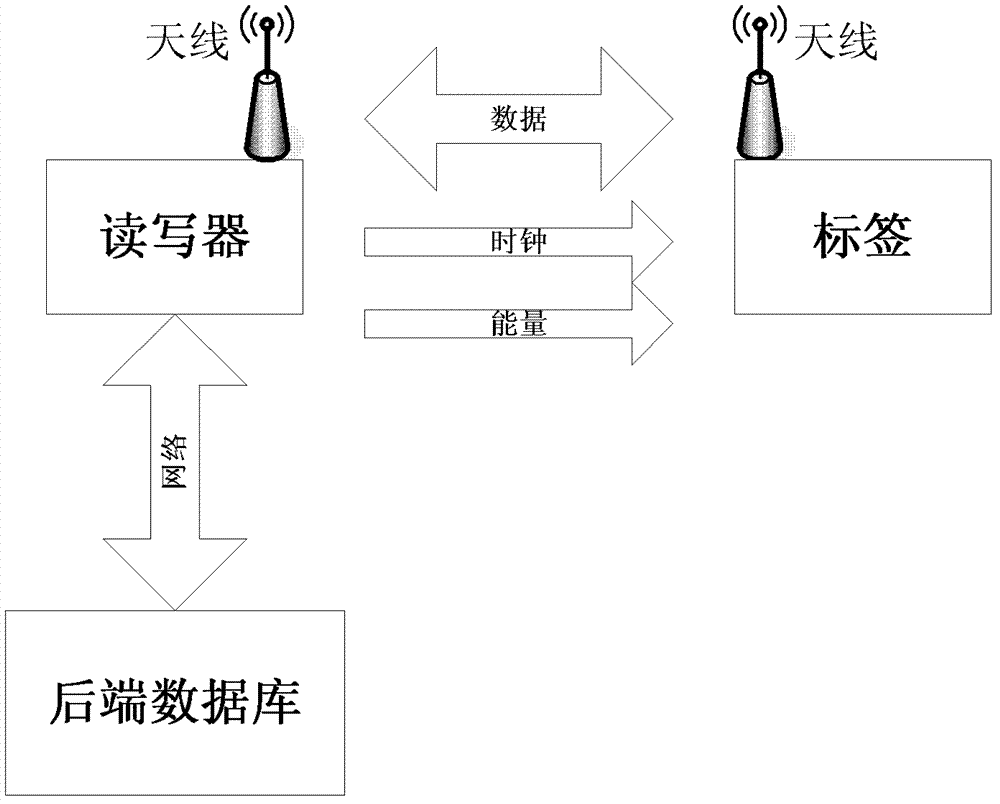
[0027] refer to figure 1 , the most basic radio frequency identification RFID system is mainly composed of tags, readers and background databases. in:
[0028] Tags: Composed of coupling elements and chips, each tag has a unique electronic code, which is attached to the object to identify the target object. Communicate with the reader through radio frequency signals.
[0029] Reader: It is a device that writes and reads tag information, and communicates with the database through the network to complete multiple tasks for the data of the radio frequency electronic tag.
[0030] Back-end database: Read and write control on tags, which stores tag-related information.
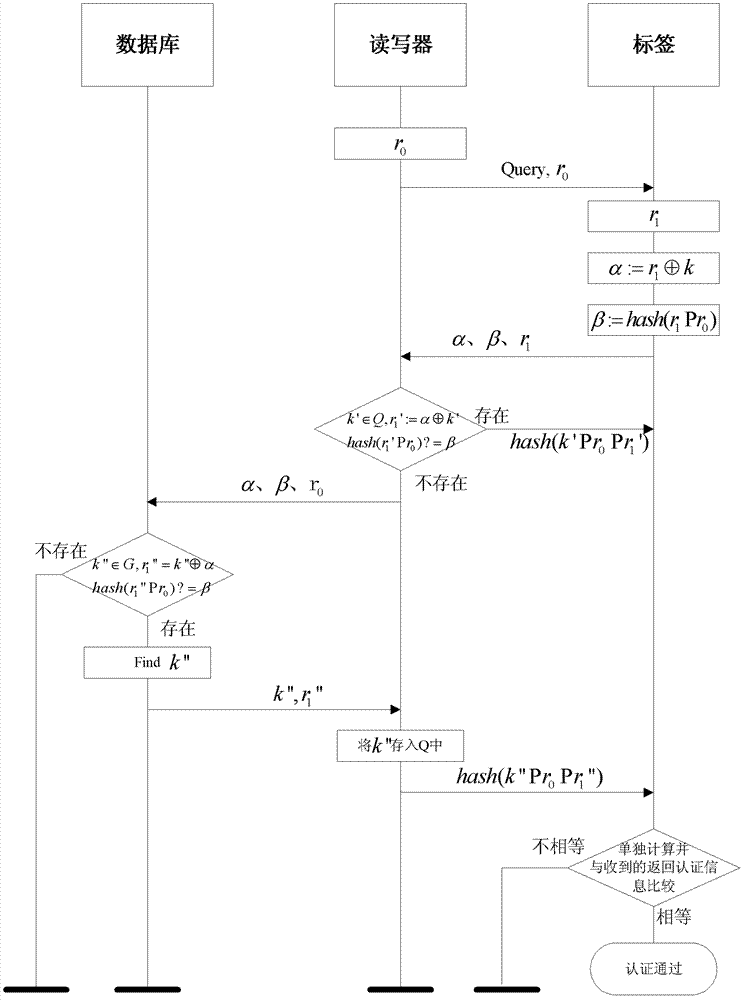
[0031] The invention is an authentication method for a reader-writer and a label, and only when both parties pass the security authentication can relevant data communication be carried out.
[0032] Initial conditions:
[0033] The tag contains a random number generation module and a Hash function, and stores it...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com