A method and device for sharing encrypted cards in a virtual environment
A virtual environment and encryption card technology, applied in the field of hardware sharing, can solve the problem of wasting encryption card resources and unable to apply for hardware resources, etc., and achieve the effect of improving use efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be described below in conjunction with the accompanying drawings and specific embodiments.
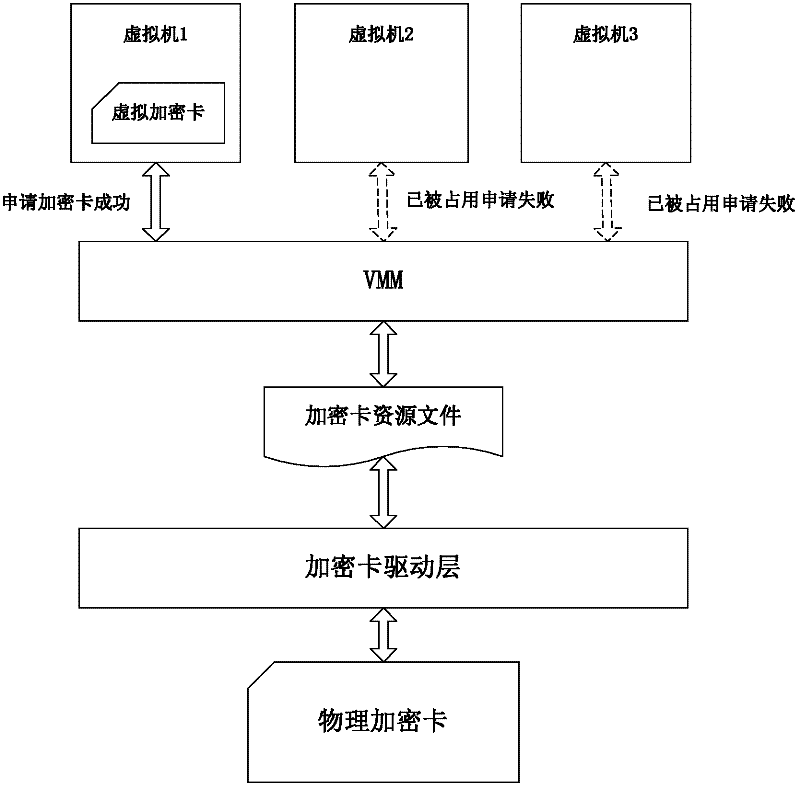
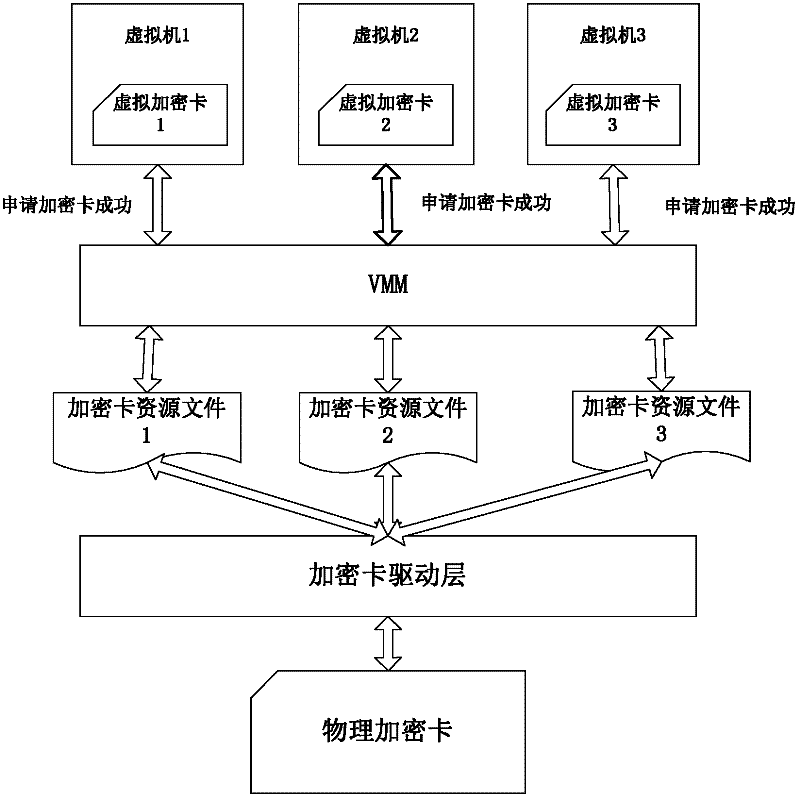
[0029] In order to realize multi-virtual machines sharing the encryption card in the virtual environment, it is necessary to add a resource mapping module and a queue processing module on the basis of the existing common encryption card driver.
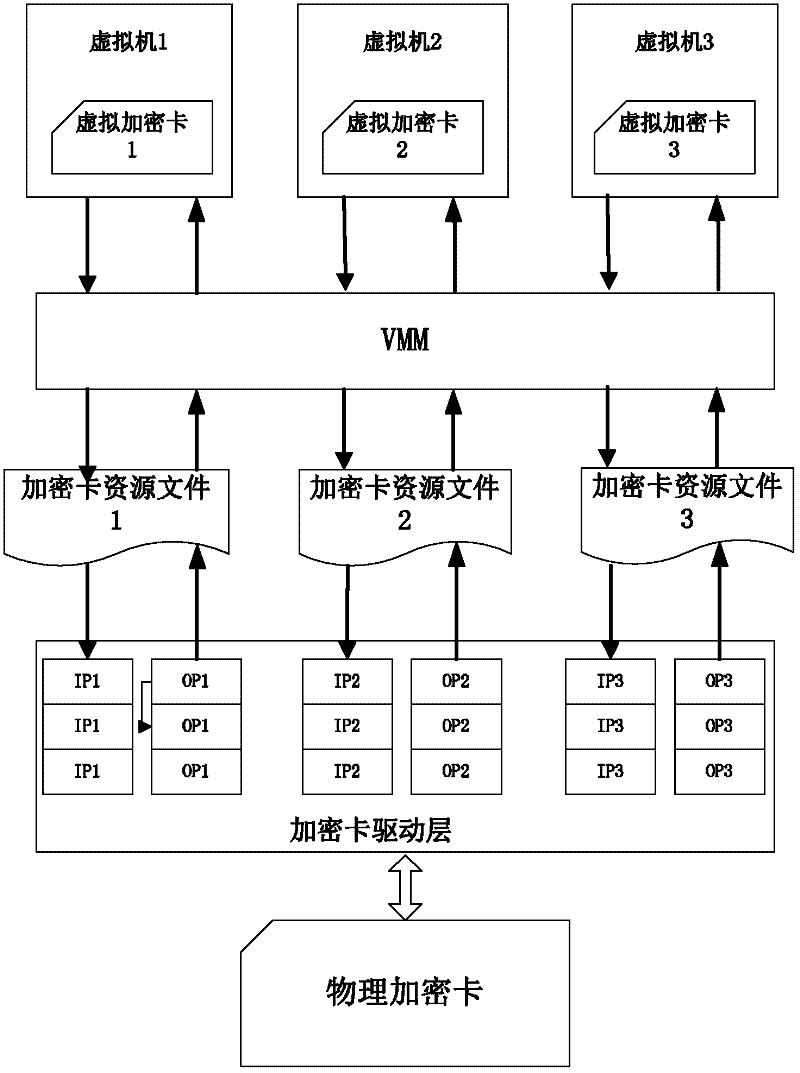
[0030] The main function of the resource mapping module is to map an encryption card hardware into multiple independent encryption card resource files, such as image 3 A physical encryption card shown is mapped to three independent resource files, but each resource file ultimately accesses a physical encryption card. Therefore, requests for different resource files need to be managed within the driver. In order to solve the above problems, the queue management module is introduced.
[0031] The main function of the queue management module is to establish two processing queues for each resource file, one is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com