A variable-rate safe transmission method of image data based on fountain code
A technology for image data and secure transmission, applied in the field of wireless communication, can solve the problems of only concerned about the security of bit stream transmission, inapplicability of image services, waste of resources, etc., to reduce decoding delay, meet high-speed transmission, and expand channel advantages. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
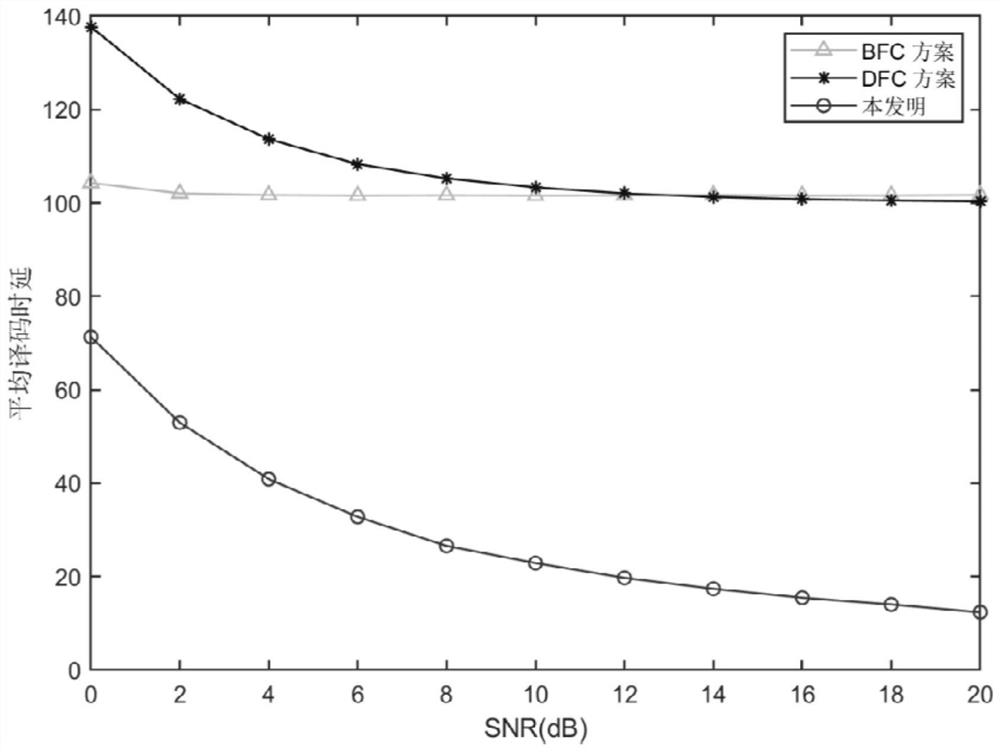
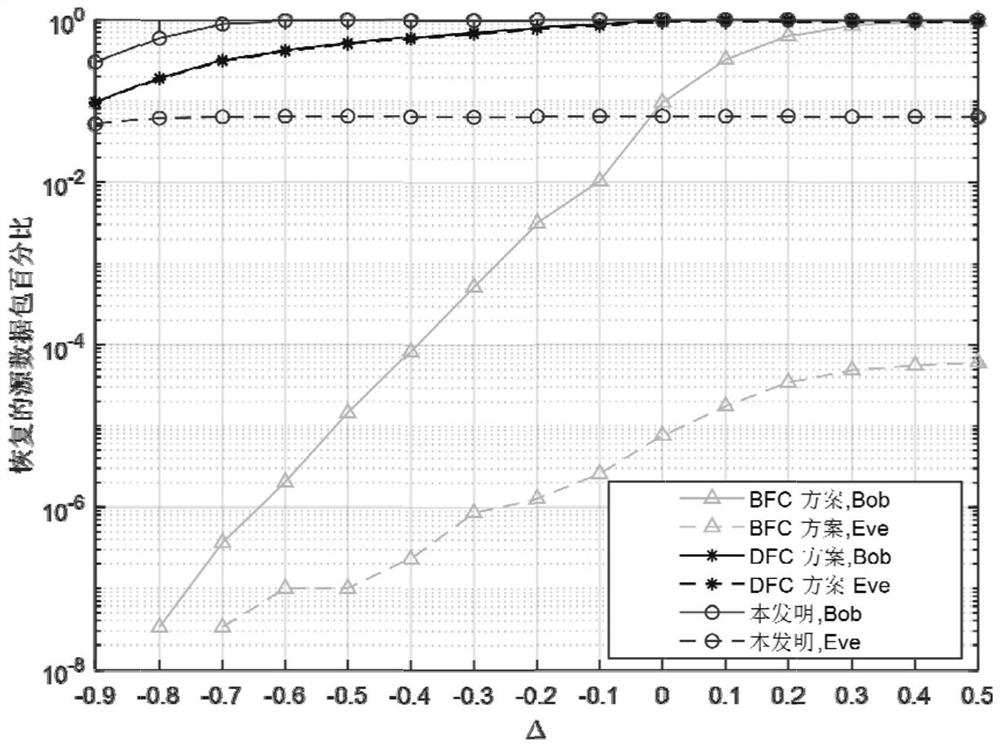
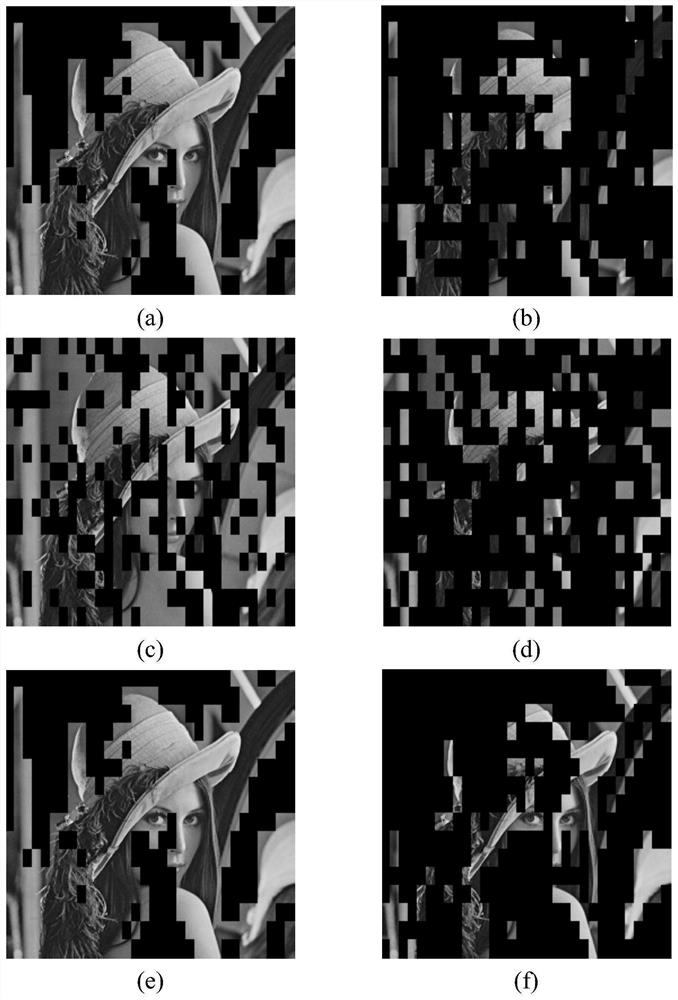
[0029] The purpose and effects of the present invention will become clearer by describing the present invention in detail according to the accompanying drawings and preferred embodiments. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
[0030] Assuming that the system bandwidth is B, the system contains three nodes Alice, Bob and Eve, representing the legal sender, legal receiver and eavesdropper respectively. Assuming that the wireless channel is a block fading channel model, the channel coefficient h ij is a circular symmetric complex Gaussian random variable with mean zero and variance which is where α and d ij represent the path loss exponent and the distance between nodes i and j, respectively. The average transmit power of the transmitter The noise at the receiver is the variance N 0 The additive white Gaussian noise of , the SNR is defined as
[0031] Th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com