Short-message-based authentication method, system and device
An identity verification method and identity verification technology, applied in the field of SMS-based identity verification, can solve the problems of high requirements for memorizing and modifying passwords, complexity, and easy to be forgotten.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
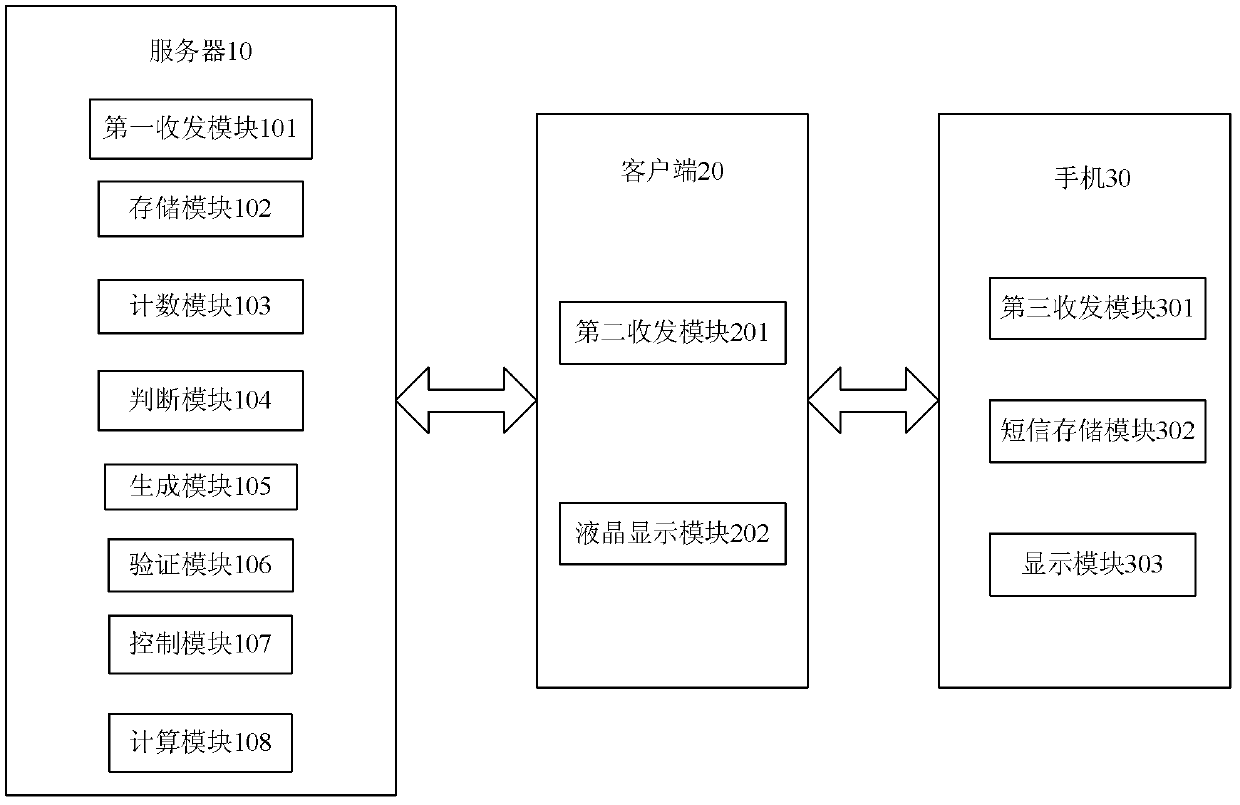
[0075] Embodiment 1 provides an identity verification system based on short messages, including a server 10, a client 20, and a mobile phone 30. The server 10 is equivalent to an identity verification device, wherein,
[0076] The server 10 is used to receive the user login request and user information transmitted by the client 20, to generate a verification code and send it to the user's mobile phone 30, to receive the verification code transmitted by the client 20, and to verify the received verification code Whether it is correct and return the verification result to the client 20;
[0077] The client 20 is used to receive the login request input by the user and send the user information and the login request to the server 10, to receive the verification code input by the user and send it to the server 10 and to receive the verification result returned by the server 10;
[0078] The mobile phone 30 is used to receive the verification code sent by the server 10 and display i...
Embodiment 2
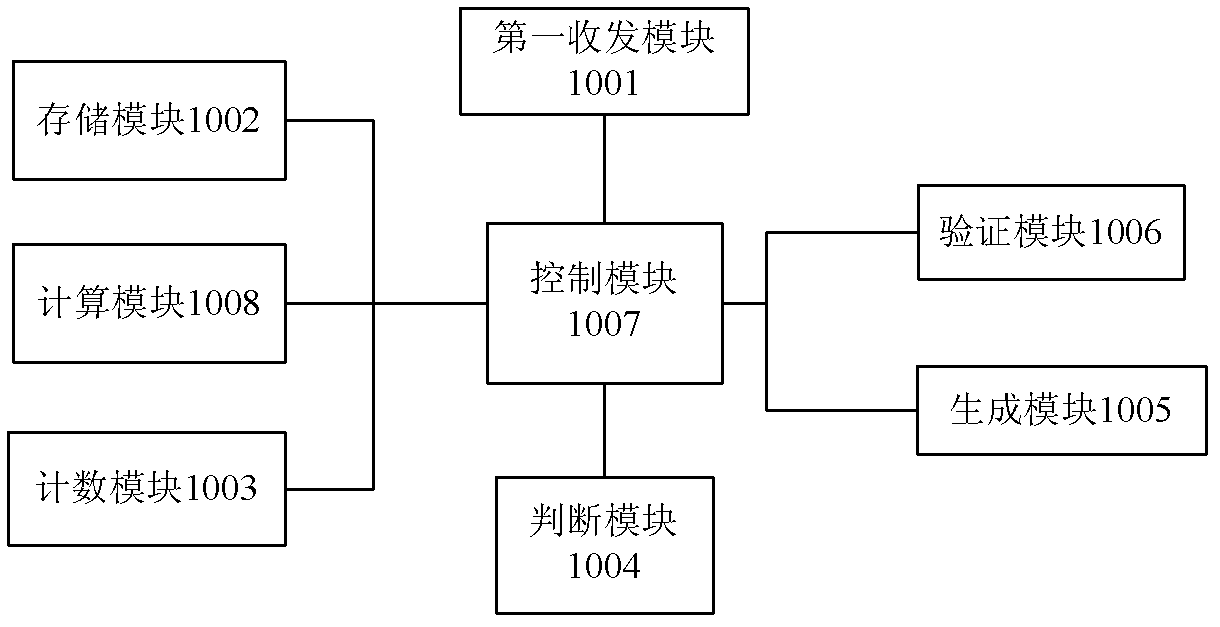
[0101] Such as figure 2 As shown, the present invention proposes a short message-based identity verification device, which includes a first transceiver module 1001, a storage module 1002, a counting module 1003, a judgment module 1004, a generation module 1005, a verification module 1006, a control module 1007 and computing module 1008;
[0102] The first transceiver module 1001 is used to send and receive data transmitted between the client and the server, to receive the verification code transmitted by the generation module 1005 and to send a short message containing the verification code to the mobile phone number bound to the current login request;
[0103] In this embodiment, the first transceiver module 1001 is specifically configured to receive user information, a login request, and a verification code sent by the client and transmit them to the verification module 1006 for returning a corresponding response result to the client.
[0104]The storage module 1002 is use...
Embodiment 3
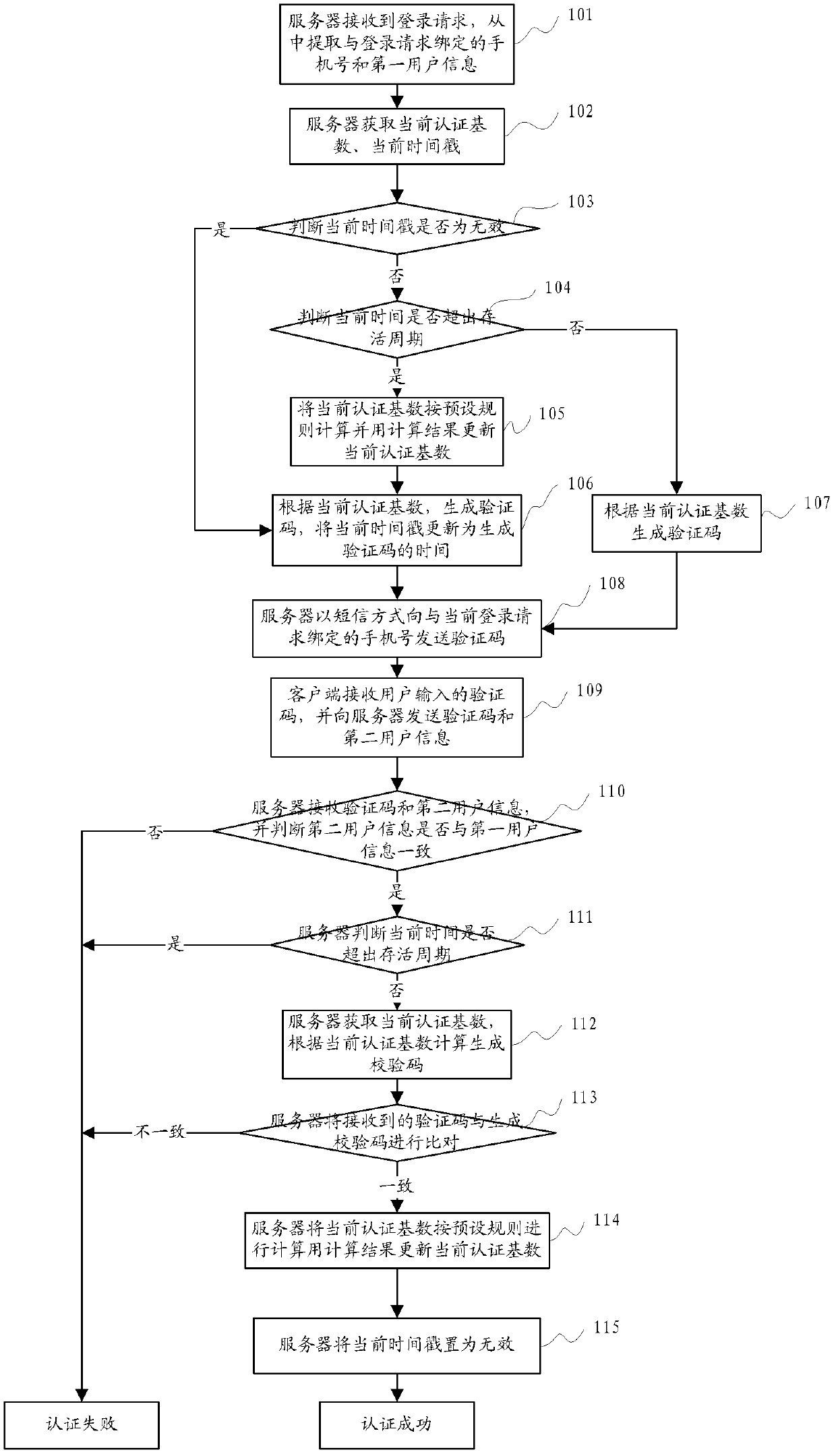
[0116] This embodiment provides a short message-based identity verification method,
[0117] The process for the server to generate the verification code includes the following steps:
[0118] Step S1: the server receives a user login request;
[0119] Step S2: The server judges whether the current timestamp is invalid, if yes, execute step S3, otherwise execute step S4;
[0120] Step S3: the server generates a verification code and updates the current timestamp, and then executes step S5;
[0121] Step S4: The server judges whether the current time exceeds the survival period, if yes, generates a verification code and then executes the next step, otherwise generates a verification code and updates the current timestamp and then executes the next step;
[0122] Step S5: The server sends the verification code to the mobile phone number bound to the user's login request.
[0123] Wherein, the process of verifying the received verification code by the server includes the follo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com